PenTesting laboratory deployed as IaC with Terraform on AWS. It deploys a Kali Linux instance accessible via ssh & wireguard VPN. Vulnerable instances in a private subnet.
NOTE:
Ids only defined for region "eu-west-1" For other regions, kali ami id must be specified and metasploitable3 id (after building it)Changelog
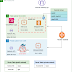
[2021-06-02] AMI IDs changed to use Kali 2021.2 [2021-03-10] Use new Kali version 2021.1Diagram
Components
Kali 2021.2 instance (private key is saved into kali.pem) Wireguard VPN service: client file client_vpn.wg Accessible via ssh/scp Public Subnet 10.0.0.5/24 Vulnerable machine "Metasploitable" (ami build is public) Private subnet 10.0.1.5/24 More vulnerable labs/machines/docker (to-be-done)Features added
User management Automatically create non privileged users in kali instance with rsa Wireguard VPN client file per user Command line audit logging in syslog auditd enabled with sudo_log and users_log keys for auditing user actions (see also ausearch command) ToDO: Forward terminal audit to CloudWatch or an S3 Bucket with write once policyHow-To
Requirements: Terraform CLI install guide AWS CLI install guide $PATH configured for AWS CLI & Terraform AWS account and configure credentials via aws cli: aws configure Kali Linux Subscription in AWS Marketplace (version 2020.04) Metasploitable3 AMI image previously built (public AMI available for eu-west-1 region) seeDeploy
Enable/disable vulnerable instances to be deployed setting 0 or 1 in variables.tf:type = map
default = {
#"instance" = 0 or 1, to disable or enable
"metasploitable3" = 1
"dvca" = 0
}
description = "Control which EC2 instances are deployed, 0 for none or 1"
}
terraform plan
terraform apply -auto-approve
Outputs
Terraform outputs will show following entries:
ssh connection command for kali user (root via sudo) wireguard client file for kali user will be automatically retrieved from kali server scp command to retrieve wireguard client file (just in case defined terraform local-exec command fails) For each of the normal users created in Kali instance Private key file for ssh connection Wireguard client file for VPN connectivityUsage
Either connect to Kali via ssh or wireguard:
SSH: (Only command line) Use autogenerated private key (see terraform output)ssh -i kali.pem -o StrictHostKeyChecking=no -o IdentitiesOnly=yes [email protected]${KALI_IP}
scp -i kali.pem -o StrictHostKeyChecking=no IdentitiesOnly=yes [email protected]${KALI_IP}:/home/kali/client_vpn.wg .
####
(local_kali)$ sudo apt-get install –y wireguard
(local_kali)$ sudo gedit /etc/wireguard/wg0.conf # copy contents of client_vpn.wg
(local_kali)$ sudo chmod 700 /etc/wireguard/wg0.conf
(local_kali)$ sudo wg-quick up wg0
(local_kali)$ ping 10.0.0.5 # test connectivity with kali instance in AWS
Destroy
References
rapid7 / metasploitable3 - license Kali 2021.2 AWS Marketplace terraform-aws-ec2-kali-linux.png)
 3 years ago
179
3 years ago
179 















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·