BOOK THIS SPACE FOR AD
ARTICLE ADLondon Police can’t say if they nabbed the 17-year-old suspected mastermind & multimillionaire – but researchers say they’ve been tracking an Oxford teen since mid-2021.
City of London Police have arrested seven people suspected of being connected to the Lapsus$ gang.
The bust came within hours of Bloomberg having published a report about a teenage boy living at his mother’s house near Oxford, England who’s suspected of being the Lapsus$ mastermind.
The police haven’t verified whether or not they nabbed the Oxford teen, per se.
At any rate, given that he’s a minor, it would be illegal to identify him: According to security journalist Brian Krebs, the teen is 17, though the BBC pegs his age at 16.
But for what it’s worth, all of the suspects are young. In a statement given to TechCrunch, the City of London Police said the seven are between 16 and 21: “The City of London Police has been conducting an investigation with its partners into members of a hacking group,” according to Detective Inspector Michael O’Sullivan. “Seven people between the ages of 16 and 21 have been arrested in connection with this investigation and have all been released under investigation. Our enquiries remain ongoing.”
Investigators reportedly told Bloomberg that another member of Lapsus$ is suspected to be a teenager residing in Brazil. There could well be more: Another investigator told the outlet that security researchers have identified seven unique accounts associated with Lapsus$, “indicating that there are likely others involved in the group’s operations.”
Busy Beavers
Over the past few months, Lapsus$ – a data extortion group – has targeted Brazil’s Ministry of Health and the gaming giant Ubisoft, crippled the Portuguese media kingpin Impresa, and, in recent weeks, eviscerated tech giants including Samsung, Nvidia, Microsoft and Okta.
Allison Nixon, chief research officer at Unit 221B, is one of the researchers who’ve been tracking the Oxford teen, who, researchers say, goes by the online aliases “White,” “Breachbase” or “Oklaqq,” among other names
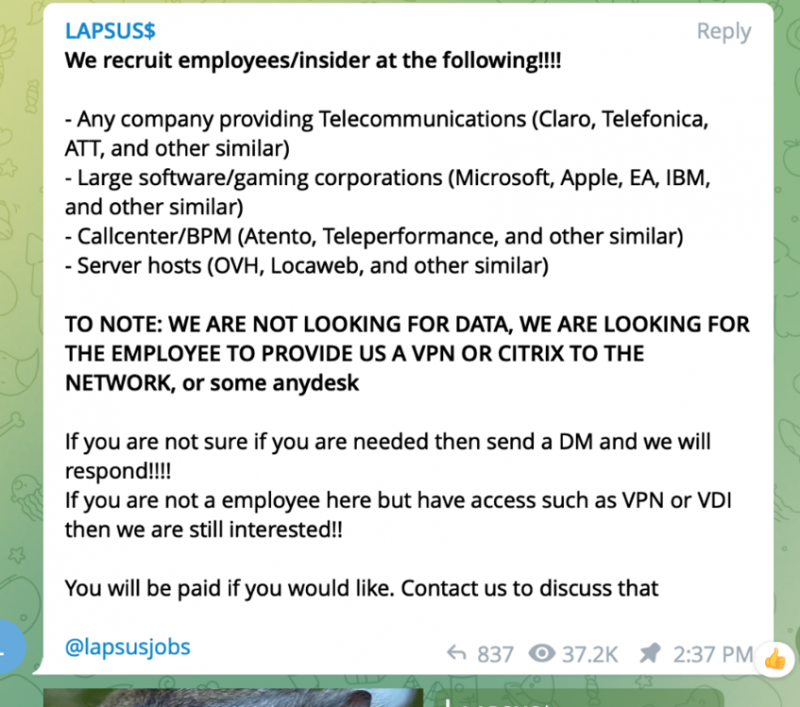
She’s been working with researchers at security firm Palo Alto Networks to track individual members of LAPSUS$ even prior to the group’s formation. Nixon told KrebsOnSecurity that she’s convinced that the White/OklAGG individual is the head honcho, given that, among other things, theidentity has been tied to the Lapsus$ group’s recruiting message for company insiders to help them penetrate targeted organizations.
Nixon told the BBC that researchers have had the Oxford teen’s name since the middle of last year and that they’d identified him even before he was doxed by a hacking forum – Doxbin, a site where people can post or sift through the personal data of hundreds of thousands of people for the purpose of doxing –that he’d allegedly purchased and then run as a lousy, much-complained-about admin.
He wound up selling the forum back to its previous owner, at a loss, then leaked the entire Doxbin dataset, leading to the Doxbin community turning around and doxing him right back. That included what Krebs reported as “videos supposedly shot at night outside his home in the United Kingdom,” along with his name, address, and social media pictures.
