BOOK THIS SPACE FOR AD
ARTICLE ADAlthough not new, Registered Domain Generation Algorithms (RDGAs) have become a major cybersecurity threat, exploited by threat actors to bypass security solutions and distribute malware.
Cybersecurity is a growing concern, with threat actors constantly developing new ways to bypass security mechanisms and carry out their malicious activities. One such development that has flown under the radar for some time is the use of Registered Domain Generation Algorithms (RDGAs).
In a recent report, cybersecurity researchers at Infoblox have shed light on this rapidly growing technique, revealing how it has become a major tool for threat actors to impact the DNS threat environment.
From DGAs to RDGAs: A Stealthier Evolution
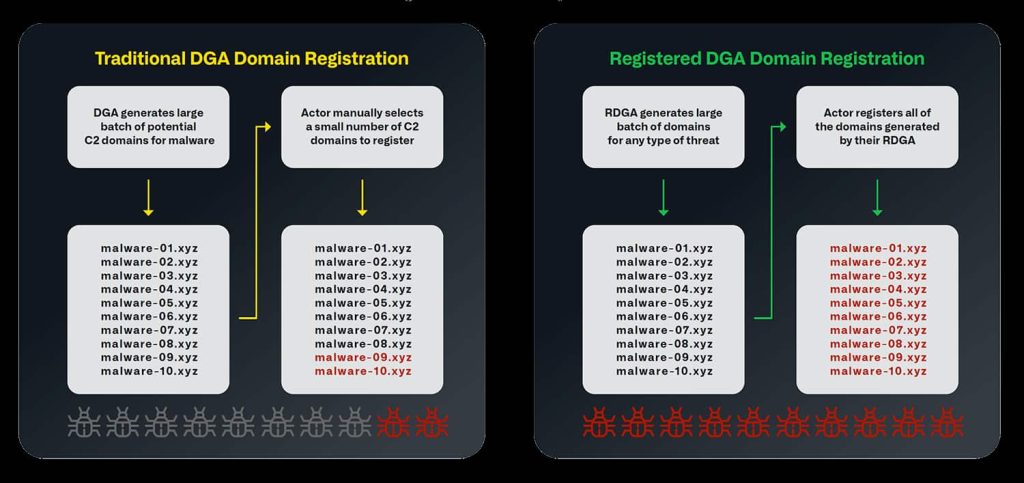
For your information, domain generation algorithms (DGAs) are not a new concept. For nearly two decades, they have been used by threat actors to distribute malware. However, the transformation of DGAs into RDGAs presents a challenge that is difficult to handle.
With RDGAs, threat actors programmatically create numerous domain names, either all at once or over time, for use in their criminal infrastructure. The key difference is that with RDGAs, the algorithm remains a closely guarded secret, and all domain names are registered, making them significantly harder to detect and defend against.
The Many Faces of RDGAs
RDGAs are not just limited to malware distribution. They have become a versatile tool for a wide range of malicious activities, including phishing, spam, scams, and even gambling.
One of the most concerning aspects is their use in traffic distribution systems (TDS) and virtual private networks (VPNs), allowing threat actors to fly under the radar and direct traffic to malicious destinations without raising suspicions.
Case Study: Hancitor Malware’s Stealthy Secret
Infoblox’s James Barnett writes in their technical report that a prime example of the effectiveness of RDGAs is the Hancitor malware. For years, this popular malware loader carried out malspam campaigns, delivering booby-trapped documents to unsuspecting victims.
What most didn’t realize was that Hancitor (aka Chanitor) used an RDGA to generate its C2 domains, allowing it to remain undetected and carry out its campaigns with ease. It was only through Infoblox’s statistical modelling and DNS expertise that the pattern was recognized, leading to the creation of predictive analytics to block Hancitor’s domains.
Revolver Rabbit: An RDGA Mastermind
The report also uncovers a prolific, yet unclassified, RDGA actor named Revolver Rabbit. This actor has registered an astonishing 500,000 domains on the .bond TLD alone. Their RDGA pattern is highly variable, making detection challenging without advanced DNS context.
Revolver Rabbit’s domains have been linked to both active C2s and decoy domains in XLoader malware (aka Roaming Mantis and MoqHao) samples, highlighting the critical need for RDGA detection and analysis.
A Rising Tide of Unknown RDGAs
The discovery of Revolver Rabbit is just the tip of the iceberg. Infoblox has detected thousands of other RDGAs with unknown purposes, and the numbers are only growing. In just six months, over 2 million unique RDGA domains were identified, averaging more than 11,000 new RDGA domains per day.
This rapid expansion underscores the urgency of automated detection as the only viable defence against these threats.
Securing Networks in an RDGA-laden environment
Nevertheless, the report concludes with a direct warning: RDGAs pose a serious threat to organizations, and their underreporting in the security industry is cause for concern. With RDGAs being used to register millions of new domains, organizations must implement security solutions with automated RDGA detection capabilities.
As RDGAs continue to expand and adapt, staying one step ahead of these threats is key for maintaining a secure cyber environment.
The full research report from Infoblox provides an in-depth exploration of RDGAs, offering valuable insights for cybersecurity professionals seeking to protect their organizations from this threat.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·