BOOK THIS SPACE FOR AD
ARTICLE AD
This is a beginner level LFI challenge.
LFI is local file inclusion. It is a web vulnerability which is caused by the mistakes made by the programmer of the website. LFI attack may lead to the important information disclosure , remote code execution and even cross site scripting(XSS). An attacker can disclose the users and passwords of the vulnerable website . LFI occurs when an application uses the path to a file as input. If the application treats this input as trusted, a local file may be used in the include statement.
Even without the ability to upload and execute code, a Local File Inclusion vulnerability can be dangerous. An attacker can still perform a Directory Traversal / Path Traversal attack using an LFI vulnerability as follows.
http://example.com/?file=../../../etc/passwd
Deploy the machine.
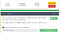
Lets find out what services are running on the machine using nmap tool.
-sS: This option is used for service scanning. (s for scan, S for Service)
-sV: This option is used for version scanning. (s for scan, V for Version)
We can combine these options and use as -sSV followed by IP address of the machine.

We found that http service is running on port number 80. HTTP service means a web application is running on port 80.
So, we will open our browser and go to IP_address_of_machine:80
A website will open as shown below.
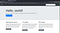
Since, we are doing LFI challenge so click on view details under LFI-attack. The complete details will open as shown below. Read the complete paragraph carefully. Look at the URL of the page (IP_address/article?name=lfiattack). We can perform lif attack on name parameter.
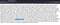
The first and most basic LFI attack is finding the users and passwords which can be done by setting parameter’s value as /etc/passwd or ../etc/passwd or ../../etc/passwd or ../../../etc/passwd and so on until you get the users and passwords as shown below.
We found that a user named as falconfeast exists and the password of the user is rootpassword.
In a linux file system user.txt file exists at the location /home/user_name/user.txt and root.txt file exist at /root/root.txt. Since we got the users and passwords very easily by performing LFI attack we can also read the user.txt and root.txt files easily by following the same approach that was used in finding passwords.
Set parameter’s value as ../../../../home/falconfeast/user.txt to read user flag. And,
Set parameter’s value as ../../../../root/root.txt to read root flag.

Submit the flags and complete the room.
H4PPY H4K1NG :)
Thank You !!!
.png)
 4 years ago
283
4 years ago
283 














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·