BOOK THIS SPACE FOR AD
ARTICLE ADBug bounties is an upcoming trend nowadays. Hackers are paid legally to hack companies and getting paid from them. Many newcomers are attracted to financial rewards offered by bug bounty hence directly jumping straight into platforms without enough practice. In result, most of them ends up getting frustrated because of weeks or months without a valid bug hence not getting paid.

If you are a newcomer, this article is perfect for you to get started with bug bounties. I’ll try my best to explain it in a story mode with simple terms.
1. Why are hackers getting paid
Let’s start with understanding why hackers are paid to do all of these instead of ended up in jail. Traditionally, a company would have their own security team to prevent hackers from intruding their network/website infrastructure. As the company grows, more and more infrastructure of the company is being built and deployed until the security team are unable to verify all of it.
One day, someone emailed the security team of the company that he found a vulnerability in one of the company website. A vulnerability is a bug that can be used to damage the company’s infrastructure, customers of the company and even causing reputational damage. The security team are glad that the guy told them about the vulnerability and quickly deployed a fix against the vulnerability. To express their gratitude, the security team decided to send 100 dollars to the reporter’s PayPal account.
In the end, the reporter receives 100 dollars for their effort in reporting the security vulnerability to the company and the security team gets to fix it before the bad guys discovers it and do bad things with it.
2. Bug bounty platforms
The security team of the company thinks that this is a nice way for people to report vulnerability to them, so they want more. If possible, they want a group of hackers to find vulnerabilities in their system and in the mean time make sure they responsibly report the issue to them.
That’s when bug bounty platforms comes in. A bug bounty platform is a company that combine ethical hackers and companies together so the companies gets vulnerability reports from hackers and hackers get paid from doing that.
A bug bounty platform normally have many companies and even more hackers in their website. Three of the most popular bug bounty platforms are HackerOne, BugCrowd and Intigriti. (If your platform aren’t in this list I’m really sorry).
A bug bounty platform makes money by helping the company to handle security reports from hackers to make sure the report is a valid one before forwarding the issue to the company (yes, not all reports are valid security vulnerabilities).
If you read until here, you might wonder why the company wants to pay the platform to help them handle security reports? Aren’t security reports supposed to be confidential?
That’s where the policy comes in.
3. Bug bounty program policy
A company that uses a bug bounty platform is known as a bug bounty program. Every bug bounty program have their own policy which are similar in most cases (eg. don’t leak the vulnerability details to social media)
In a bug bounty platform, there is this role known as triager. A triager is someone like a middleman between the hacker and the program (the triager works for the platform). The duty of triager is to verify if the report submitted by the hacker is valid or invalid. If you’re wondering, hackers are not allowed to directly ask the program if a platform is managing it (think like you can’t tell the CEO your boss sucks, probably easier to understand).
If it’s not obvious enough, the triager is not supposed to leak any details to third parties (or else they get fired). They also need to make sure hackers can’t access other hacker’s report (no sharing here) or else the vulnerability will eventually be public.
You can imagine that when a hacker reported a vulnerability to a program, the only ones that have access to the vulnerability details are the triager and the program only.
Going back to the main point, the bug bounty policy is like the rules of what the hacker must obey when participating in the program. One of the policies that works everywhere is don’t disclose the vulnerability. This ensures that the company will be able to fix the vulnerability details privately and award the hacker.
4. Understand private and public programs
If you navigate to https://hackerone.com/directory/programs, https://bugcrowd.com/programs or https://www.intigriti.com/programs, you will see a list of programs offered for the hackers to hack them.
Is it all of them? Nope.
There is something known as private programs in bug bounty, which basically means a program that is … private. Private programs are companies that have bug bounty program but prefer to make it a secret and don’t want the public to know about.
All private programs have this policy of not disclosing their company’s bug bounty program publicly. For instance, HackerOne would remind hackers to not discuss a private program in public.

One of the reasons a company wants to make their bug bounty program private is they prefer experienced hackers rather than newcomers.
In short, they want pro hackers and don’t want noobs.
How can a hacker be differentiated as a pro or noob? Well, that’s why we have our next section, ranking system.
5. Ranking system
Just like most games, bug bounty platform have leaderboard to show the top hackers. The rankings are determined by the amount of reputation.
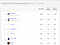


Reputation is something like a score you got from winning a match of online game with other players. Not all platforms uses the word reputation, BugCrowd uses the word points, but the concept is still the same.
The higher the reputation, the higher chance you have from getting private invites. Most hackers like to hack in private programs because there are fewer hackers which means less competition.
Each platform have different ways of calculating reputation within hackers, in general the larger the vulnerability impact, the hacker will receive more score. Impact basically means that how dangerous the vulnerability is to the company. The higher the impact, the better the reward is.
However, not all programs give financial reward but hackers still hack them.
6. Vulnerability Disclosure Programs (VDP)
Vulnerability disclosure programs is a program that accepts report from hackers but doesn’t give financial reward.
What? That’s not the reason I wanna get into bug bounties!
Indeed, some hackers may feel like it’s a waste of their time to hack on programs that doesn’t pay financially, however there are several reasons hackers still hack them.
One of them includes getting private invites. Remember I mentioned about private invites just now? Even though VDP don’t pay hackers financially, hackers can still earn reputation points and get invited into private programs that actually pays.
Beginners are also recommended to start with VDP as pro hackers are not there hence making it somehow easier.
7. Dedicated hacker emails
Imagine a hacker is hacking an online forum, is there anyway for the administrator to know which user is the hacker? If the webmaster discovers a user is trying to hack his website, how can the webmaster know the user is an ethical hacker participating in his bug bounty program and not a malicious hacker?
This is when hacker designated email address show up. When you register in a platform with your email address, the username you specified will automatically registers a hacker email address for you. Any email sent to the hacker email address will be forwarded to your real email address. Other than protecting the hacker’s privacy, this allows website owners to know that this specific user is an ethical hacker participating in their bug bounty program.
Some of them includes:
[username]@wearehackerone.com for HackerOne[username]@bugcrowdninja.com for BugCrowd[username]@intigriti.me for IntigritiSome of the program policy forces hackers to use their hacker email address to test the application. Hackers that do not obey might not receive a reward even if their report is valid simply because they did not follow the program’s policy.
8. Give what the company wants
Different programs have their own definition of security vulnerability. This highly depends on how the company operates their daily business.
Let’s think of an online gaming website started a bug bounty program. In the game, players have this thing called coins which is used to purchase in game items. The website makes money by allowing their players to use real money to purchase coins which gives them an advantage in the game.
Imagine a hacker discovers a vulnerability which allows him to gain infinite coins in the game. At first glance, it doesn’t look like a security vulnerability to other users because the hacker cannot hack the server’s infrastructure or other player’s account. However, the program gladly accepts it and pay the hacker a good sum of money. The reason behind this is because if this vulnerability is found by a malicious hacker, they will abuse this vulnerability to obtain unlimited coins in the game hence making the game unplayable for other players. This will decrease the player number in the game which will cause a financial loss for the website owner.
The above story is actually from a real world scenario. There are many gaming websites pay hackers financially if they discover a vulnerability that affects the game system in the website because it is their business.
In short, understand what the program wants and find them.
9. Conclusion
All the points above is just tip of the iceberg and there are still plenty I’m unable to write in one blog post.
Please sign up for our newsletter so you will receive a notification for the next blog post. ❤
.png)
 4 years ago
276
4 years ago
276 














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·