BOOK THIS SPACE FOR AD
ARTICLE ADSQL truncation is a web application vulnerability in which an input is truncated (deleted) when added to the database due to surpassing the maximum defined length. The database management system truncates any newly inserted values to fit the width of the designated column size.
So, where can we find this vulnerability ?? it can be found in any web application that allows users to sign up/register for new accounts.
If the database considers spaces as valid characters between inputs and doesn’t do any trimming before storing the values, an attacker can create a duplicate accounts of an existing user like ‘’admin’’ with many additional spaces and characters — ‘’admin++++++random’’ that are too long to be stored in the specified column and gets deleted after passing the max length.
📍So, instead of storing “admin++++++random’’ as an entry, the database will truncate the second half to fit it in the column (‘’admin +++++’’).
Next time an attacker logs in to the application with the admin account, the database will search for all matching accounts and will consider them valid for logging in. Therefore any entry with username as admin with space or without is a valid entry that can be used to authenticate to the application.
“admin” == ‘admin +++++’
📌 One thing to keep in mind when creating a duplicate account as an admin, it doesn’t guarantee that you will have admin privileges. Some databases use permission columns to specify the account privileges.
In this post, we will exploit an application with SQL truncation vulnerability. The steps will be demonstrated on the Book machine from Hack the box. This machine is part of Scripting Track.
Usually, when I start testing a web application, I go through a list of common issues to check for in my enumeration phase to narrow the scope of the testing and give more attention to interesting components of the application. Below is part of the checklist I have for enumerating login pages.
Forgot Password
Enumerate users through Forgot Password feature.
Signups:
Enumerate users/email addresses through signing-up with existing users like “admin” , “Administrator” or “admin@admin.com”Test for second degree SQL injectionTest for SQL truncation through signing up with duplicate accounts with spaces to see if the application allows that.SQL injections:
Try SQL Injections — manually first with common special characters or with SQLmap to test for vulnerable parameters.I tried everything in the above list one by one, all of them didn’t work except for creating duplicate accounts with spaces.
I started off testing the fields by signing up with different values to understand if there any checks on them. The username field and password don’t check for duplication. I tried to use the same username and password with different emails and noticed the accounts get created immediately, which means that checks are only on the email field.