The Doxbin community also posted a curriculum vitae of his hacking career, the BBC reported – a career that made him filthy rich in short order. His Doxbin entry connected him to Lapsus$, as well. The entry reportedly reads:
“[He] slowly began making money to further expand his exploit collection. … After a few years his net worth accumulated to well over 300BTC (close to $14 mil). … [He] now is affiliated with a wannabe ransomware group known as ‘Lapsus$’, who has been extorting & ‘hacking’ several organisations.” —Doxbin entry, per the BBC
Nixon told the BBC that Unit 221B, working with Palo Alto, identified the threat actor and then watched his exploits throughout 2021, “periodically sending law enforcement a heads-up about the latest crimes.”
She said that researchers tracked him by “watching the post history of an account and seeing older posts provide contact information for the guy.” The “White” individual also helped, she said, by failing to cover his tracks.
Get Off My Code, You Damn Kids
After its breaches, Lapsus$ has posted stolen source code on the group’s Telegram channel, including code stolen from Microsoft’s Azure DevOps server for the company’s Bing and Cortana products. Lapsus$ has also posted screenshots of Okta’s Slack channels and the interface for Cloudflare, which is one of thousands of customers that use Okta’s technology to provide authentication for its employees.
In February, the group also stole two of Nvidia’s code-signing certificates – certificates that were then used to sign malware, enabling malicious programs to slide past security safeguards on Windows machines.
After its headline-grabbing attacks on Microsoft and Okta this past weekend, Lapsus$ announced on Tuesday that it was going to take a bit of a breather.
“A few of our members has a vacation until 30/3/2022. We might be quiet for some times,” the hackers wrote in the group’s Telegram channel. “Thanks for understand us. – we will try to leak stuff ASAP.”
Why’d You Do It?
Ken Westin, director of security strategy at Cybereason, said it’s tough to guess at the motivation of the purported “mastermind” teen. “Many had speculated it was an organized cybercrime syndicate or potential nation state actors,” he told Threatpost in an email on Thursday.
Whatever the teen’s motivation – he’s described as having autism, for whatever that’s worth – Westin thinks the security community underestimates the younger generation. “We forget teens today have not only grown up with computers, but also have access to an unprecedented number of educational resources on programming and offensive security,” he said.
“I speculated the group was young based on their modus operandi, or lack thereof, it was as if they were surprised by their success and were not sure what to do with it. In some of their follow up communications their language appeared more interested in the notoriety and [was] defensive of their capabilities and accomplishments than any financial motivation,” he continued.
Of course, when it comes to guessing what somebody’s motivation might be for taking on the world’s shiniest tech companies, et al., there’s always that purported 300BTC income that Doxbin pointed to. Not too shabby a motivation, that, particularly when planted in the still-developing brain of a tot that’s been put under glass during the pandemic.
“Today, teens have seen how much money is being made in criminal hacking, in some ways they are the new rockstars,” Westin said. “You pair this with the fact kids have been couped up for three years often with nothing but the internet to entertain themselves and we shouldn’t be surprised we have skilled hackers. The problem is that their brains are still developing and the line between fun and crime can get blurred, where it’s common for kids to hack to gain notoriety amongst their peers, but this easily crosses over into decisions that can affect the rest of their lives.”
It’s too early to say whether this will be the end of Lapsus$, he said. “it could still be a false flag, bad attribution, or even framing someone for the hacks. If it is this 16-year-old in England, it is likely we will see an end to the group’s activity, unless one of their partners in cybercrime takes up the mantle.”
Whether Lapsus$ boils down to a criminal gang or a teenager from Oxford, what matters is that the “organization” clearly has the ability to infiltrate some of the world’s largest organizations at a speed that makes these attacks impossible to prevent using traditional perimeter defense tools, said Darren Williams, founder and CEO of privacy/security/prevention firm BlackFog.
We can’t stick all teenagers in suspended animation until their brains are fully formed, but we can take note of how these groups/individuals stick it to targeted organizations. In an email to Threatpost on Thursday, Williams noted that more than 84 percent of all attacks involve data exfiltration, exposing data on the Dark Web and/or public web sites.
“By refocusing security efforts on anti-data exfiltration, organizations are able to mitigate extortion attempts, regulatory fines, reports and ultimately the loss of trust in the business,” Williams suggested.
Moving to the cloud? Discover emerging cloud-security threats along with solid advice for how to defend your assets with our FREE downloadable eBook, “Cloud Security: The Forecast for 2022.” We explore organizations’ top risks and challenges, best practices for defense, and advice for security success in such a dynamic computing environment, including handy checklists.
.png)
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·