BOOK THIS SPACE FOR AD
ARTICLE ADThe National Security and Defense Council of Ukraine claims the data leak has exposed millions of top websites to cyber attacks.
A few weeks ago, we saw a disruption in Cloudflare’s services forcing several top websites to go offline worldwide. At the time though, the company claimed that they had not been attacked in any way and it was due to a bad software deployment issue.
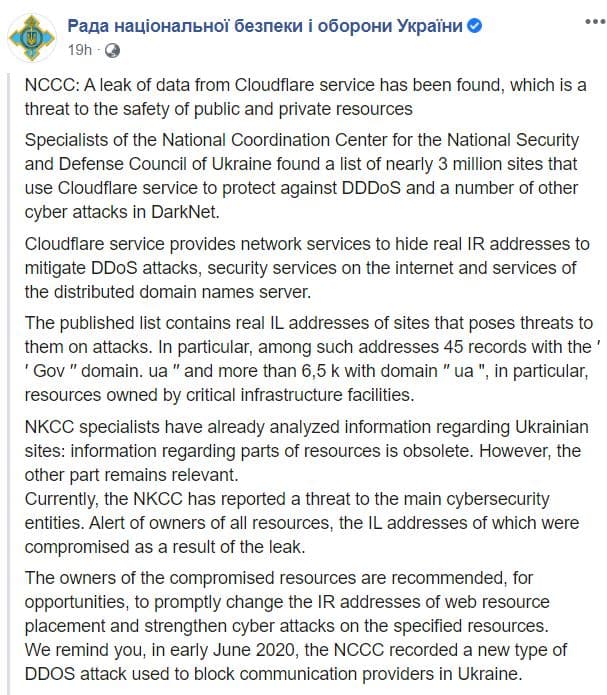
However, just yesterday, the National Cyber Security Coordination Center of Ukraine has alleged that a data leak has occurred from Cloudflare resulting in the real IP addresses of almost 3 million sites being exposed on the dark web.
If true, this could be a major blow to the service provider since it markets itself as protecting the real IP addresses of its clients in order to protect them from Distributed Denial of Service (DDoS) attacks. Moreover, it also raises the question of whether the outage earlier was because of the alleged attack?
See: 8chan down after Cloudflare & hosting firms boots it off
Currently, the records published by the agency include 45 of its own records featuring the “gov.ua” top-level domain (TLD) and 6500 records featuring the “.ua” TLD indicating that a good number of Ukrainian sites were exposed including those of critical infrastructure facilities.
In this regard, the National Security and Defense Council has alerted the owners of the specific addresses recommending them to take prompt action in the form of changing their IP details and being on the lookout for further cyber-attacks.
Furthermore, the agency has stated that in the data seen by its experts of the exposed sites, some of the information is outdated but other parts still remain a concern.
However, HackRead.com has identified a website that also claims to host approximately a list of 2,593,320 IP addresses which it claims are real IPs of websites powered by Cloudflare. The website also states that the list is updated with new IP addresses every 3 weeks and the purpose of it is to:
“Uncovering bad guys hiding behind Cloudflare.”
Homepage of the website that claims to “Uncovering bad guys hiding behind Cloudflare.” Image credit: Hackread.com
1 of 3
It is unclear whether there is a link between the website and Ukraine’s claim and so this still remains a mystery.
Statement from Cloudflare
In a comment to Hackread.com, Cloudflare has denied leaking any data. Laurel Toney from Cloudflare’s explained that “We have investigated in detail an alleged leak of DNS information concerning Cloudflare’s customers. The information posted on social media is not the result of a leak or breach of our systems. The published data is available through standard DNS queries on the open Internet, rather than the result of a leak or breach.”
“Cloudflare provides different services to different customers. Some customers use us for security services. Some use us for performance services. Some customers make use of both. The published information reflects a small fraction of Cloudflare customers who either use Cloudflare only for DNS resolution or only for performing services and therefore have not configured Cloudflare to secure their origin server,” Laurel explained.
“If these customers intended to use Cloudflare for security services, they may have misconfigured the security settings on their origin server or have misconfigured the proxy settings on some of their DNS records.”
Laurel explained that “If a customer intended to use Cloudflare for security services and has identified that their origin server information was published online, they should follow this link to ensure their origin is secured.
See: Cloudflare Launches Android and iOS version of 1.1.1.1 DNS Service
For the time being, Cloudflare still remains one of the most trusted web security companies and so we should wait for their statement before confirming what the Ukrainian government has claimed. In either case, we have reached out to Cloudflare and will continue updating you. Stay tuned.
Did you enjoy reading this article? Do like our page on Facebook and follow us on Twitter.
.png)













 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·