BOOK THIS SPACE FOR AD
ARTICLE AD
A new phishing technique using Chrome's Application Mode feature allows threat actors to display local login forms that appear as desktop applications, making it easier to steal credentials.
The Application Mode feature is available in all Chromium-based browsers, including Google Chrome, Microsoft Edge and the Brave Browser. It can generate realistic-looking login screens that are hard to differentiate from a legitimate login prompt.
Because desktop applications are generally harder to spoof, users are less likely to treat them with the same caution they reserve for browser windows that are more widely abused for phishing.
The potential for using Chrome's app mode in phishing attacks was demonstrated by researcher mr.d0x, who also devised "Browser-in-the-Browser" attacks earlier in the year. Multiple threat actors later used the BiTB technique in phishing attacks to steal credentials.
Chromium application mode feature
Chrome's application mode allows web developers to create web apps with a native desktop appearance suitable for ChromeOS or users who want to enjoy a clean, minimalist interface, like watching YouTube.
The app mode allows websites to launch in a separate window that doesn't display a URL address bar, browser toolbars, etc., while the Windows Taskbar displays the website's favicon instead of Chrome's icon.
This can allow threat actors to create fake desktop login forms, and if the user isn't knowingly launching these "apps," it could lead to sneaky phishing attacks.
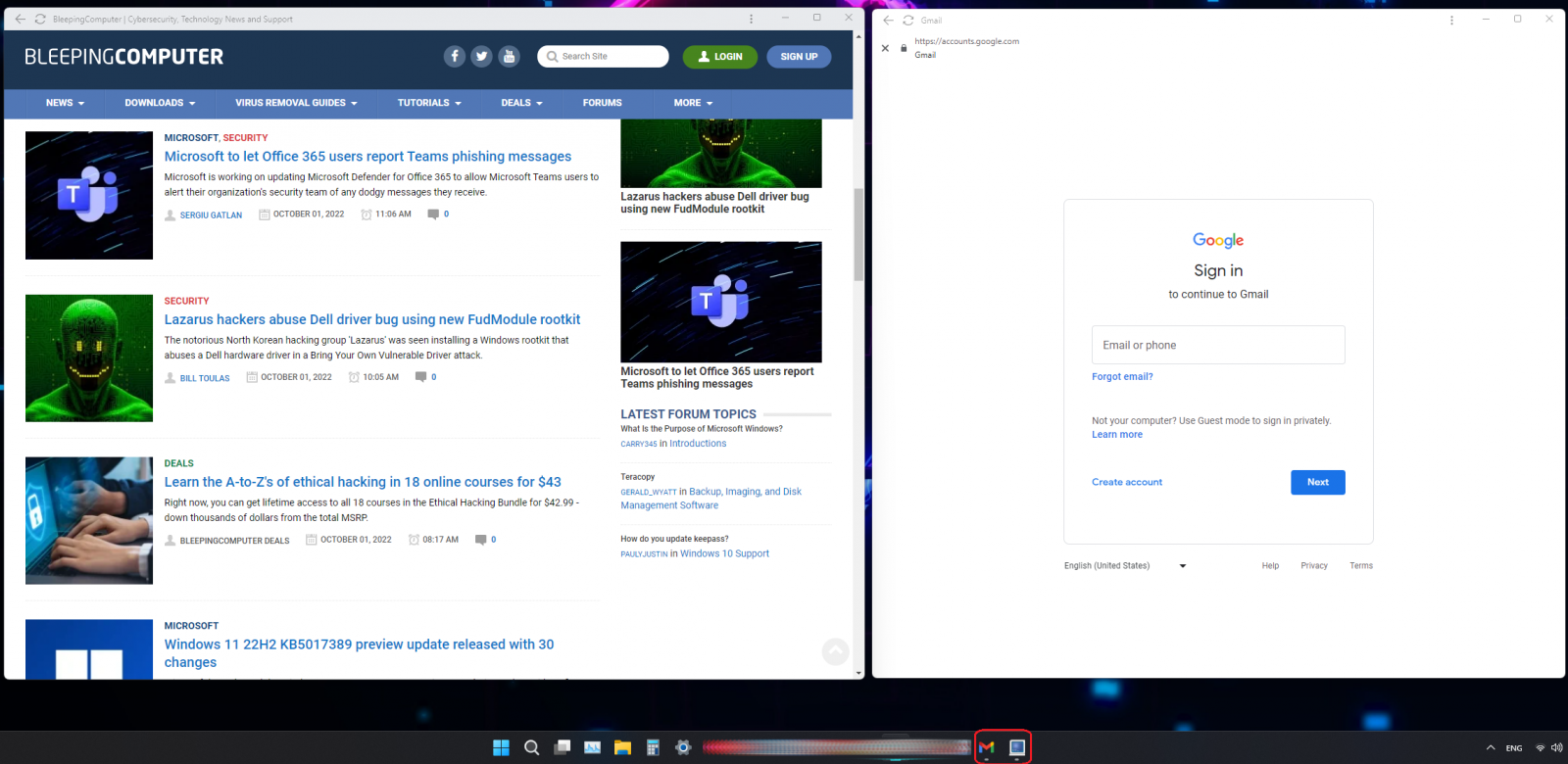 BleepingComputer and Gmail opened in Chrome's app mode
BleepingComputer and Gmail opened in Chrome's app modeAbusing app mode in attacks
To conduct an attack using the technique, threat actors must first convince a user to run a Windows shortcut that launches a phishing URL using Chromium's App Mode feature.
