BOOK THIS SPACE FOR AD
ARTICLE AD
Cloud communications company Twilio has now disclosed that it was impacted by the recent Codecov supply-chain attack in a small capacity.
As reported by BleepingComputer last month, popular code coverage tool Codecov had been a victim of a supply-chain attack that lasted for two months.
During this two-month period, threat actors had modified the legitimate Codecov Bash Uploader tool to exfiltrate environment variables (containing sensitive information such as keys, tokens, and credentials) from Codecov customers' CI/CD environments.
Using the credentials harvested from the tampered Bash Uploader, Codecov attackers reportedly breached hundreds of customer networks.
Twilio: small number of customer email addresses exposed
Today, cloud communications and VoIP platform Twilio has announced that it was impacted by the Codecov supply-chain attack.
Shortly after Codecov had disclosed the security incident concerning its Bash Uploader last month, Twilio was notified that they were impacted too.
As seen by BleepingComputer, multiple Twilio projects used and continue to use the Codecov Bash Uploader that had earlier been modified:
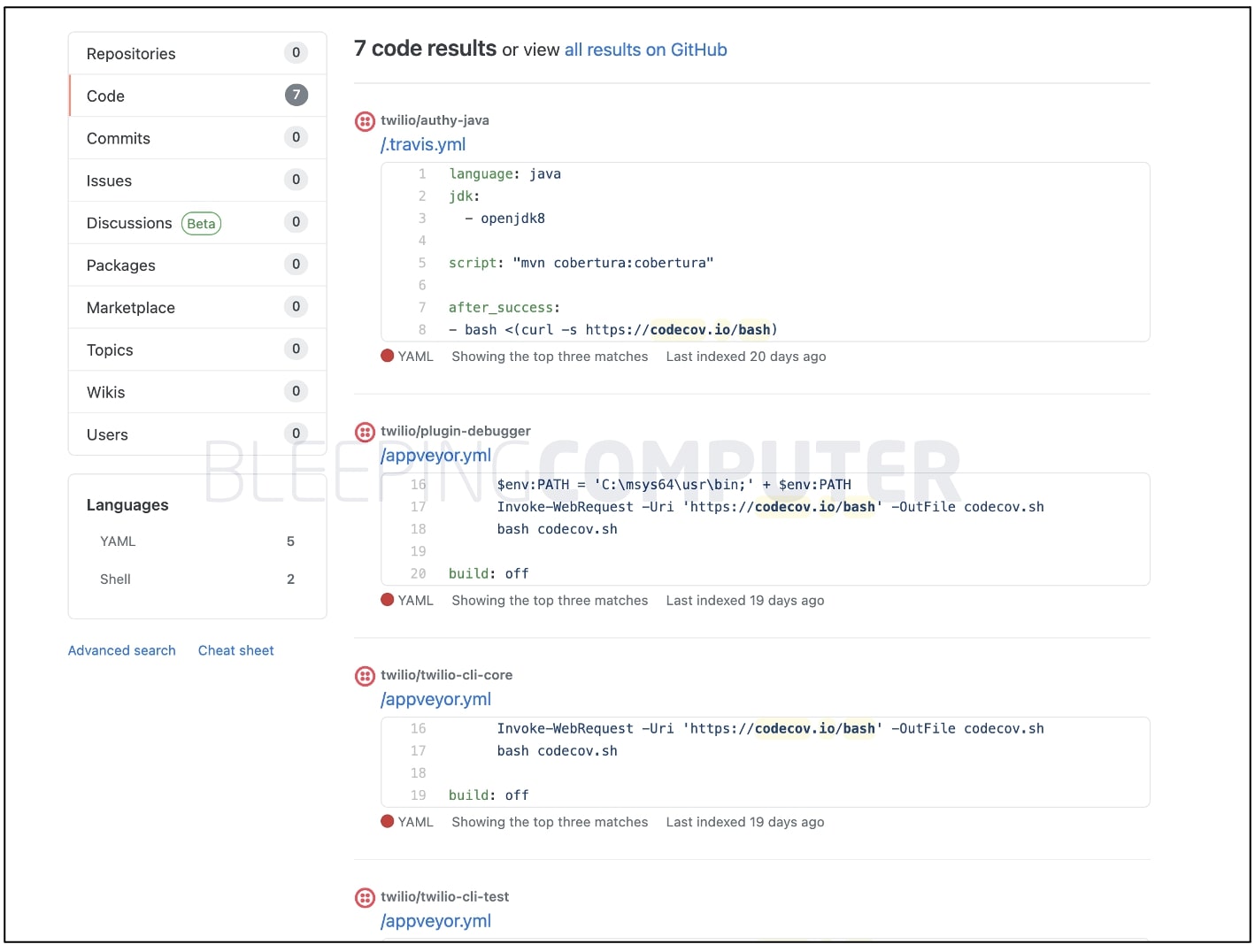 Codecov Bash Uploader in use by multiple Twilio projects
Codecov Bash Uploader in use by multiple Twilio projectsSource: BleepingComputer
But Twilio states, the illicitly altered Bash Uploader component was being actively used in a small number of Twilio's projects and CI pipelines, and did not concern critical systems.
