Cloud Security Operations
What is Cloud Sniper?
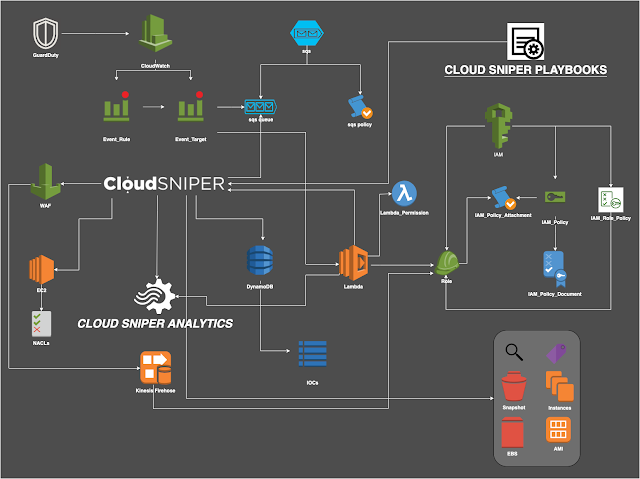
Cloud Sniper is a platform designed to manage Security Operations in cloud environments. It is an open platform which allows responding to security incidents by accurately analyzing and correlating native cloud artifacts. It is to be used as a Virtual Security Operations Center (vSOC) to detect and remediate security incidents providing a complete visibility of the company's cloud security posture.
With this platform, you will have a complete and comprehensive management of the security incidents, reducing the costs of having a group of level-1 security analysts hunting for cloud-based Indicators of Compromise (IOC). These IOCs, if not correlated, will generate difficulties in detecting complex attacks. At the same time Cloud Sniper enables advanced security analysts integrate the platform with external forensic or incident-and-response tools to provide security feeds into the platform.
The cloud-based platform is deployed automatically and provides complete and native integration with all the necessary information sources, avoiding the problem that many vendors have when deploying or collecting data.
Cloud Sniper receives cloud-based and third-parties feeds and automatically responds protecting your infrastructure and generating a knowledge database of the IOCs that are affecting your platform. This is the best way to gain visibility in environments where information can be bounded by the Shared Responsibility Model enforced by cloud providers.
To detect advanced attack techniques, which may easily be ignored, the Cloud Sniper Analytics module correlates the events generating IOCs. These will give visibility on complex artifacts to analyze, helping both to stop the attack and to analyze the attacker's TTPs.
Cloud Sniper is currently available for AWS, but it is to be extended to others cloud platforms.
Automatic infrastructure deployment (for AWS)
WIKI => HOW IT WORKS
Cloud Sniper releases
1. Automatic Incident and Response 1. WAF filtering 2. NACLs filtering 3. IOCs knowledge database. 4. Tactics, Techniques and Procedures (TTPs) used by the attacker 2. Security playbooks 1. NIST approach 3. Automatic security tagging 4. Cloud Sniper Analytics 1. Beaconing detection with VPC Flow Logs (C2 detection analytics)Upcoming Features and Integrations
1. Security playbooks for cloud-based environments 2. Security incidents centralized management for multiple accounts. Web Management UI 3. WAF analytics 4. Case management (automatic case creation) 5. IOCs enrichment and Threat Intelligence feeds 6. Automatic security reports based on well-known security standards (NIST) 7. Integration with third-party security tools (DFIR).png)
 4 years ago
144
4 years ago
144 
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·