BOOK THIS SPACE FOR AD
ARTICLE ADUncover the risks posed by a data leak exposing over 3 million vulnerable records, internal communications, client details, and plaintext passwords – Explore proactive cybersecurity measures to mitigate threats.
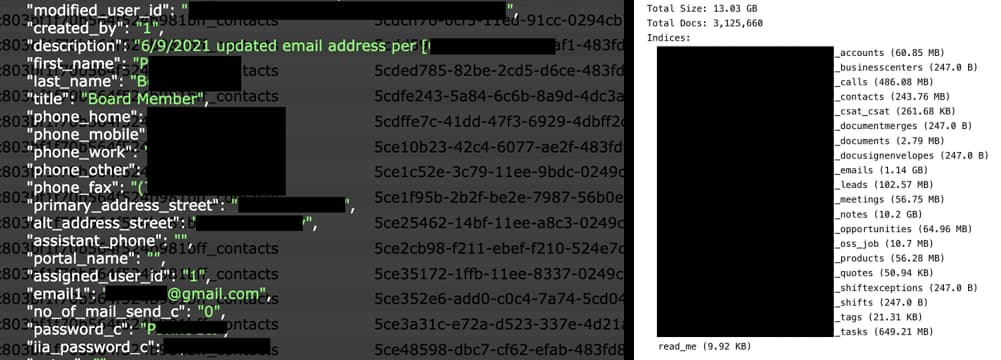
Cybersecurity researcher Jeremiah Fowler made a significant discovery: a 13 GB misconfigured cloud database resembling a Customer Relationship Management (CRM) system, reportedly linked to CU Solutions Group, a Michigan-based credit union service provider.
The data leak’s severity was made worse by two critical factors: firstly, it was left publicly accessible without any security authentication or password protection. Secondly, the server contained over 3 million records (3,125,660 in total), including a collection of sensitive information. This included over 1 million email conversations, internal notes, clients’ full names, physical addresses, details about thousands of credit unions across the United States, email addresses, and plaintext passwords.
In his blog post for Website Planet, Fowler detailed how he contacted CU Solutions Group for responsible disclosure, leading to the company securing the server on the same day. However, representatives of the company attributed the misconfiguration to a possible mismanagement by a third-party vendor, leaving the actual responsibility unclear.
Nevertheless, despite the database being secured, uncertainty remains regarding whether malicious threat actors, aside from Fowler (the good guy), had accessed it before the researcher’s report. If they had, it could lead to the breach being circulated on cybercrime forums. This, in turn, could result in additional cybersecurity threats, including ransomware attacks, spam, identity theft, account takeover due to plaintext passwords, phishing attacks, and more.
If you are registered with CU Solutions Group, it is a good time to contact the company and inquire about the data leak. Additionally, enable 2FA on your account and keep an eye on any suspicious activity on it.
Database misconfiguration is a top cybersecurity threat. It allows threat actors to access a trove of data hardly without looking and exploiting for vulnerabilities or breaching a system. Anyone with knowledge of how to surf the Shodan search engine can access these databases.
Here’s what companies can do to secure a misconfigured database and prevent exposure:
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·