BOOK THIS SPACE FOR AD
ARTICLE AD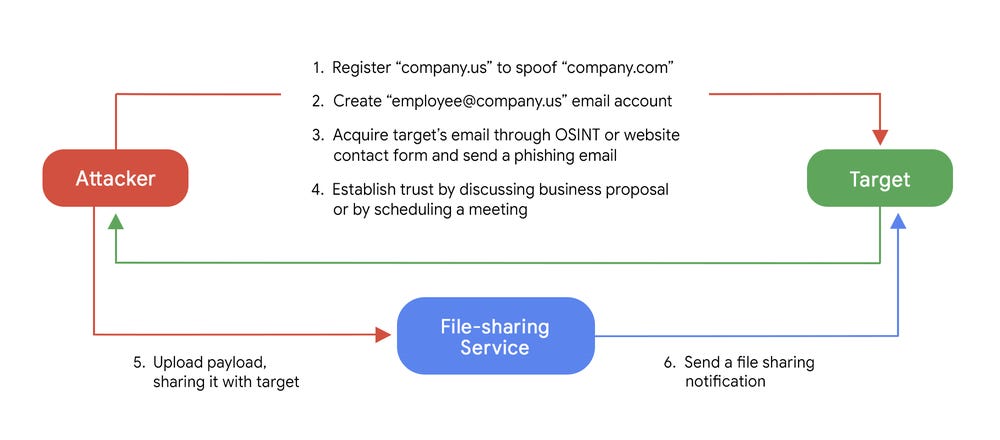 Image: Google
Image: Google
Google's Threat Analysis Group has detailed a group it has labelled as Exotic Lily that breached a target and sold off the gained access.
The preferred method for gaining targets is spear phishing, with the group sending around 5,000 emails a day, and setting up similar domains with different TLDs -- such as using example.co for example.com users -- in an effort to fool those on the receiving end.
It also began with fake personas, but recently started ripping publicly available data from sites like RocketReach and CrunchBase to impersonate users.
The group also used public file-sharing sites including TransferNow, TransferXL, WeTransfer, or OneDrive to pass payloads onto users and make it harder for defenders to detect, since the sites are legitimate.
"Investigating this group's activity, we determined they are an initial access broker who appear to be working with the Russian cyber crime gang known as Fin12 (Mandiant, FireEye) / Wizard Spider (CrowdStrike)," Google said.
"Exotic Lily is a resourceful, financially motivated group whose activities appear to be closely linked with data exfiltration and deployment of human-operated ransomware such as Conti and Diavol."
The group also appears to maintain a high degree of work-life balance, as Google said the activity it has seen is typical of a 9 to 5 job in eastern or central Europe, with little activity on weekend.
Although the group has relationships with ransomware gangs, Google said Exotic Lily is a separate entity that is only interested in access, with other groups doing the ransomware operations.
Off the back of its discovery, Google said it would have additional Gmail warning for emails originating from website contact forms, improve its spoofing identification, and adjust the reputation of email file sharing notifications.
.png)
 2 years ago
140
2 years ago
140 














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·