BOOK THIS SPACE FOR AD
ARTICLE ADGoogle has released an update to Chrome which includes seven security fixes. Version 123.0.6312.86/.87 of Chrome for Windows and Mac and 123.0.6312.86 for Linux will roll out over the coming days/weeks.
The easiest way to update Chrome is to allow it to update automatically, which basically uses the same method as outlined below but does not require your attention. But you can end up lagging behind if you never close the browser or if something goes wrong—such as an extension stopping you from updating the browser.
So, it doesn’t hurt to check now and then. And now would be a good time, given the severity of the vulnerability in this patch. My preferred method is to have Chrome open the page chrome://settings/help which you can also find by clicking Settings > About Chrome.
If there is an update available, Chrome will notify you and start downloading it. Then all you have to do is relaunch the browser in order for the update to complete, and for you to be safe from those vulnerabilities.
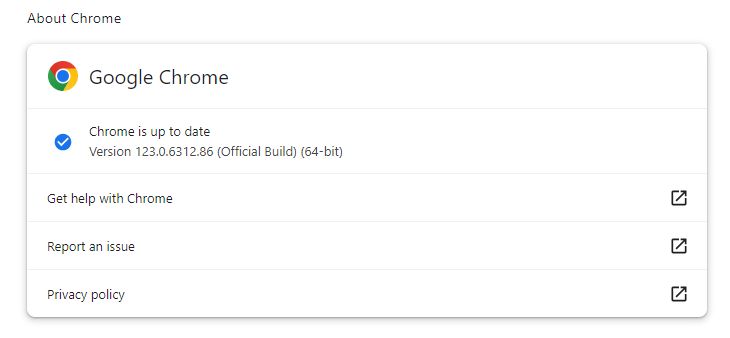
After the update, the version should be 123.0.6312.86, or later
Technical details
Google never gives out a lot of information about vulnerabilities, for obvious reasons. Access to bug details and links may be kept restricted until a majority of users are updated with a fix.
There is one critical vulnerability that looks like it might be of interest to cybercriminals.
CVE-2024-2883: Use after free (UAF) vulnerability in Angle in Google Chrome prior to 123.0.6312.86 could allow a remote attacker to potentially exploit heap corruption via a crafted HTML page.
Angle is a browser component that deals with WebGL (short for Web Graphics Library) content. WebGL is a JavaScript API for rendering interactive 2D and 3D graphics within any compatible web browser without the use of plug-ins.
UAF is a type of vulnerability that is the result of the incorrect use of dynamic memory during a program’s operation. If, after freeing a memory location, a program does not clear the pointer to that memory, an attacker can use the error to manipulate the program. Referencing memory after it has been freed can cause a program to crash, use unexpected values, or execute code. In this case, when the vulnerability is exploited, it can lead to heap corruption.
Heap corruption occurs when a program modifies the contents of a memory location outside of the memory allocated to the program. The outcome can be relatively benign and cause a memory leak, or it may be fatal and cause a memory fault, usually in the program that causes the corruption.
Chromium vulnerabilities are considered critical if they “allow an attacker to read or write arbitrary resources (including but not limited to the file system, registry, network, etc.) on the underlying platform, with the user’s full privileges.”
So, to sum this up, in this case an attacker could create a specially crafted HTML page–which can be put online as a website–that exploits the vulnerability, potentially leading to a compromised system.
My suggestion: don’t wait for the update, get it now.
We don’t just report on vulnerabilities—we identify them, and prioritize action.
Cybersecurity risks should never spread beyond a headline. Keep vulnerabilities in tow by using ThreatDown Vulnerability and Patch Management.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·