Twitter is officially beginning to roll out support for encrypted direct messages (DMs) on the platform, more than five months after its chief executive Elon Musk confirmed plans for the feature in November 2022.
The "Phase 1" of the initiative will appear as separate conversations alongside existing direct messages on users' inboxes. Encrypted chats carry a lock icon badge to visually differentiate them.
That said, the opt-in feature is currently limited to verified users or affiliates to a verified organization. It's also essential both the sender and recipient are on the latest versions of the Twitter apps across Android, iOS, and desktop web.
Another criteria to send and receive encrypted messages is that the recipient must follow the sender, has sent a message to the sender in the past, or has accepted a direct message request from the sender at some point.
While Twitter did not disclose the exact method it uses to secure the conversations, the company said it employs a "combination of strong cryptographic schemes" to encrypt users' messages, links, and reactions.
It further emphasized that the encrypted chat contents remain encrypted while stored on its infrastructure and only decrypted at the receiver's end. The implementation is expected to be open sourced later this year.
That said, the work-in-progress nature of the project also means that it does not support encrypted group conversations or allow exchanging media and other file attachments. Some other notable restrictions are as follows -
Users can only register a maximum of up to 10 devices to send and receive encrypted messages. New devices (where the Twitter app is re-installed) cannot partake in existing encrypted conversations Logging out from Twitter will calls all messages including encrypted DMs to be deleted from the current deviceIt also said the current architecture does not "offer protections against man-in-the-middle attacks" and that it does not guarantee forward secrecy, a crucial security measure that ensures that a compromise of a single session key will not impact data shared in other sessions.
"If the private key of a registered device was compromised, an attacker would be able to decrypt all of the encrypted messages that were sent and received by that device," Twitter said, adding it doesn't plan to remediate the limitation keeping larger user experience in mind.
Found this article interesting? Follow us on Twitter and LinkedIn to read more exclusive content we post.
.png)
 1 year ago
78
1 year ago
78 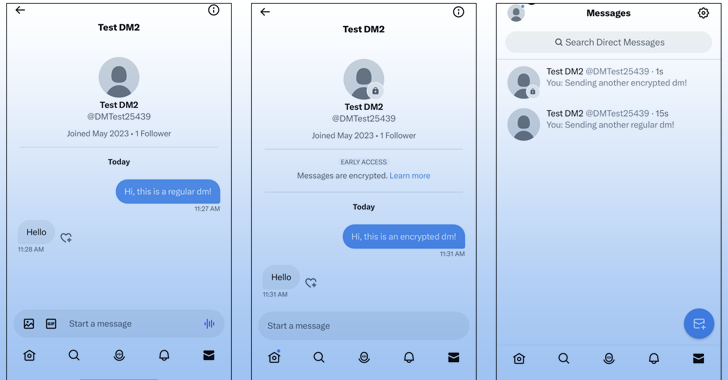
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·