BOOK THIS SPACE FOR AD
ARTICLE AD
Ransomware news has been steady this week with new tactics, decryptors, the return of ransomware gangs, and likely the largest single ransomware attack in history conducted Friday afternoon.
Friday afternoon, the REvil ransomware gang used a zero-day vulnerability in the Kaseya VSA management software to encrypt MSPs and their customers worldwide.
While Kaseya states that only 40 MSPs were affected, each MSP could potentially have thousands if not millions of individual business customers, making this the most significant ransomware attack ever conducted.
No information about the VSA vulnerability has been released at this time. However, our detailed article about REvil's attack on Kaseya included detailed information regarding how REvil conducted the attack, including IOCs.
One of the first businesses reporting they were affected by the attack is Coop, one of the largest supermarket chains in Sweden.
This week's other news of interest is the return of the Babuk ransomware operation, which previously shut down after publishing the stolen data of Washington DC's Metropolitan Police Department.
We also saw an older version of the Babuk Ransomware build leaked online and used by other threat actors to perform their own cyberattacks.
Finally, a sample of the new REvil Linux encryptor used to encrypt ESXi virtual machines was found, TrickBot is using a new Diavol ransomware, CISA released a new ransomware self-assessment tool, and a decryptor for Lorenz was released.
Contributors and those who provided new ransomware information and stories this week include: @malwareforme, @struppigel, @fwosar, @DanielGallagher, @serghei, @Ionut_Ilascu, @jorntvdw, @demonslay335, @malwrhunterteam, @Seifreed, @FourOctets, @PolarToffee, @VK_Intel, @BleepinComputer, @LawrenceAbrams, @Accenture_US, @Intel_by_KELA, @y_advintel, @Tesorion_NL, @CISAgov, @fbgwls245, @pcrisk, @GossiTheDog, @ido_cohen2, @GroupIB_GIB, @Fortinet, @_johnhammond, @markloman, and @ESETresearch.
June 26th 2021
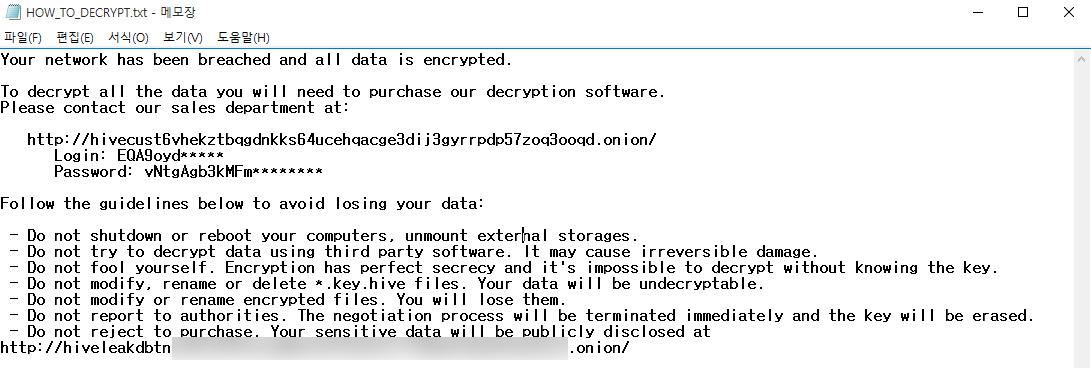
New Hive Ransomware
dnwls0719 found a sample of the Hive Ransomware that appends the .hive extension to encrypted files.
June 27th 2021
Babuk ransomware builder leaked
Kevin Beaumont found that the ransomware builder for the Babuk Ransomware was uploaded to VirusTotal.
June 28th 2021
Ransomware gangs now creating websites to recruit affiliates
Ever since two prominent Russian-speaking cybercrime forums banned ransomware-related topics criminal operations have been forced to promote their service through alternative methods.
REvil ransomware's new Linux encryptor targets ESXi virtual machines
The REvil ransomware operation is now using a Linux encryptor that targets and encrypts Vmware ESXi virtual machines.
June 29th 2021
HADES ransomware operators continue attacks
Accenture Security assesses with a moderate-to-high level of confidence that a previously reported unknown threat group is now using multiple ransomware variants in cybercrime operations that have impacted at least seven (7) victims.
Lorenz ransomware decryptor recovers victims' files for free
Dutch cybersecurity firm Tesorion has released a free decryptor for the Lorenz ransomware, allowing victims to recover some of their files for free without paying a ransom.
New STOP Djvu ransomware variants
PCrisk found new STOP Djvu ransomware variants that append the .miis, .neer, and .leex extension.
June 30th 2021
CISA releases new ransomware self-assessment security audit tool
The US Cybersecurity and Infrastructure Security Agency (CISA) has released the Ransomware Readiness Assessment (RRA), a new module for its Cyber Security Evaluation Tool (CSET).
Leaked Babuk Locker ransomware builder used in new attacks
A leaked tool used by the Babuk Locker operation to create custom ransomware executables is now being used by another threat actor in a very active campaign targeting victims worldwide.
REvil Twins: Deep Dive into Prolific RaaS Affiliates' TTPs
In this blog post, we would like to focus on one of the most active ransomware collectives, REvil, and their RaaS program, which attracts more and more affiliates due to the shutdown of other RaaS. Group-IB's DFIR experts took a deep dive into the modus operandi of REvil affiliates and shared some information on various affiliates' tactics, techniques and procedures observed, so defenders can tune their detection capabilities accordingly.
July 1st 2021
Trickbot cybercrime group linked to new Diavol ransomware
FortiGuard Labs security researchers have linked a new ransomware strain dubbed Diavol to Wizard Spider, the cybercrime group behind the Trickbot botnet.
Babuk ransomware is back, uses new version on corporate networks
After announcing their exit from the ransomware business in favor of data theft extortion, the Babuk gang appears to have slipped back into their old habit of encrypting corporate networks.
Babuk Ransomware, if you Hit and Run do not leave a trace
On the Server, we saw a weird directory that we start to check, after the scan we were able to see that the website onion is full with Active Chat sessions. In the active session, we can view all conversations between the Babuk ransomware group and the victims. the sessions basically get you inside the “Chat Conversation Page” with all the History chats. that gives us an inside look into the negotiations process.
July 2nd 2021
US insurance giant AJG reports data breach after ransomware attack
Arthur J. Gallagher (AJG), a US-based global insurance brokerage and risk management firm, is mailing breach notification letters to potentially impacted individuals following a ransomware attack that hit its systems in late September.
REvil ransomware hits 200 companies in MSP supply-chain attack
A massive REvil ransomware attack affects multiple managed service providers and their clients through a reported Kaseya supply-chain attack.
ESET shares list of targeted countries in Kaseya attack
ESETresearch telemetry shows majority of reports of Win32/Filecoder.Sodinokibi.N (REvil) coming from
.png)














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·