After Microsoft started disabling macros by default in Office, threat actors have switched to new phishing attacks that have proven to be very successful. One method that is commonly used is to email Windows shortcuts (.LNK) in ISO archives to distribute QBot, BazarLoader, BumbleBee, and other malware.
However, installing malware is very noisy and can easily be detected by security software running on the machine. On the other hand, opening a browser to a new phishing URL will less likely be detected.
With Microsoft Edge now installed in Windows 10 and later by default, it is easier to conduct these attacks, as threat actors can simply distribute Windows shortcut files that launch Microsoft Edge.
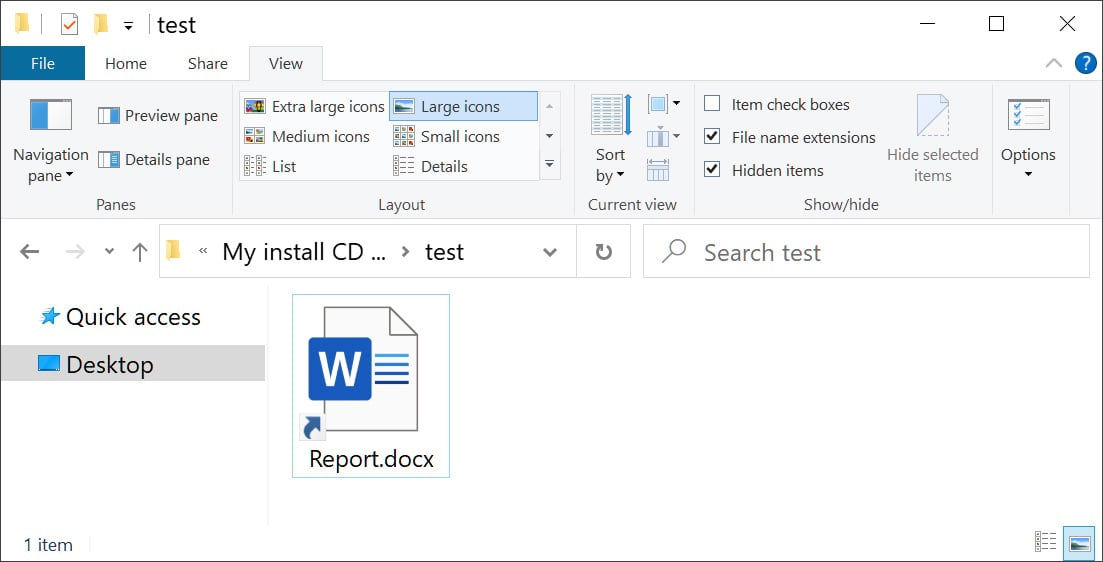 Windows shortcut disguised as a Word document
Windows shortcut disguised as a Word documentSource: BleepingComputer
As mr.d0x explains in his post, using the following commands, a malicious attacker could create shortcuts that launch a phishing "applet" on the target's computer.
# Chrome "C:\Program Files\Google\Chrome\Application\chrome.exe" --app=https://example.com # Microsoft Edge "c:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --app=https://example.com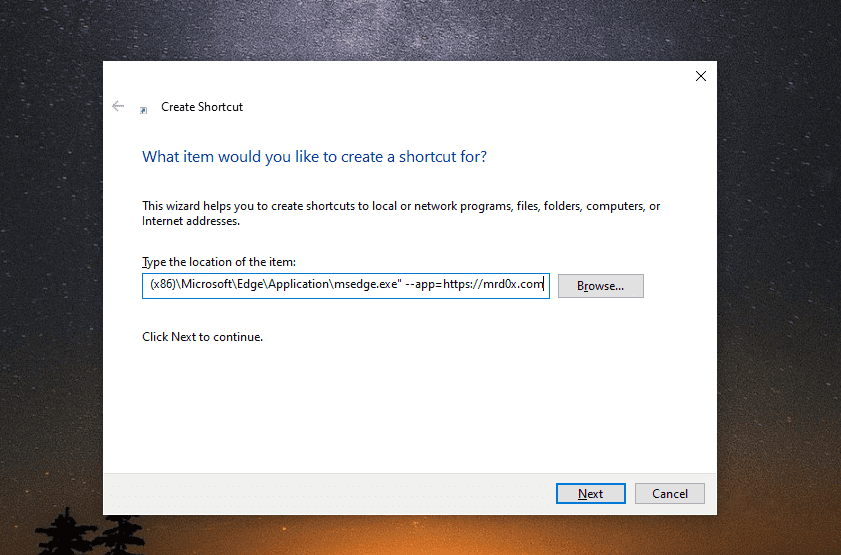 Adding the required parameters on the malicious file (mrd0x.com)
Adding the required parameters on the malicious file (mrd0x.com)Although this would require access to the target's machine, which is a strong prerequisite, this isn't the only way to abuse Chrome's app mode.
