BOOK THIS SPACE FOR AD
ARTICLE ADTale of PII Information Leakage in Chennai Corporation Website!
Hello all, this is my first ever blog. Seriously, I’m not much into writing stuff but here I am with grammatical flaws. If I can, you can also do it. Go write something 🥲.
Hey people, I am Naveen Kumar. An independent security researcher from India. I occasionally hunt bugs and Meh, that’s all. Feel free to connect 👇
LinkedIn: https://www.linkedin.com/in/naveenkumar-16/
It all started with me, who got up late and went to office like a good little kiddo. But what isn’t good was the damn roads. Due to my “rush to office” mood and the conditions of Chennai roads, my poor Activa literally went through an off-roading adventure. After reaching the office, my colleague was also complaining about the same bad roads which she took. She also mentioned that we can file a complaint in some website, where they actually look into and fix the issue. So I thought of raising a complaint there.
Link for such cases: https://erp.chennaicorporation.gov.in/pgr/citizen/BeforeReg.do
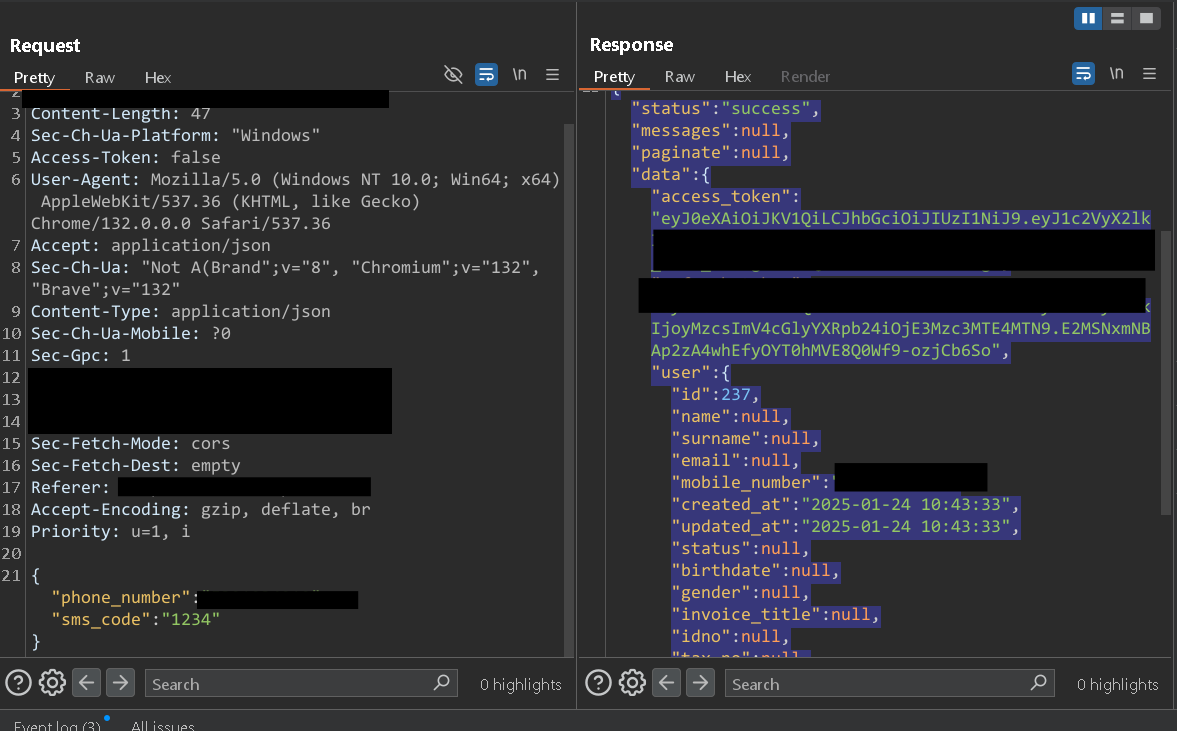
Well, it did. To register a complaint I must verify myself with OTP sent to my mobile number. OTP bypass ?? Nahh, I appreciate your mindset, but it’s not.
After registration you’ll be shown with a receipt like page, which has all your data like Name, Mobile Number, Address, e-mail ID, Pin-code, Complaint details, etc. I noticed something weird there. The URL looked like this : https://erp.chennaicorporation.gov.in/pgr/citizen/pgr_det.jsp?CmpID=<year>-<some-number-with-alphabets>. I was like “wait a minute, let me change the numbers and see what happens”.
https://erp.chennaicorporation.gov.in/pgr/citizen/ ?CmpID=2024-CD345N
But I got “404 Not Found” 😐. I think I got the value wrong. Then I saw my colleague’s complaint form and typed that value. Guess what, I can see her personal data as mentioned above. But the issue here is how am I going to guess the ID value. It’s almost very tough to brute-force because it has alphanumeric values. I was like
Later did I notice, that URL had a unique URI ‘pgr_det.jsp’. You’re right buddy, here comes the “Google Dork”. I crafted a google dork like this,
“pgr_det” site:erp.chennaicorporation.gov.in
Whoop Whoop!! I got around 70K results (Might includes duplicates).
What next ? Tried different scrappers, which can get the browser results into excel sheet and everything was paid version. I wasn’t rich to buy one, hence went with some trail version. It gave me list of top 100 urls that appeared in the search results. With that as input, I wrote a python script to hit requests and grab the responses and grep the needed info. It looked something like this,
User A--sxxxxx@gmail.com--9xxxxxx0--DR.YYY ROAD,TEYNAMPET,CHUser B--kxxxxx@gmail.com--9xxxxxx5--YYY STREET,PURASAIWAKKAM,CH
I wrote an e-mail to NCIIPC Responsible Vulnerability Disclosure Program attaching all the necessary proof of concept. At first they marked that as “invalid vulnerability”. Not sure why, but can such data be available to public? Let me know in the comments. Again I demonstrated the issue with the working video and data that could collect (obviously for testing purpose). Then they decided to accept and now it is fixed.
Protecting PII is crucial to prevent identity theft, which can lead to financial loss, and reputational damage. Ethical reporting plays a key role in securing sensitive data by ensuring vulnerabilities are responsibly disclosed and fixed. By following proper disclosure guidelines, we all can help organizations address security flaws without exposing users to risks. Safeguarding PII requires vigilance, awareness, and ethical responsibility, fostering trust in the digital world. Let me know if you have thoughts.
Until next time!! Bybeeeeee.
.png)
 5 hours ago
5
5 hours ago
5 

![OTP Bypass on [Redacted]: Contact Forms to Unauthorized Calls](https://miro.medium.com/v2/resize:fit:547/1*8IL2jXIbRemLJln3M9GsQw.png)











 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·