BOOK THIS SPACE FOR AD
ARTICLE AD
In an ongoing blackhat SEO campaign tracked by BleepingComputer, scammers are using open redirects found on government websites to redirect visitors to pornography sites.
An open redirect is an URL that anyone can use to redirect a visitor to a website of their choosing.
Blackhat SEO scammers use these open redirects to get listings in search engines, such as Google, that show the page's title being redirected to but are listed as if it is located on the government site.
For about two weeks, scammers have been injecting government open redirect links into search engines as shown in the heavily redacted image below.
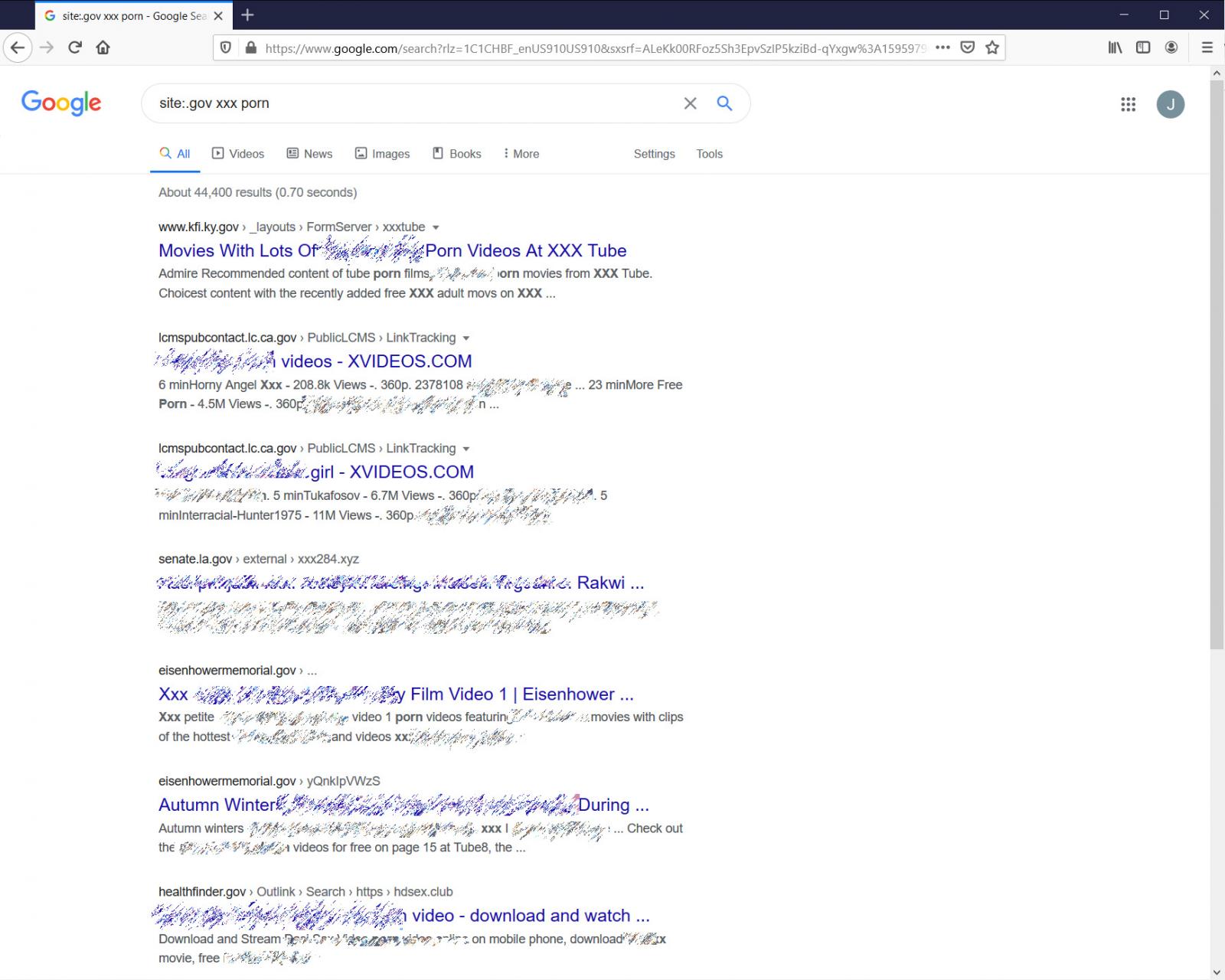 Indexed open redirects in search results
Indexed open redirects in search resultsSource: BleepingComputer
While government system administrators have been playing whack-a-mole and removing open redirects as they find them, new ones keep appearing and being used to inject links to adult sites in search engines.
The SEO scammers are not targeting only government websites or a particular platform, CMS, or script, and are merely searching for open redirects and injecting them into search engines.
One of the open redirects seen by BleepingComputer was found on the National Weather Service website.