Great, that narrows down to one field to test.
I created a new account with an email address of ‘r3dbuck3t@bucket.com’. Fired up Burp Suite and intercepted the Signup request. I added encoded spaces “+++++” and a random name “hacker” 😈 , and send it to the application.

As we see, we got a 200 response as the account was created, and I was able to log in as ‘r3dbuck3t@bucket.com’’. Though I signed up as ‘r3buck3t@bucket.com+++++hacker’’.

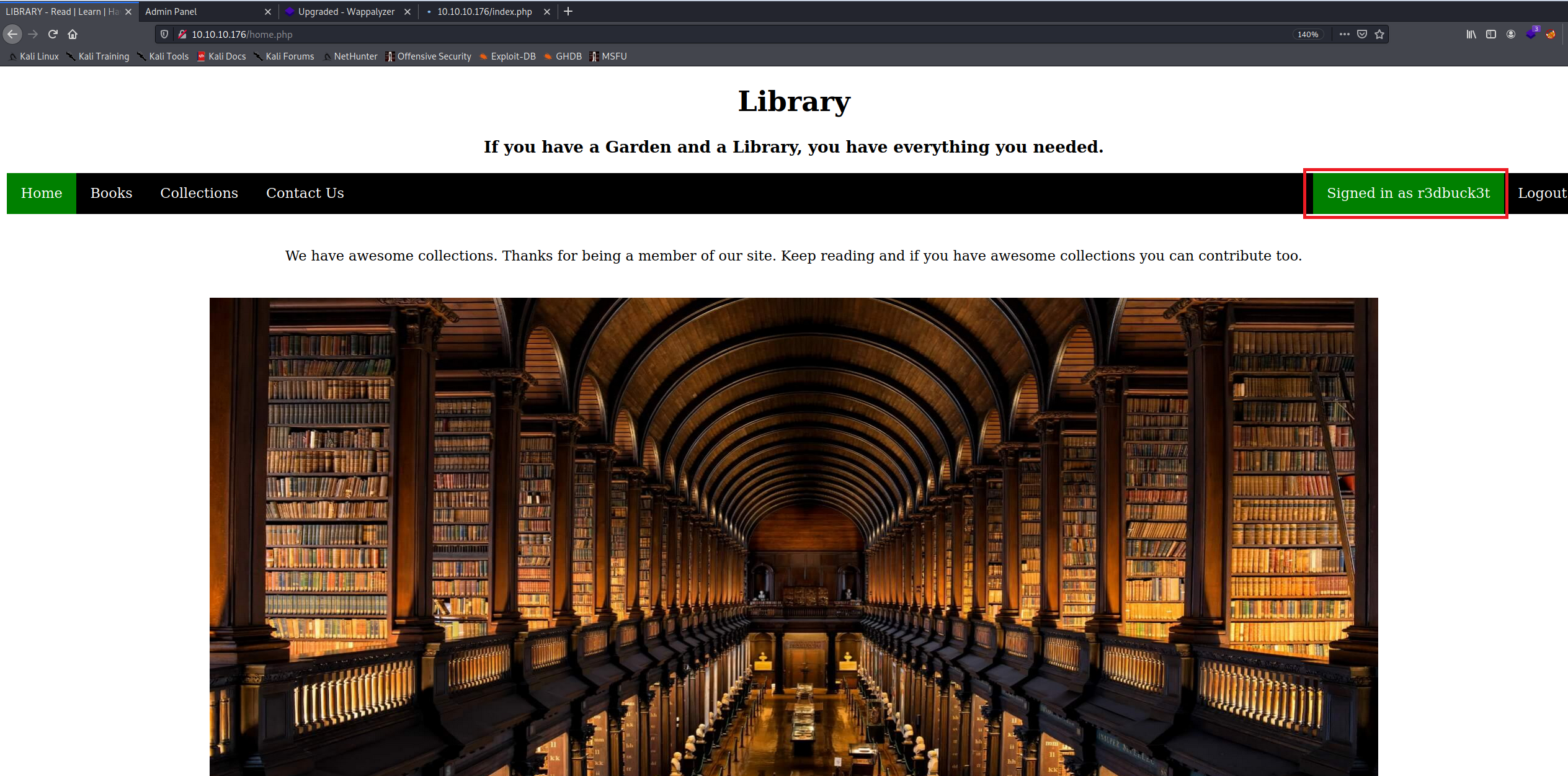
After logging into the application, I found the admin’s email on the Contact Us page. I was thinking, why not following the same steps in creating duplicate account for “admin@book.htb” and see if that will get us to authenticate as the admin.
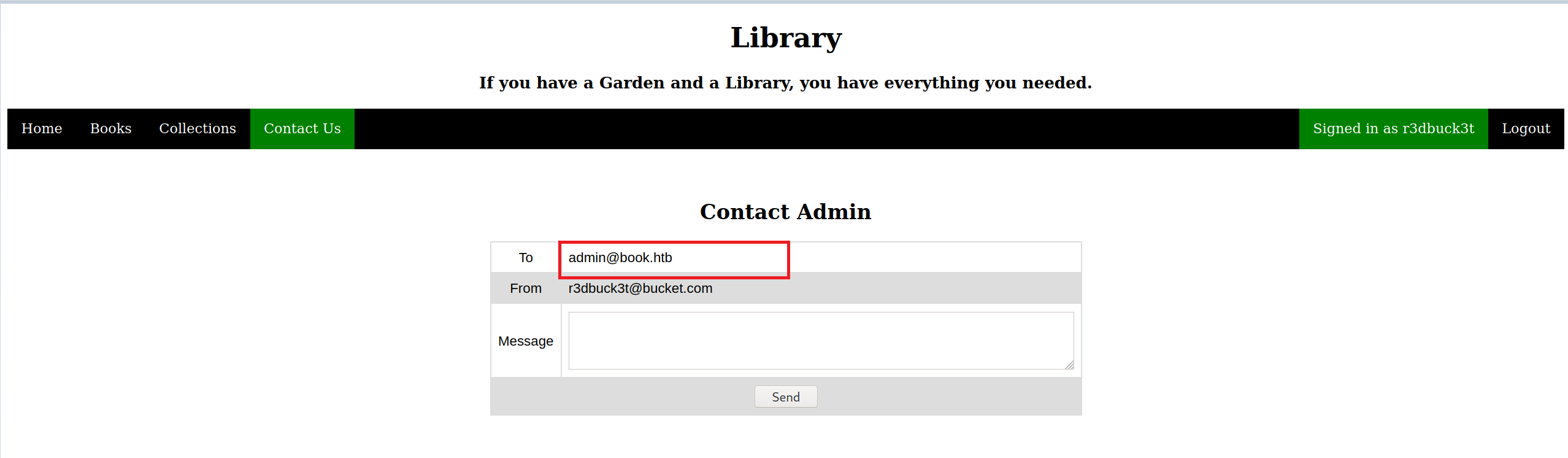
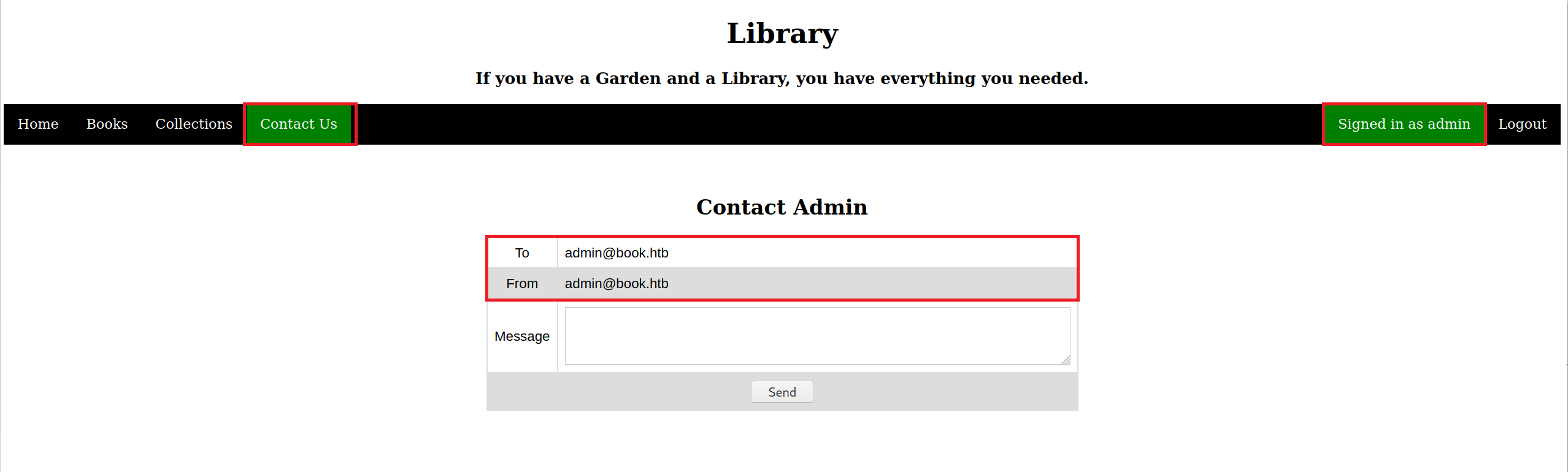
Again, intercepted the request, added the encoded spaces and a name to the email address — “admin@book.htb++++++hacker” with a password of “r3dbuck3t”.


Even though, the account was created and I was able to log in, I am still in the user role. As I mentioned at the beginning of the post, using the truncation technique in hijacking accounts is not guaranteed to get you a privileged accounts.
Sometimes, there are other flags set in the database to distinguish the privileged users from regular ones.
