BOOK THIS SPACE FOR AD
ARTICLE ADUS Cyber Command linked the group to Iranian intelligence and detailed its multi-pronged, increasingly sophisticated suite of malware tools.
U.S. Cyber Command has confirmed that MuddyWater – an advanced persistent threat (APT) cyberespionage actor aka Mercury, Static Kitten, TEMP.Zagros or Seedworm that’s historically targeted government victims in the Middle East – is an Iranian intelligence outfit.
The link has been suspected, and now it’s government-stamped. On Wednesday, USCYBERCOM not only confirmed the tie; it also disclosed the plethora of open-source tools and strategies MuddyWater uses to break into target systems and released malware samples.
“MuddyWater has been seen using a variety of techniques to maintain access to victim networks,” according to USCYBERCOM’S National Mission Force (CNMF). “These include side-loading DLLs in order to trick legitimate programs into running malware and obfuscating PowerShell scripts to hide command and control functions.”
USCYBERCOM has uploaded multiple MuddyWater-attributed malware samples to VirusTotal.
Iranian MOIS hacker group #MuddyWater is using a suite of malware to conduct espionage and malicious activity. If you see two or more of these malware on your network, you may have MuddyWater on it: https://t.co/xTI6xuQOg3. Attributed through @NCIJTF @FBI
— USCYBERCOM Cybersecurity Alert (@CNMF_CyberAlert) January 12, 2022
USCYBERCOM’s press release described MuddyWater as being “a subordinate element within the Iranian Ministry of Intelligence and Security (MOIS).” The Congressional Research Service describes MOIS as conducting “domestic surveillance to identify regime opponents” and said that the agency is responsible for surveillance of anti-regime activists abroad through a network of agents placed in Iran’s embassies.
New Variants of PowGoop Malware
Among multiple malware sets, MuddyWater is using new variants of the PowGoop malware family, CNMF said.
PowGoop was first described by Palo Alto Networks in September 2020, when it was used in attacks on two state-run organizations in the Middle East and North Africa that ultimately installed and ran a variant of the Thanos ransomware.
At the time, Palo Alto suspected that the threat actors were using a downloader – one that researchers dubbed PowGoop – to reach out to a remote server to download and execute PowerShell scripts. The name comes from the use of GoogleUpdate.exe to load a malicious, modified version of goopdate.dll – a DLL that’s used to load a malicious PowerShell script from an external file.
PowGoop has been buffed up since it was first spotted: SentinelLabs on Wednesday explained that significantly enhanced, newer variants of PowGoop have shown up in the wild, discovered in recently triaged incidents, “suggesting the group continues to use and maintain it even after recent exposures.”
“The new variants reveal that the threat group has expanded its arsenal of legitimate software used to load malicious DLLs,” SentinelOne intelligence researcher Amitai Ben Shushan Ehrlich wrote.
Ehrlich explained that, aside from GoogleUpdate.exe, three more benign pieces of software are abused in order to sideload malicious DLLs: Git.exe, FileSyncConfig.exe and Inno_Updater.exe.
CNMF has shared new samples showing the different parts of MuddyWater’s new suite of tools, along with JavaScript files used to establish connections back to malicious infrastructure. They include new PowGoop command-and-control (C2) beacon variants as well as the Mori Backdoor: a backdoor used for cyber espionage that employes DNS tunneling to communicate with the C2 infrastructure.
“Any instances of these files may indicate an attacker in the network,” CNMF reiterated about newly released and already known indicators of compromise (IoC). “Should a network operator identify multiple of the tools on the same network, it may indicate the presence of Iranian malicious cyber actors.”
Love of Tunneling, Exchange Exploits & Ruler Abuse
SentinelLabs drilled down into multiple additional recent findings about MuddyWater’s techniques, tactics and procedures (TTPs), including:
MuddyWater Tunneling Activity: “The operators behind MuddyWater activities are very fond of tunneling tools,” SentinelOne’s Ehrlich wrote. “The custom tools used by the group often provide limited functionality, and are used to drop tunneling tools which enable the operators to conduct a wider set of activities.”
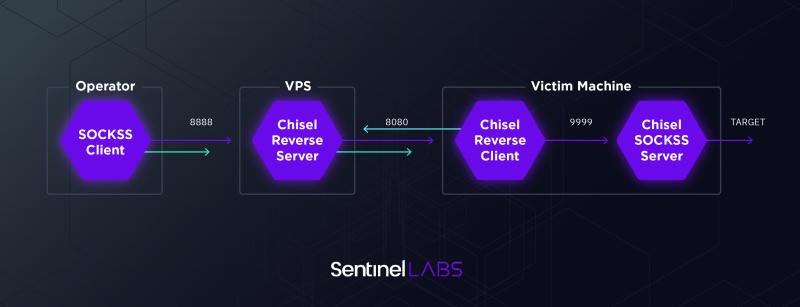
MuddyWater attackers are using tunneling tools including Chisel, SSF and Ligolo: tools that enable the threat actor to connect to machines within target environments as if they were inside the operator LAN, he explained.
Exploiting Microsoft Exchange: Sentinel Labs has also tracked MuddyWater targeting Exchange servers of high-profile organizations. “This subset of Exchange exploitation activity is rather interesting, as without context it would be difficult to attribute it to MuddyWater because the activity relies almost completely on publicly available offensive security tools,” Ehrlich noted.
They’re using two tools to try to exploit Exchange servers: a publicly available script for exploiting CVE-2020-0688 – a vulnerability that enables remote code execution (RCE) for an authenticated user – and Ruler, an open source Exchange exploitation framework recently used to target a string of Middle Eastern telecom operators and IT companies, as reported by Symantec’s Threat Hunter Team last month.
MuddyWater: Better & Better at Stirring Up Muck
Analysis shows that the MuddyWater APT continues to evolve and adapt its techniques Sentinel Labs summarized. “While still relying on publicly available offensive security tools, the group has been refining its custom toolset and utilizing new techniques to avoid detection,” Ehrlich observed, pointing to evolution of the PowGoop malware family, the group’s use of tunneling tools, and its targeting of Exchange servers in high-profile organizations.
The group doesn’t have to be fancy to be effective, he noted: “Like many other Iranian threat actors, the group displays less sophistication and technological complexity compared to other state-sponsored APT groups. Even so, it appears MuddyWater’s persistency is a key to their success, and their lack of sophistication does not appear to prevent them from achieving their goals.”
Password Reset: On-Demand Event: Fortify 2022 with a password security strategy built for today’s threats. This Threatpost Security Roundtable, built for infosec professionals, centers on enterprise credential management, the new password basics and mitigating post-credential breaches. Join Darren James, with Specops Software and Roger Grimes, defense evangelist at KnowBe4 and Threatpost host Becky Bracken. Register & Stream this FREE session today – sponsored by Specops Software.
.png)
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·