BOOK THIS SPACE FOR AD
ARTICLE ADThousands of Industrial Control Systems in the US and UK are vulnerable to cyberattacks, putting critical infrastructure like water systems at risk. A new report from Censys reveals the alarming number of exposed devices, highlighting the urgent need for improved cybersecurity measures
A new report from cybersecurity firm Censys has spotlighted the alarming vulnerabilities facing ICS (Industrial Control Systems) in both the United States and the United Kingdom. The findings, part 1 of Censys’ 2024 State of the Internet Report, emphasise on the ease with which malicious threat actors could potentially disrupt essential services like water supply and power generation.
The report reveals that over 40,000 ICS devices in the U.S. are connected to the public internet. More concerning is that 18,000 of these devices, excluding those related to building control protocols, are directly involved in managing industrial systems, making them lucrative targets for cybercriminals.
In comparison, the U.K. has around 1,500 exposed control systems, with an additional 1,700 publicly accessible HTTP devices linked to 26 different operational technology (OT) vendors. Many of these devices likely still operate on default credentials, creating an easy entry point for attackers.
A particularly concerning finding is the vulnerability of Water and Wastewater Systems (WWS). Nearly half of the HMIs (Human-Machine Interfaces) associated with these systems were found to be manipulable without any authentication, making them sitting ducks for cybercriminals.
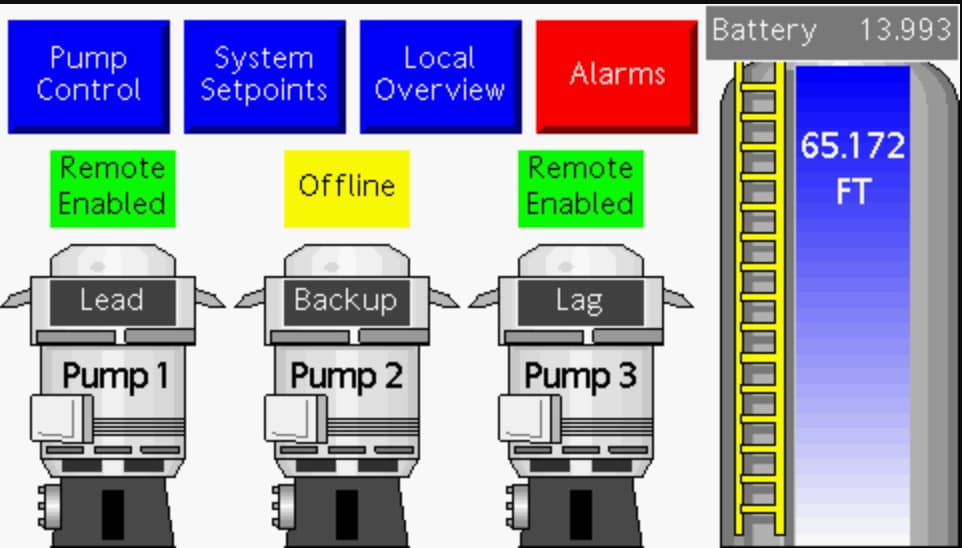 The screenshot shared by Censys shows the HMI interface for a three-pump system, displaying options for viewing alarms, controls, and system setpoints.
The screenshot shared by Censys shows the HMI interface for a three-pump system, displaying options for viewing alarms, controls, and system setpoints.The report also highlights the difficulty in notifying owners of exposed devices, as many are hosted on cellular networks or commercial ISPs like Verizon and Comcast in the US, making it impossible to identify the responsible organization or sector.
The report’s findings come at a time when cyberattacks on critical infrastructure are becoming increasingly common. Recent attacks (including the one in December 2023) have seen Iranian hackers from Cyber Av3ngers group targeting Israeli-manufactured devices and Russian groups disrupting water supplies in Texas in April 2024.
Brad Brooks, CEO of Censys, emphasized the urgent need for increased awareness and action. “It is imperative that we shed light on the exposure of ICS as they are essential to our critical infrastructure across the globe,” said Brooks. “The goal for our research was to not only discover the exposed devices but to notify device owners of their improper exposure.”
Nonetheless, Censys’ report calls for a collaborative effort to address the vulnerabilities identified. This includes working with device manufacturers to implement stronger security measures, improving communication channels to enable rapid notification of exposed devices, and raising awareness among operators of the importance of robust cybersecurity practices.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·