BOOK THIS SPACE FOR AD
ARTICLE AD
The Vanilla Tempest cybercrime gang used INC ransomware for the first time in attacks on the healthcare sector
Pierluigi Paganini
September 20, 2024

Microsoft warns that a financially motivated threat actor is using INC ransomware in attacks aimed at the healthcare sector in the U.S.
Microsoft Threat Intelligence team revealed that a financially motivated threat actor, tracked as Vanilla Tempest (formerly DEV-0832) is using the INC ransomware for the first time to target the U.S. healthcare sector.
Microsoft observed the financially motivated threat actor tracked as Vanilla Tempest using INC ransomware for the first time to target the healthcare sector in the United States. pic.twitter.com/WnnZvGODjV
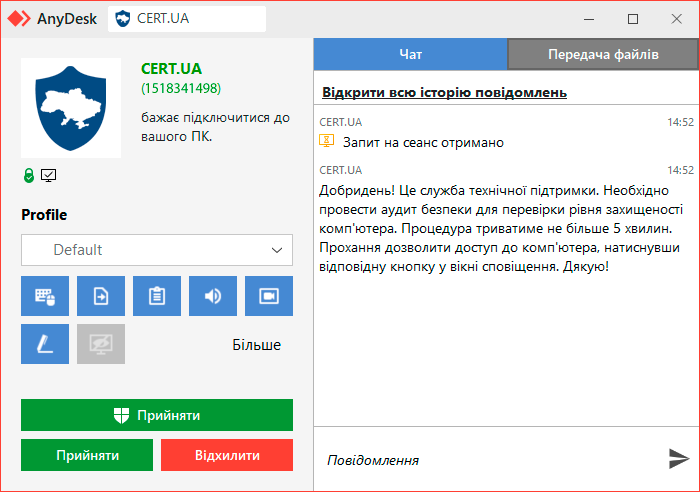
— Microsoft Threat Intelligence (@MsftSecIntel) September 18, 2024“Vanilla Tempest receives hand-offs from Gootloader infections by the threat actor Storm-0494, before deploying tools like the Supper backdoor, the legitimate AnyDesk remote monitoring and management (RMM) tool, and the MEGA data synchronization tool.” Microsoft wrote on X.
Vanilla Tempest has been active since July 2022, it was observed targeting organizations in the education, healthcare, IT, and manufacturing sectors. The group employed various ransomware payloads in its attacks, including BlackCat, Quantum Locker, Zeppelin, and Rhysida.
The threat actor uses Remote Desktop Protocol (RDP) for lateral movement and deploys the INC ransomware payload through the Windows Management Instrumentation Provider Host.
Microsoft Defender for Endpoint detects multiple stages of Vanilla Tempest activity and known INC ransomware and other malware identified in this campaign. For more info and guidance on defending against ransomware, visit https://t.co/Gf44gffDvc.
— Microsoft Threat Intelligence (@MsftSecIntel) September 18, 2024Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, ransomware)
.png)













 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·