Bolstering password policies in your organization is an important part of a robust cybersecurity strategy. Cybercriminals are using compromised accounts as one of their favorite tactics to infiltrate business-critical environments; as we've seen in recent news, these attacks can be dangerous and financially impactful.
Unfortunately, account compromise is a very successful attack method and requires much less effort than other attack vectors.
One of the essential types of password protection recommended by noted cybersecurity standards is breached password detection. Hackers often use known breached password lists in credential stuffing or password spraying attacks.
Here are some critical criteria to consider when your sysadmins are evaluating breached password protection solutions.
Breached password recommendations
In the last few years, password security recommendations have evolved past the traditional recommendations regarding password security.
Businesses have used Microsoft Active Directory for years to implement password policies in the organization. Standard Active Directory password policies include minimal password configuration settings.
Below is an example of the settings offered with a conventional Active Directory Password Policy:
Enforce password history Maximum password age Minimum password age Minimum password length Minimum password length audit Password must meet complexity requirements Store password using reversible encryptionBy default, Active Directory Password Policies do not include a solution to implement breached password protection.
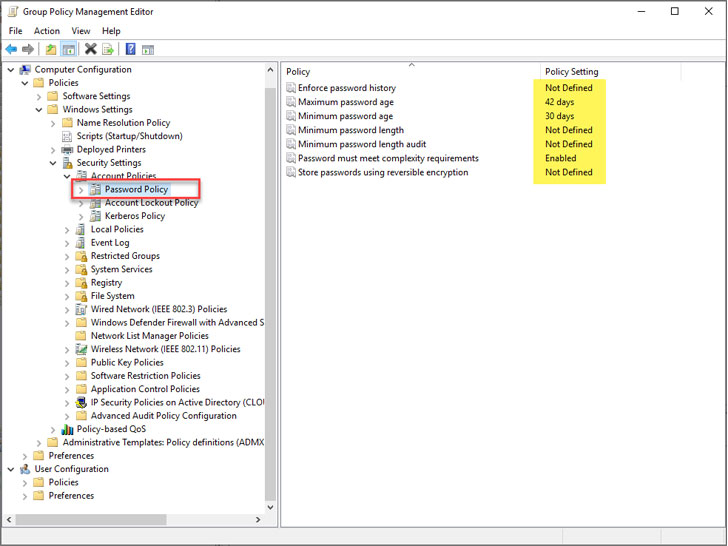 |
| Active Directory Password Policy settings |
Why is it important for businesses to start thinking about breached password protection? Let's look at best practice recommendations from leading authorities in cybersecurity guidance.
New password policy recommendations
As mentioned, traditional password policies created using Active Directory are limited in features and capabilities. These allow creating basic password policies with standard length, complexity, age, and other requirements. However, there is no way to use native functionality to implement breached password protection.
While there is a means for implementing a password filter .dll in Active Directory to provision password dictionary protection, this is a manual process relying on the development of custom password filter .dll files.
New password policy guidance from leading cybersecurity authorities such as the National Institute of Standards and Technology (NIST) recommend breached password protection. The NIST Special Publication 800-63B SP 800-63B Section 5.1.1.2 paragraph 9 states:
"Verifiers SHOULD NOT impose other composition rules (e.g., requiring mixtures of different character types or prohibiting consecutively repeated characters) for memorized secrets. Verifiers SHOULD NOT require memorized secrets to be changed arbitrarily (e.g., periodically). However, verifiers SHALL force a change if there is evidence of compromise of the authenticator."
Basically, NIST's guidance recommends that organizations should force a password change if there is evidence of a breach. For businesses to have proof of a password breach, they must have a way to monitor the password landscape for breached passwords. In addition to monitoring for passwords to become breached, as users choose new passwords, the new password choices need to be checked.
Evaluating breached password detection services
Breached password detection is a recommended best practice for an additional layer of cyberattack prevention. Consider the following functions as must-haves to pay close attention to when choosing a solution:
Ease of deployment Proactive monitoring Proactive password changes Breached password database size Integration with current Active Directory password policies Ease of deploymentAn essential consideration businesses need to make when choosing a third-party breached password solution is deployment ease. Look for solutions that are easily deployed using existing Active Directory infrastructure. Solutions that are difficult to deploy will likely lead to configuration issues and challenges with implementation and time to value. Look for solutions that make use of existing Active Directory infrastructure along with Group Policy that allows quickly making use of existing policies and infrastructure.
1 — Proactive monitoring
One of the essential requirements for breached password protection is proactive monitoring. Organizations need a solution that checks a password during the password set operation and proactively monitors the password landscape to find passwords that may become breached. This functionality helps to ensure passwords that may not be breached during creation, but become breached later, are correctly identified and can be remediated.
2 — Proactive password changes
Dovetailing into the proactive monitoring of breached passwords in the environment, organizations need to look for a breached password protection solution that proactively requires end-users to change their password if these become breached. This feature helps ensure any passwords that become breached in the environment are remediated as quickly as possible.
3 — Breached password database size
Keep in mind that all breached password protection services are not equal in the number of breached passwords checked. Breached password databases may vary between different services. The more extensive the breached password database, the better for protecting against breached passwords. If the quantity of breached passwords isn't transparently communicated, ask the vendor directly how many are included in their backend lists.
4 — Integration with current Active Directory password policies
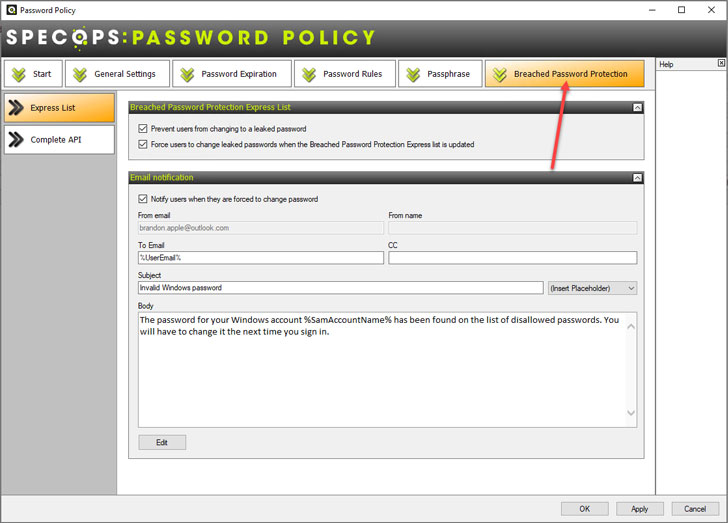 |
| Specops Breached Password Protection |
Look for a breached password protection solution that can integrate with current Active Directory password policies. It means you can leave GPO assignments in place that assign various password policies to specific users and will help to prevent "reinventing the wheel."
Specops Breached Password Protection
The Specops Password Policy solution allows organizations to have powerful breached password protection as part of the environment's password security. Features include all the top requirements, like:
Proactive breached password monitoring and password change enforcement Easily to deploy and integrates with existing Active Directory GPO-based password policies Downloadable breached password database or API-based protection Managed database of over 2-billion passwords and growing With the API-based approach, you get real-time breached password protection for your organization's passwordsUsing Specops Password Policy with Breached Password Protection, you can easily rollout breached password protection using GPO-based Active Directory Password Policies that are already in place.
To delve into the Specops Password Policy with Breached Password Protection, start a free trial anytime.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 3 years ago
300
3 years ago
300 















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·