BOOK THIS SPACE FOR AD
ARTICLE ADWhile testing the contact support feature on [Redacted], I discovered a vulnerability that allowed me to bypass OTP verification through simple response manipulation. This issue not only allowed an attacker to impersonate a victim and interact with customer support but also enabled unauthorized phone calls to be initiated on behalf of the victim.
This write-up outlines how I exploited the vulnerability and escalated its impact by leveraging the “Get a Call” feature.
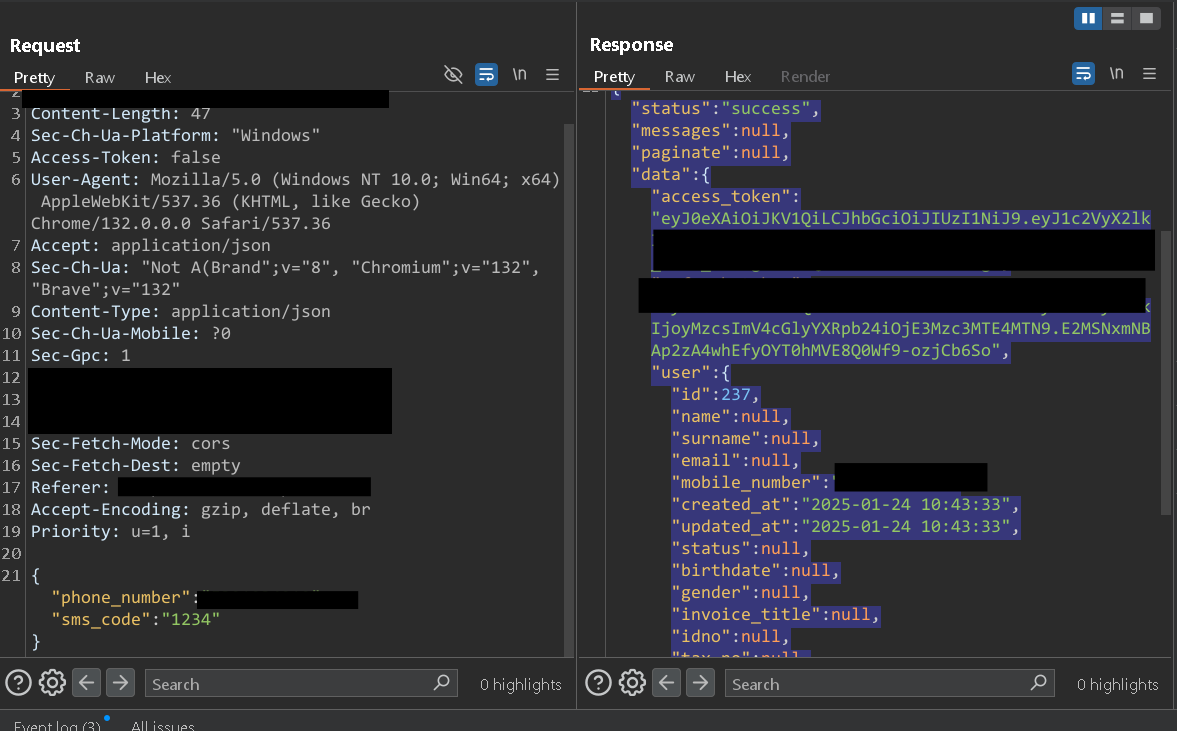
Navigate to https://redacted.com/help/ContactUs.Fill out the contact form, entering an email and phone number (attacker can use the victim’s details).The system sends a one-time password (OTP) to the provided email for verification.Enter any random OTP and intercept the request using Burp Suite or a similar tool.In Burp Suite, intercept the request and modify the response. Change the result from ‘false’ to ‘true’ to bypass OTP verification.Forward the modified request to the server.
Once OTP verification is bypassed, attackers can trigger an immediate call or chat from customer support without further verification.Clicking on “Get a Call” actually triggers a call to the provided phone number without any further verification.Since an attacker can submit a victim’s phone number and email, the victim will receive a call from [Redacted]’s official support line.📞 Unauthorized Calls: By triggering the “Get a Call” feature, attackers can have calls placed to victims or impersonate them.
🕵️♂️Impersonation: The attacker can bypass OTP and submit the contact form on behalf of any user.
⚡️Resource Exhaustion: By combining automation and manual actions, attackers can flood [Redacted]’s support system with hundreds of calls or chat requests, overwhelming resources and causing victims to receive unwanted calls.
Validate OTP on the Server Side: Make sure OTP verification is enforced consistently on the server side.Implement Rate Limiting: Prevent abuse by limiting the number of requests that can be made in a short time.Thanks for reading the report! Feel free to connect with me on LinkedIn for more.
.png)
 5 hours ago
5
5 hours ago
5 













 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·