Alternatively, the attacker can use a portable HTML file to launch the attack, embedding the "-app" parameter to point to a phishing site and distribute the files to targets.
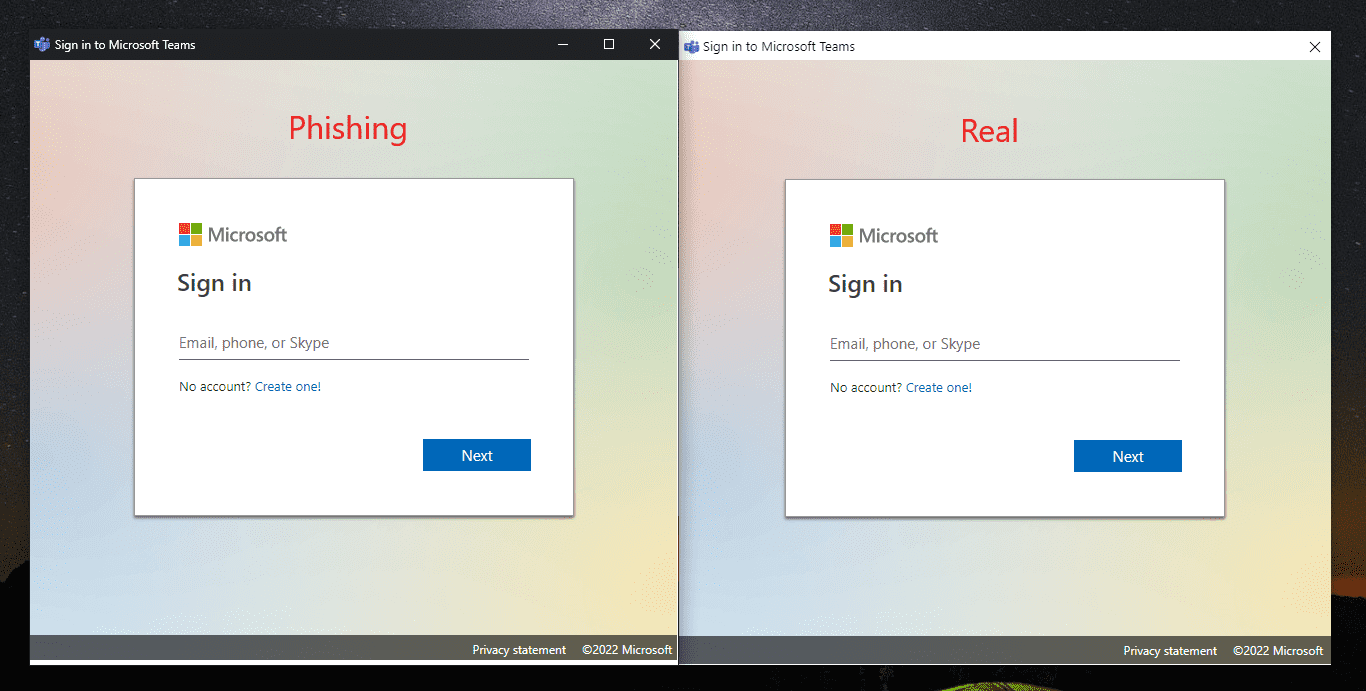 Phishing Microsoft Teams users with Chrome's app mode (mrd0x.com)
Phishing Microsoft Teams users with Chrome's app mode (mrd0x.com)Depending on the use case, an attacker can also use the Browser-in-the-Browser technique to insert a fake address bar by adding the required HTML/CSS, and creating clones of software, like, for example, Microsoft 365, Microsoft Teams, or even VPN login prompts.
The researcher also claims it's possible to launch the attack on macOS and Linux using the appropriate commands for these operating systems.
"/Applications/Google Chrome.app/Contents/MacOS/Google Chrome" --app=https://example.comThe phishing window can also receive action commands via JavaScript, like closing after the user enters their login credentials, accepting window resize requests, or rendering on a specific position on the screen.
The attack's potential is limited due to the requirement that Chromium app mode is launched locally on a device. This local access means that there is already some degree of compromise of the device.
However, once threat actors trick a target into launching a Windows shortcut, the potential for advanced phishing attacks is only limited by an attacker's creativity.
.png)














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·