"These projects and CI pipelines are not in the critical path to providing updates or functionality to our communication APIs," explained Twilio in a statement released today.
"Our subsequent investigation into the impact of this event found that a small number of email addresses had likely been exfiltrated by an unknown attacker as a result of this exposure."
"We have notified those impacted individuals privately and have remediated the additional potential exposure by thoroughly reviewing and rotating any potentially exposed credentials," continues the statement.
Email addresses found in GitHub repository
On April 22nd, GitHub had also notified Twilio after detecting suspicious activity related to Codecov exposure, and that specifically a Twilio user token had been exposed.
"GitHub.com had identified a set of GitHub repositories that had been cloned by the attacker in the time before we were notified by Codecov."
"Our investigation turned from identifying secrets to identifying the content of the repositories that were cloned," says Twilio.
It was then in one such GitHub repository that Twilio's security team found "a small number of email addresses belonging to Twilio customers," although the company has not disclosed what exactly this "small number" is.
Twilio states that at this time there is no indication or evidence of any other customer data having been exposed, or that Twilio's repositories were altered by the attackers in any manner.
As a part of its investigation activities, the company has additionally conducted an automated search for finding any exposed secrets and manually analyzed the findings.
Further, the company has rotated all secrets that could have been possibly exposed in the repositories, as a result of the Codecov supply-chain attack.
Twilio has also taken steps to detect such incidents in the future, such as scanning GitHub pull requests in real-time to spot any exposed secrets and common insecure coding practices.
Twilio not the only company to be impacted
Twilio is not the first or the only company to be impacted by the Codecov supply-chain attack.
Last month, as reported by BleepingComputer, HashiCorp had disclosed that their GPG private key had been exposed in the attack.
This key had been used for signing and verifying software releases, and therefore had to be rotated.
Since then, several other Codecov clients have had to rotate their credentials. Whether or not they have been impacted, and in what capacity, remains a mystery.
