BOOK THIS SPACE FOR AD
ARTICLE ADHello everyone, This is my 6th Blog first about Bugs and Bug bounty
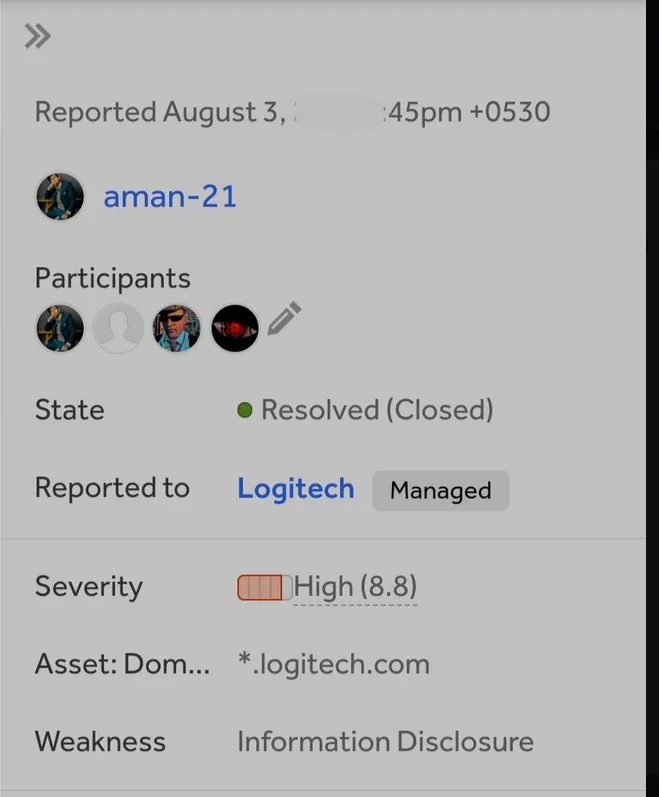
There are a lot of bugs but one which is a little easy to find without much technical expertise is Sensitive Information Disclosure.
Overview of this Vulnerability
This is a vulnerability where some information which is very sensitive/critical/confidential is publicly available or disclosed where it shouldn’t be. For Example,
This is one example of the vulnerability where the Sensitive Information like DB_USERNAME, DB_PASSWORD is disclosed Publicly.
So finally the reason you are reading this -> The DORKS
These are below DORKS:
.png)
 6 hours ago
7
6 hours ago
7 












 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·