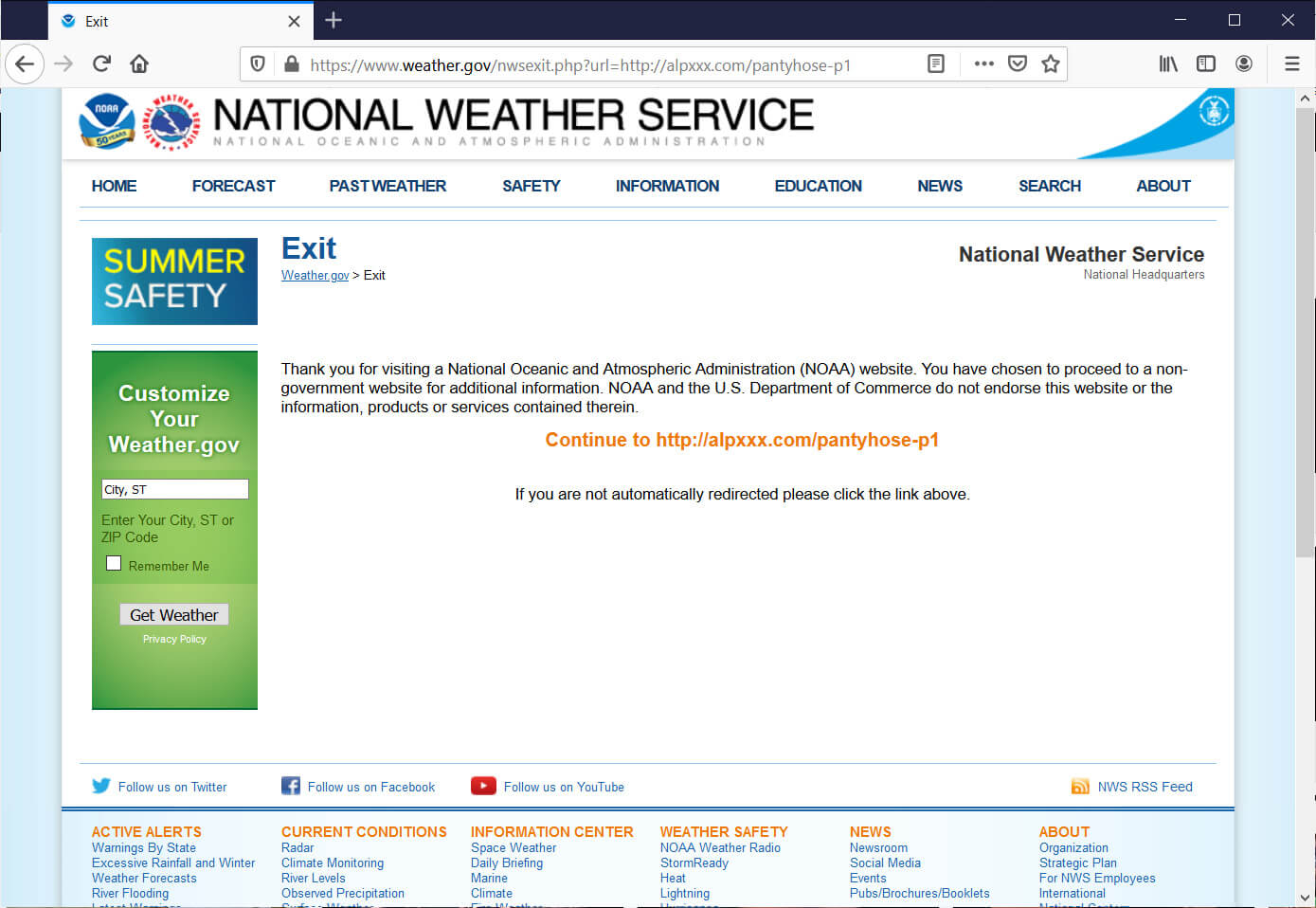 National Weather Service redirect abuse
National Weather Service redirect abuseSource: BleepingComputer
This site uses an open redirect in the form of a nwsexit.php script that lets you create a weather.gov URL that redirects to another site.
For example, the URL below will redirect a user from weather.gov to example.com.
https://www.weather.gov/nwsexit.php?url=http://example.comThough the weather.gov site shows a brief interstitial page before redirecting visitors, most of the open redirects do not use a page like this and automatically redirect them.
It is not known at this time how the SEO scammers are injecting these links into search engines.
Historically, these types of attackers are conducted by hacking into WordPress sites and then creating pages containing hundreds of URLs that they want to be indexed.
These pages are then fed into search engines so that the search engine spiders index them and add URLs to the search results.
Thankfully, these websites were abused to only redirect users to pornography sites. They could have just as easily been used as part of phishing campaigns targeting government employees to steal account credentials.
Some of the domains affected by this blackhat SEO campaign are the National Weather Service, Louisiana State Senate, Dwight D. Eisenhower Memorial, the Colorado Department of Higher Education, and many more.
Below is a list of some of the federal and local government sites abused in this SEO campaign.
www.kfi.ky.gov lcmspubcontact.lc.ca.gov senate.la.gov eisenhowermemorial.gov healthfinder.gov goea.louisiana.gov ecfsapi.fcc.gov www.cftc.gov www.weather.gov www.jeffersoncountyfl.gov archive.usgs.gov hru.gov id.loc.gov www.minnesota.feb.gov bphc.hrsa.gov akleg.gov srs.fs.usda.gov arlweb.msha.gov www.mountainview.gov drafts.wichita.gov highered.colorado.gov www.maurycounty-tn.gov www.research.gov www.brooklynohio.gov www.nwcg.gov supplier.raleighnc.gov search.wi.gov.png)














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·