Researchers have demonstrated a new type of fingerprinting technique that exploits a machine's graphics processing unit (GPU) as a means to track users across the web persistently.
Dubbed DrawnApart, the method "identifies a device from the unique properties of its GPU stack," researchers from Australia, France, and Israel said in a new paper," adding " variations in speed among the multiple execution units that comprise a GPU can serve as a reliable and robust device signature, which can be collected using unprivileged JavaScript."
A device fingerprint or machine fingerprint is information that is collected about the hardware, installed software, as well as the web browser and its associated add-ons from a remote computing device for the purpose of unique identification.
Fingerprints can be a double-edged sword. On the one hand, a fingerprint algorithm may allow a service provider (e.g., bank) to detect and prevent identity theft and credit card fraud. But it can also be abused to compile long-term records of individuals' browsing activity for targeted advertising.
Browser fingerprinting, in a similar vein, primarily relies on stitching together key pieces of information gleaned from the browser to create the fingerprint. The attributes run the gamut, spanning the browser's version, OS, timezone, screen, language, list of fonts, and even the way the browser renders text and graphics.
But browser fingerprints also suffer from one major drawback in that they can evolve over time, making it harder to track users for extended periods. That's where DrawnApart comes in.
It's not only the first-of-its-kind mechanism to explore and weaponize the manufacturing differences between identical GPUs, but also for reliably using the approach to distinguish between machines with identical hardware and software configurations, effectively undermining users' privacy.
At its core, the proposed tracking system involves measuring the time required to render different graphics primitives using the WebGL API, each targeting different execution units that comprise a GPU, to create a fingerprint trace that's then fed into a deep learning network to uniquely identify the specific device that generated it.
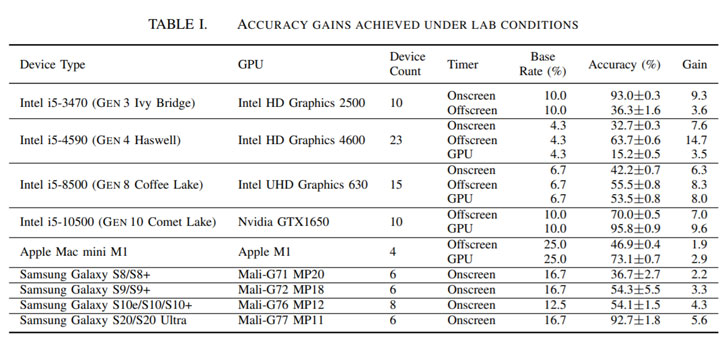
In an evaluation setup constituting 88 devices, including Windows 10 desktops, Apple Mac mini devices, and multiple generations of Samsung Galaxy smartphones, the researchers found that when used in conjunction with state-of-the-art fingerprint linking algorithms like FP-STALKER, DrawnApart extended the median average tracking period from 17.5 days to 28 days.
Countermeasures to block the GPU fingerprinting method range from script blocking to disabling WebGL, and limiting each web page to a single execution unit, or even turning off hardware-accelerated rendering — a move the researchers warn could severely affect usability and responsiveness.
Furthermore, the ongoing development into the WebGPU standard — currently available in canary releases of Google Chrome and Mozilla Firefox — is expected to drastically reduce the time taken to collect the fingerprint, prompting the academics to conclude that the "effects of accelerated compute APIs on user privacy should be considered before they are enabled globally."
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 2 years ago
144
2 years ago
144 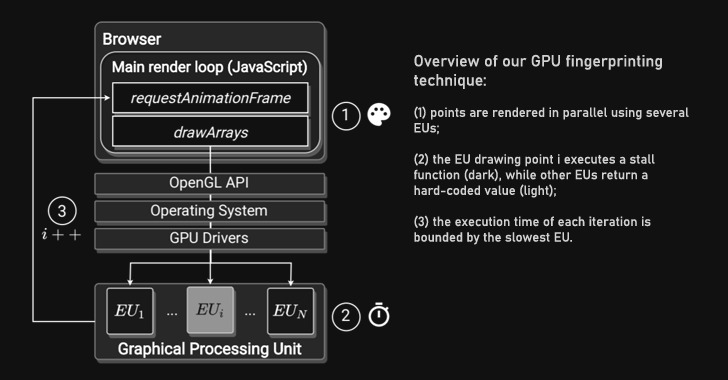

















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·