BOOK THIS SPACE FOR AD
ARTICLE ADU.S. agencies must implement vulnerability-disclosure policies by March 2021, according to a new CISA mandate.
The U.S. government’s cybersecurity agency is now requiring federal agencies to implement vulnerability-disclosure policies (VDPs), which would give ethical hackers clear guidelines for submitting bugs found in government systems, by next March.
Currently, most federal agencies lack a formal mechanism to receive information from white-hat hackers about potential security vulnerabilities on their systems. The new directive by the Cybersecurity and Infrastructure Security Agency (CISA) aims to change this by requiring agencies to publish policies with detailed descriptions of which systems are in scope, the types of testing that are allowed and how ethical hackers can submit vulnerability reports. A directive is a compulsory direction for federal, executive branch, departments and agencies.
“When agencies integrate vulnerability reporting into their existing cybersecurity risk management activities, they can weigh and address a wider array of concerns,” according to the CISA directive, released Wednesday. “This helps safeguard the information the public has entrusted to the government and gives federal cybersecurity teams more data to protect their agencies. Additionally, ensuring consistent policies across the executive branch offers those who report vulnerabilities equivalent protection and a more uniform experience.”
The policies would cover all internet-accessible systems or services in government agencies – including systems that were not intentionally made internet-accessible, according to CISA.
The directive mandates that organizations implement VDPs with clear wording around which systems are in-scope, as well as assurances around good-faith security research. VDPs must also clearly identify the mechanism through which researchers can report flaws to agencies, and provide “timely” feedback on vulnerabilities reported.
And, “to streamline communication and collaboration, Federal agencies shall ensure vulnerability reports are available to system owners within 48 hours of submission, and shall establish a channel for system owners to communicate with vulnerability reporters, as appropriate,” according to a memorandum sent to heads of executive departments and agencies.
Today we issued a directive that requires federal civilian agencies in the executive branch to publish a #vulnerability disclosure policy. This will ensure people know how to report a problem if they find one. Learn more: https://t.co/5RsjPvyCOO. #InfoSec (1/3) pic.twitter.com/tPXXShmfRD
— Cybersecurity and Infrastructure Security Agency (@CISAgov) September 2, 2020
The directive first debuted in December 2019 as a draft open to public comment. Bryan Ware, assistant director of CISA, said that the agency received more than 200 recommendations from more than 40 security researchers, academics, federal agencies, technology companies, civil society and members of Congress.
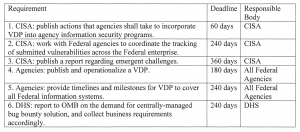 As next steps, in 60 days CISA will publish further guidance regarding implementation, which will break down actions that agencies should take to incorporate VDP into their information-security programs in an effective, standardized, responsible and tailored manner. And, within 180 days all agencies must publish and operationalize their VDP.
As next steps, in 60 days CISA will publish further guidance regarding implementation, which will break down actions that agencies should take to incorporate VDP into their information-security programs in an effective, standardized, responsible and tailored manner. And, within 180 days all agencies must publish and operationalize their VDP.
Finally, in 240 days agencies must report “milestones for VDP to cover all federal information systems” and CISA must begin coordinating ways to track reported bugs.
As part of the directive, CISA will offer a vulnerability-disclosure program service next spring. “We expect this will ease operations at agencies, diminish their reporting burden under this directive, and enhance discoverability for vulnerability reporters,” according to CISA.
On Wed Sept. 16 @ 2 PM ET: Learn the secrets to running a successful Bug Bounty Program. Register today for this FREE Threatpost webinar “Five Essentials for Running a Successful Bug Bounty Program“. Hear from top Bug Bounty Program experts how to juggle public versus private programs and how to navigate the tricky terrain of managing Bug Hunters, disclosure policies and budgets. Join us Wednesday Sept. 16, 2-3 PM ET for this LIVE webinar.
.png)
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·