But it is worth trying 😃

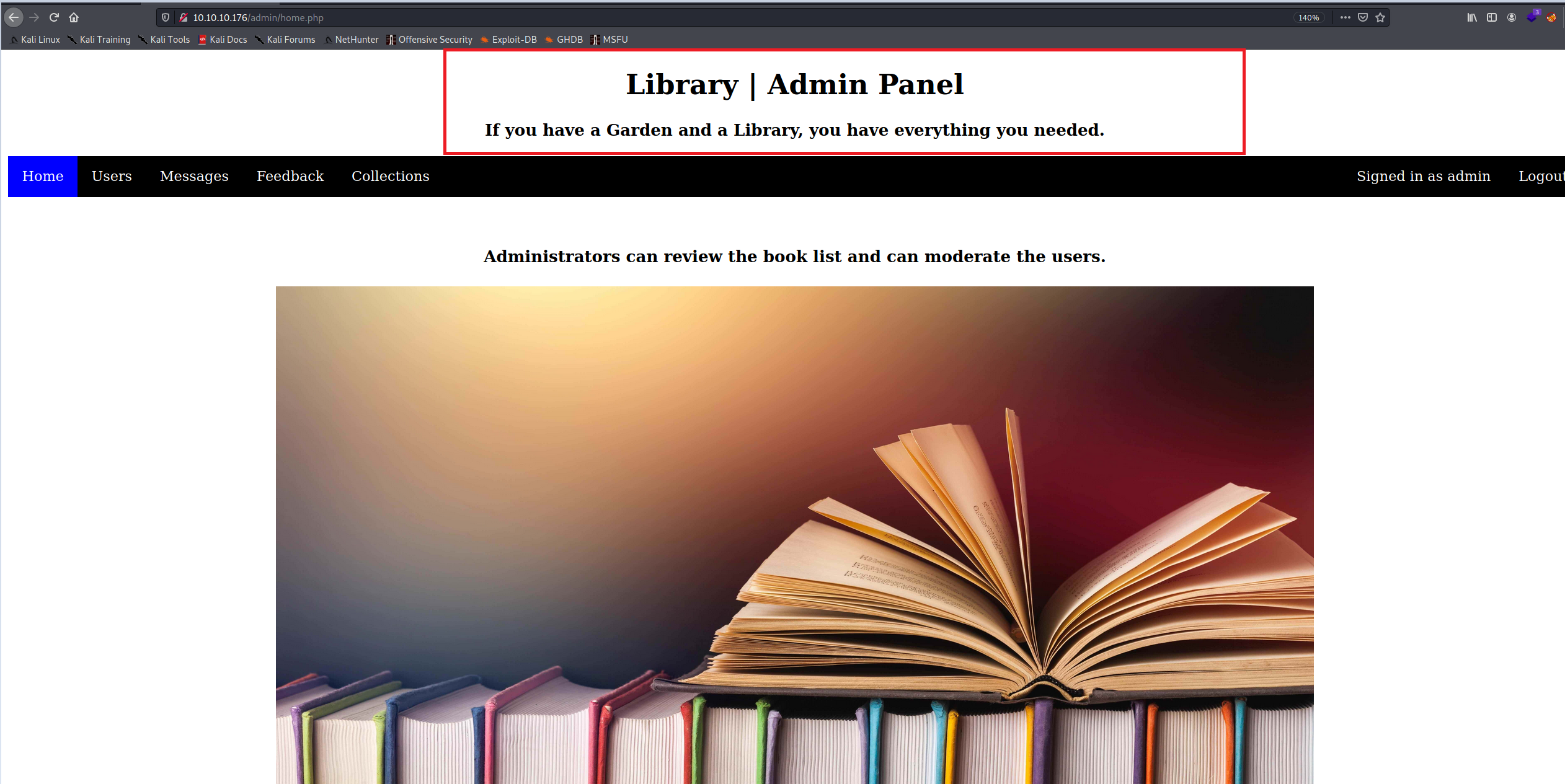
Now, for this machine, there was another portal called “Admin Portal” that I discovered while conducting directory enumeration with Gobuster.
I tried to log in with the same email “admin@book.htb” and the password “r3dbuck3t”, and YESS, I was able to login to the admin portal as an admin this time.
That’s all for today. I’ll see you in another post.
🛎️ The SQL checklist mentioned above can be found at R3d-Buck3T — Notion.
.png)
 3 years ago
202
3 years ago
202 














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·