BOOK THIS SPACE FOR AD
ARTICLE ADEnterprises are embracing on-demand freelance help — but the practice, while growing, opens up entirely new avenues of cyber-risk.
As businesses strive to move faster and faster, many are adopting a “just-in-time” strategy of spinning up human resources on demand – a phenomenon known as the gig economy, familiar to most via Uber, Instacart or DoorDash. But it’s a concept that enterprises are embracing too – inadvertently creating a brand-new insider-threat attack vector that can have dire consequences for data security.
“Your attack surface is changing,” said James Christiansen, vice president of information risk management at Netskope. “Gig-economy workers are typically very short-term workers, they’re coming in and they’re going out, and they’re doing specialty kinds of activities – so they’re different than contract workers. They’re most often going to be using their own laptops and their own collaboration tools, and they’re going to take your data, and perhaps put it in their storage.”
Speaking from the stage this week at the RSA Conference 2021, he encapsulated the problem with the true story of “Bob,” a freelancer who outsourced his own gig.
A Gig Risk Profile: Outsourcing the Outsourced
Bob, an application programmer, was “on call” for various companies to punch up their code when needed. He was doing very well for himself, too, making a six-figure income across the various companies he helped. In fact, he was doing so well that he thought it was entirely reasonable to take some of that income and use it to outsource his own programming role to an organization in China.
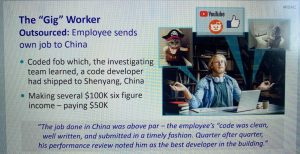
Bob outsourced his own outsourced job. Click to enlarge. Source: Netskope.
“The company had put in two-factor authentication,” Christiansen explained. “So he mailed them his key fob. And they were actually logging in every day, doing his coding. The work was clean and well-written and submitted in a timely fashion; and then around that five o’clock he’d email his update to his management team, and that would be it.”
Clearly, Bob was scamming the system but not intentionally trying to purloin company data. But sharing that code, which could have been proprietary, with an outside entity presents a few different problems. For one, it could be stolen and sold to a competitor; two, sub-freelancer organization could introduce malicious backdoors into the code, unbeknownst to anyone; and three, the lack of visibility into who can access the code means it could end up in an open-source repository somewhere, disallowing a company to recoup its investment and killing a potential competitive advantage.
“If you spent maybe $100,000 in developing a new routine, and someone uploads it to GitHub, it may be used as an open-course tool the very next day,” Christiansen said. “So think about the loss of that investment in your R&D, potentially enabling your competitors to go faster.”
The same risks can be illustrated with other forms of company data, too. For instance, competitive market analysis is a form of research that’s often done by gig workers, Christiansen pointed out. It’s busy work on some levels, but it requires the compilation of sensitive corporate information, such as pricing schedules, discounts, information on channel and supplier relationships, compensation and commission rates, lists of the top salespeople, prospects and customers, request for proposal terms, profit margins and more.
Aside from the potential for breaking the chain of data custody with unauthorized data sharing, other data-security risks associated with gig workers include the ability for them to fall prey to cyberattacks, since they’re often working outside of the company security footprint, he added.
Managing Data Risk in the Gig Economy
The first step in managing gig-economy risk is performing a secondary risk assessment, according to Christiansen.

Click to enlarge. Source: Netskope.
“You’ve probably already done a ‘crown-jewels’ assessment, so you know where the important stuff is,” he explained. “But you need to reassess what would really be critical to the organization in these cases where we may be using freelance help. What can these workers do? Can they copy that code, access pricing data, access marketing data? We want to understand the impact of that data should it leak out, if it’s used for one of our competitors or if it becomes public knowledge.”
Once that risk assessment is completed, organizations can use it to inform the controls they put in place and to develop a protection plan, he added, which should consist of administrative controls, process controls and tech controls:
Administrative Controls: Contractual Approaches Have a Gig-Worker Exit Strategy Process Controls: Monitoring Tech Controls: Zero-Trust TacticsAdministrative Controls: Contractual Approaches
Companies should have clear requirements for gig workers, which can and should be put into a contract. These should cover how workers protect the systems they use to perform the work, any potential liabilities and costs associated with that, restrictions on Bob-like outsourcing, breach-notification requirements, a consent to be monitored – and financial consequences for not adhering to the contract.
“You can require them to have encryption on their laptops and antivirus software and those standard things, and you need to think about who’s going to make sure that gets done,” Christiansen said. “Include any security safeguards you want in place, and specify how they use applications. Can they outsource the work you’ve given to them? It all needs to be specified.”
The contract should also include consequences if gig workers don’t meet security controls. For instance, companies could reserve the right to withhold 10 to 20 percent of their compensation – or not pay at all – if the requirements aren’t in place and carried through.
