BOOK THIS SPACE FOR AD
ARTICLE ADInvestigating “strings” within an application and why these values are important!
Room link: https://tryhackme.com/room/malstrings
Note: This room is for Premium Members Only. who purchased THM premium membership.
Motivation:
What you will learn after completing this Room:
String analysisOSINTStatic Analysis(Part of Malware Analysis)
What are “strings”?
> From a programming perspective, “strings” is the term given for data handled by an application. At a broader view, these pieces of data are used to store information such as text to numerical values.For example, let’s say we have an application such as a calculator. A user will have to input two numerical values (e.g. 1 and 5) combined with an operator (e.g. + or plus) addition in this case. These values will be stored as “strings”.However “strings” can be stored within the application itself — where no input is necessary from the user. For example, using the example of usernames and passwords is a great representation of the many types of information that may be stored as a “string”.Why are “strings” important?
We’re all security-minded people here and know that writing down passwords isn’t a very smart thing to do. However, developers are not quite so likeminded and often leave credentials in applications which are often essential i.e. An application that server needs to know the IP address of it. Arguably, an IP address is trivial in comparison to the sensitivity of a password — but both would be stored as strings.There are a plethora of examples of companies storing sensitive information such as passwords within their applications. For example, Intellian, a satellite-communications focused company had the disclosure of their “Aptus Web 1.24” application retaining a default passcode of “12345678”.Illustrated below is an example of an Android Application containing sensitive credentials within strings:Task 1:

Answer: intellian
I searched this product name on google and found it’s default username and password.
Reference:
2. What is the CVE entry disclosed by the company “Teradata” in their “Viewpoint” Application that has a password within a string?
Answer: CVE-2019–6499

Reference:
3. According to OWASP’s list of “Top Ten IoT” vulnerabilities, name the ranking this vulnerability would fall within, represented as text.
Answer: 1
As this is an IOT device so I quickly searched on google and found that weak, hardcoded category is on 1st number.
Reference:
[Task 2] Practical: Extracting “strings” From an Application
#1 What is the correct username required by the “LoginForm”?
Answer: for this question I used string utility that are inbuilt in the kali linux.

I extracted strings from LoginFrom.exe.

From the extracted strings I found some sensitive information.
Ans: cmnatic
#2 What is the required password to authenticate with?
Answer: from the above screenshot we can see that in the second line we have the password that is:
TryHackMeMerchWhen
#3 What is the “hidden” THM{} flag?
Answer: From above screenshot, we can see the flag for this task.
THM{Not_So_Hidden_Flag}
[Task 3] Strings in the Context of Malware
#1 What is the key term to describe a server that Botnets receive instructions from?
Answer: Command and Control
#2 Name the discussed example malware that uses “strings” to store the bitcoin wallet addresses for payment
Answer: Wannacry
[Task 4] Practical: Finding Bitcoin Addresses in Ransomware (Deploy!)
#1 List the number of total transactions that the Bitcoin wallet used by the “Wannacry” author(s)
Answer: for this question THM already give us hint in description of this task.
we have a bitcoin address of the wannacry author.
On the bottom side, we can see that this author did 140 transactions from this wallet.
Answer: 140
#2 What is the Bitcoin Address stored within “ComplexCalculator.exe”
Answer: for this question, we have to deploy thm instance to connect.
you can use Remote Desktop Connection utility provides in the Windows operating systems.
Linux users follow the below blog to install rdesktop utility to connect to the remote desktop machine.
Now connect to the remote machine.
We have given credentials for login.
Username: analysis
Password: tryhackme
Now after login on desktop we have Sysinternals folder open it, then open cmd in that folder.
now type -> strings.exe ComplexCalculatorv2.exe > strings.txt
Let’s breakdown this command.
Strings.exe is our tool executable file.
ComplexCalculatorv2.exe is our target file.
> operator will work as a pipeline here.
Strings.txt is our output file,
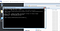
Now open Strings.txt in Notepad.
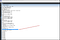
From outfile I got the bitcoin address. that is stored in calculator application.
Answer: 1LVB65imeojrgC3JPZGBwWhK1BdVZ2vYNC
Reference:
Best Books to learn Malware Analysis:
https://www.amazon.in/Practical-Malware-Analysis-Hands-Dissecting/dp/1593272901
Courses:
Author: Mayur Parmar (th3cyb3rc0p)
Follow me on Twitter & LinkedIn( mostly I will share tips on these social media platforms)
https://twitter.com/th3cyb3rc0p?lang=en
https://in.linkedin.com/in/th3cyb3rc0p
.png)
 4 years ago
372
4 years ago
372 














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·