Microsoft has warned about a new strain of mobile ransomware that takes advantage of incoming call notifications and Android's Home button to lock the device behind a ransom note.
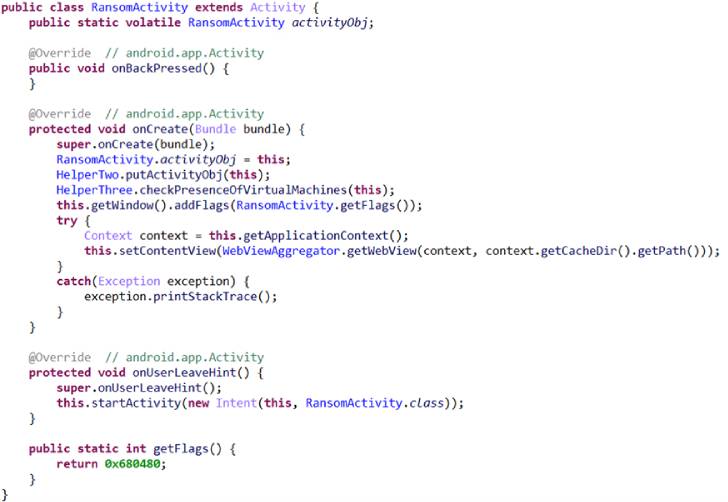
The findings concern a variant of a known Android ransomware family dubbed "MalLocker.B" which has now resurfaced with new techniques, including a novel means to deliver the ransom demand on infected devices as well as an obfuscation mechanism to evade security solutions.
The development comes amid a huge surge in ransomware attacks against critical infrastructure across sectors, with a 50% increase in the daily average of ransomware attacks in the last three months compared to the first half of the year, and cybercriminals increasingly incorporating double extortion in their playbook.
MalLocker has been known for being hosted on malicious websites and circulated on online forums using various social engineering lures by masquerading as popular apps, cracked games, or video players.
Previous instances of Android ransomware have exploited Android accessibility features or permission called "SYSTEM_ALERT_WINDOW" to display a persistent window atop all other screens to display the ransom note, which typically masquerade as fake police notices or alerts about purportedly finding explicit images on the device.
But just as anti-malware software began detecting this behavior, the new Android ransomware variant has evolved its strategy to overcome this barrier. What's changed with MalLocker.B is the method by which it achieves the same goal via an entirely new tactic.
To do so, it leverages the "call" notification that's used to alert the user about incoming calls in order to display a window that covers the entire area of the screen, and subsequently combines it with a Home or Recents keypress to trigger the ransom note to the foreground and prevent the victim from switching to any other screen.
"This creates a chain of events that triggers the automatic pop-up of the ransomware screen without doing infinite redraw or posing as a system window," Microsoft said.
Aside from incrementally building on an array of aforementioned techniques to show the ransomware screen, the company also noted the presence of a yet-to-be-integrated machine learning model that could be used to fit the ransom note image within the screen without distortion, hinting at the next stage evolution of the malware.
Furthermore, in an attempt to mask its true purpose, the ransomware code is heavily obfuscated and made unreadable through name mangling and deliberate use of meaningless variable names and junk code to thwart analysis, the company said.
"This new mobile ransomware variant is an important discovery because the malware exhibits behaviors that have not been seen before and could open doors for other malware to follow," Microsoft 365 Defender Research Team said.
"It reinforces the need for comprehensive defense powered by broad visibility into attack surfaces as well as domain experts who track the threat landscape and uncover notable threats that might be hiding amidst massive threat data and signals."
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 4 years ago
167
4 years ago
167 















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·