Prior to the breach having been spotted by Codecov, the Bash Uploader was in use by thousands of open-source projects:
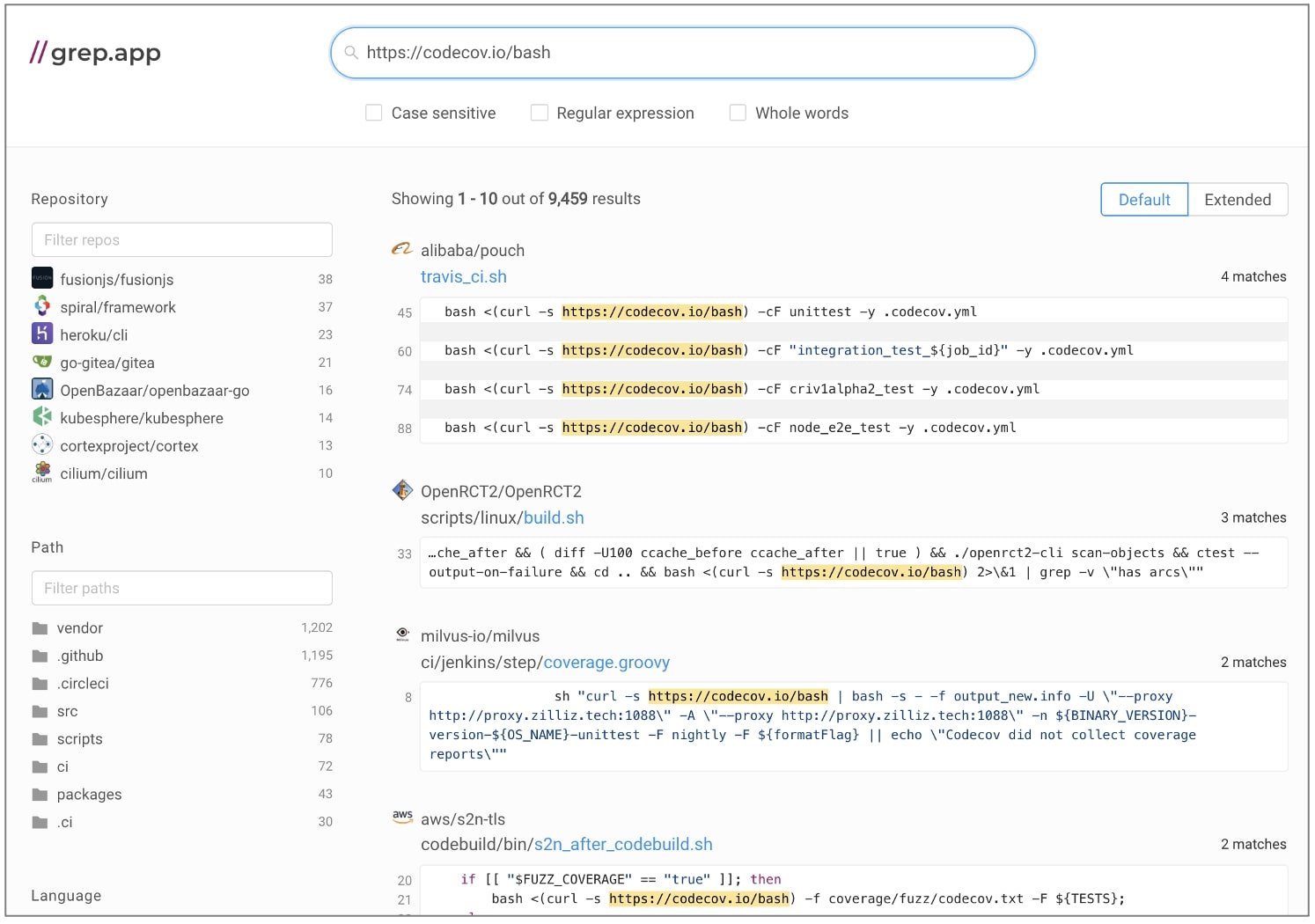 Thousands of repositories using Codecov Bash Uploader
Thousands of repositories using Codecov Bash UploaderSource: grep.app
Similarly, BleepingComputer also came across a discussion among Mozilla Firefox community members who acknowledged rotating secrets following the Codecov attack.
We did rotate all secrets last week already.
This is a _new_ email, saying there’s new information after login.
Except when I login there’s nothing.
(The blog post is updated and has Indicators of Compromise)
Mozilla responded to us with:
"In response to Codecov's breach which was announced on April 15, 2021, Mozilla's security team coordinated the rotation of credentials and tokens pursuant to the guidance of Codecov."
"No evidence of compromise was detected, and we don’t expect any impacts to Mozilla's products or services," a spokesperson for Mozilla told BleepingComputer.
Last week, Codecov began sending additional notifications to the impacted customers and disclosed a thorough list of Indicators of Compromise (IOCs), i.e. attacker IP addresses associated with this supply-chain attack.
Codecov users should scan their CI/CD environments and networks for any signs of compromise, and as a safeguard, rotate any and all secrets that may have been potentially exposed.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·