Days after Microsoft, Secureworks, and Volexity shed light on a new spear-phishing activity unleashed by the Russian hackers who breached SolarWinds IT management software, the U.S. Department of Justice (DoJ) Tuesday said it intervened to take control of two command-and-control (C2) and malware distribution domains used in the campaign.
The court-authorized domain seizure 1m took place on May 28, the DoJ said, adding the action was aimed at disrupting the threat actors' follow-on exploitation of victims as well as block their ability to compromise new systems. The department, however, cautioned that the adversary might have deployed additional backdoor accesses in the interim period between when the initial compromises occurred, and the seizures took place last week.
"[The] action is a continued demonstration of the Department's commitment to proactively disrupt hacking activity prior to the conclusion of a criminal investigation," said Assistant Attorney General John C. Demers for the Justice Department's National Security Division. "Law enforcement remains an integral part of the U.S. government's broader disruption efforts against malicious cyber-enabled activities, even prior to arrest, and we will continue to evaluate all possible opportunities to use our unique authorities to act against such threats."
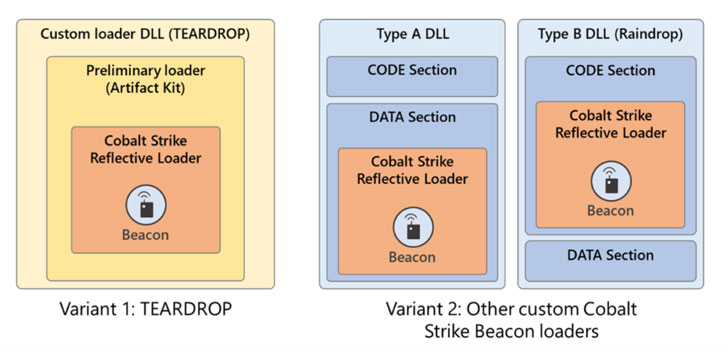
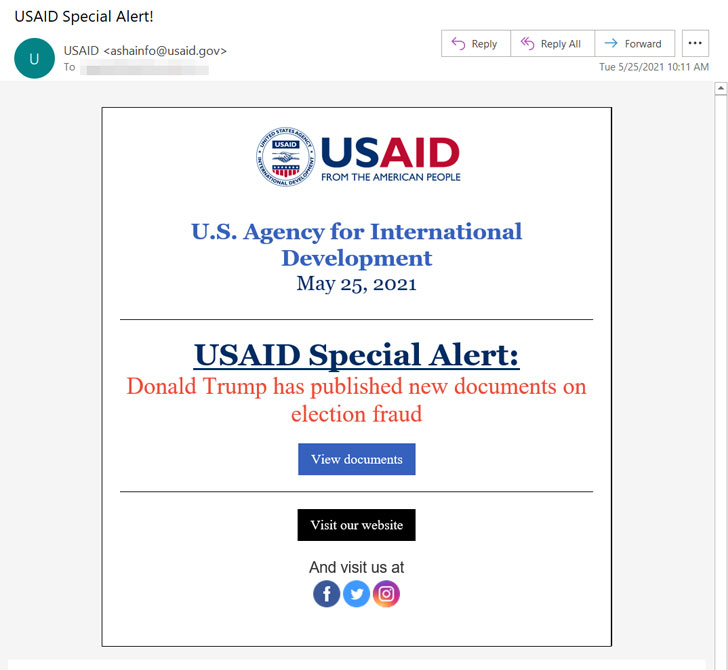
The two domains in question — theyardservice[.]com and worldhomeoutlet[.]com — were used to communicate and control a Cobalt Strike beacon called NativeZone that the actors implanted on the victim networks. The wide-scale campaign, which was detected on May 25, leveraged a compromised USAID account at a mass email marketing company called Constant Contact to send phishing emails to approximately 3,000 email accounts at more than 150 different organizations.
Once the recipients clicked on the embedded link in the email message, a sub-domain of theyardservice[.]com was used to gain an initial foothold into the victim machine, exploiting it to retrieve the Cobalt Strike backdoor to maintain persistent presence and potentially deliver additional payloads. "The actors' instance of the Cobalt Strike tool received C2 communications via other subdomains of theyardservice[.]com, as well as the domain worldhomeoutlet[.]com," the DoJ said.
Microsoft attributed the ongoing intrusions to the Russian threat actor it tracks as Nobelium, and by the wider cybersecurity community under the monikers APT29, UNC2452 (FireEye), SolarStorm (Unit 42), StellarParticle (Crowdstrike), Dark Halo (Volexity), and Iron Ritual (Secureworks).
The company has since identified three more unique pieces of malware used in the infection chain, namely BoomBox, EnvyScout, and VaporRage, adding to the attackers' growing arsenal of hacking tools such as Sunburst, Sunspot, Raindrop, Teardrop, GoldMax, GoldFinder, Sibot, and Flipflop, once again demonstrating Nobelium's operational security priorities when targeting potentially high-risk and high-visibility environments.
While BoomBox is a downloader to obtain a later-stage payload from an actor-controlled Dropbox account, VaporRage is a shellcode loader used to download, decode, and execute an arbitrary payload fully in-memory. EnvyScout, on the other hand, is a malicious dropper capable of de-obfuscating and writing a malicious ISO file to disk and is delivered in the form of a malicious HTML attachment to spear-phishing emails.
The attacker's practice of changing tactics several times over the course of its latest campaign underscores the widespread damage that could be inflicted on individual victims, government agencies, non-governmental organizations, and private businesses, not to mention reflect on its pattern of establishing access on one system or account and then using it as a jumping-off point to gain access to numerous targets.
In "significantly" differing from the SolarWinds hack by way of evolving its tools and tradecraft, the modus operandi enables a high level of stealth that allows them to remain undetected for extended periods of time, the researchers noted.
"Nobelium is an actor that operates with rapid operational tempo, often leveraging temporary infrastructure, payloads, and methods to obfuscate their activities," Microsoft said. "Such design and deployment patterns, which also include staging of payloads on a compromised website, hamper traditional artifacts and forensic investigations, allowing for unique payloads to remain undiscovered."
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 3 years ago
208
3 years ago
208 
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·