Christiansen said that breach notification is often a contractual term that gets overlooked, but he noted that it’s critical.
“If for some reason, the sensitive data you have given them is then compromised or shared inappropriately, you need to make sure that they notify you in a timely way because you have an obligation yourself to the organization, customers and others,” he noted.
Administrative Controls: Have a Gig-Worker Exit Strategy
The other part of the administrative equation is the exit strategy – what happens when a gig worker wraps a two-day or two-week long engagement?
“Just like a good marriage, you have to think about how you’re going to break up,” Christiansen explained. “What are your expectations around deleting data, returning data, archiving data and so on? Make sure that exit strategy has been thought through, and they’ve agreed to it, and make sure you follow through on it at the end.”
This also includes of course changing any credentials, switching off profiles for collaboration tools and eliminating access to any back-end systems.
Process Controls: Monitoring
Contracts are nice for legal liability purposes, but the hard part is finding out if the terms have been followed.
The clear answer to this conundrum, according to Christiansen, is monitoring (with the worker’s consent, of course). It’s a typical practice within the enterprise footprint for full-time employees, but it becomes a bit trickier for freelance workers.
“The idea is to look at behavioral activity and record any anomalies,” he explained. “If you see that normally they’re working on certain files, and it’s intensive where because a gig worker is very focused, but suddenly they’re going on- and offline repetitively, that can be because they’re working another gig on their computer and they have to sign off our system. So think about the patterns.”
Monitoring can also be used to watch for application risk – a common issue with gig-economy workers, who may be mixing personal and work activities.
“Are they using applications that may be causing risk? Are they storing data in a place they shouldn’t be storing it? Application instance awareness is absolutely key,” according to Christiansen. “If you’ve got Office 365 or G Suite, you need to be able to see if workers are accessing a business version or personal version. Standard secure web gateways can’t tell the difference. We need to keep it limited to only corporate-approved sites.”
It’s possible too to pop up alerts when a user goes to a rogue destination application, he added – a process he said is an opportunity for coaching.
“I can say, ‘what you’re about to do is high risk,'” he explained. “‘Please enter a justification for doing this.’ And 95 percent of the time, they’ll back out, because they know you’re watching them, and you just educated them on where should be going.”
Technical Controls: Zero-Trust Tactics
The final piece of the puzzle, which can be used in tandem or in place of monitoring efforts, is the application of technology that makes it impossible for data to be shared inappropriately.
“Data protection now must be done in a zero-trust world,” Christiansen said. “We don’t trust where computers are coming from because they’re BYOD; we don’t trust the network because it’s not one we control necessarily; we’re using cloud and it’s running on machines that we don’t own. We’re using SaaS applications. But there are some tactical things we can do for the gig worker or the freelancer.”
For instance, virtual desktop infrastructure (VDI), pioneered by Citrix but now available from a range of vendors, centralizes applications and data on a shared server, which is accessed by thin (or “dumb”) client workstations that aren’t themselves connected to the internet or other resources. There’s no capacity to download files or save anything outside of the enterprise-owned central repository, so workers can’t share data outside of the organization.
“None of the data actually ever goes to that desktop,” Christiansen explained. “So therefore, all of those threats around data being copied off or reused or screenprinted, etc., go away.”
Another alternative is remote browser isolation RBI), which is a similar concept that applies only to actions that take place via a browser.
“It makes a lot of sense because you don’t have to virtualize the whole machine, because they’re working remotely – but I can make sure they can’t take anything out of my G Drive or my SharePoint. I can contain data there, and prevent it from getting outside of that browser to a worker’s underlying desktop.”
A third option to bolster information risk management or information rights management in is to use encrypted files.
“These files require authorization at time of use,” he explained. “I can email it to someone and they can open it if they have the right credentials, but if they email it to somebody else, that person can’t open it. So, it’s not like a file that can be leaked out and get into the wrong hands.”
Overall, the idea is to embrace the bold new gig-economy way of working – but it’s vital to understand the data risks and danger that comes with the territory.
“The gig economy is here to stay, so lean into it, it’s not a fad,” Christiansen concluded. “But that gig-worker route represents a significant threat. So, think about your available security tactics and your overall strategy, and remember that key to any successful security program is understanding your culture, what is acceptable what isn’t acceptable. And remember that we’ve got more data going outside of our organizations these days than what’s being sent around inside.”
Download our exclusive FREE Threatpost Insider eBook, “2021: The Evolution of Ransomware,” to help hone your cyber-defense strategies against this growing scourge. We go beyond the status quo to uncover what’s next for ransomware and the related emerging risks. Get the whole story and DOWNLOAD the eBook now – on us!
.png)
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·