BOOK THIS SPACE FOR AD
ARTICLE ADGitHub is a goldmine for bug bounty hunters and security researchers, with countless repositories containing sensitive information — API keys, credentials, private tokens, and more. All it takes is the right search query (a.k.a. dorking) to uncover these treasures.
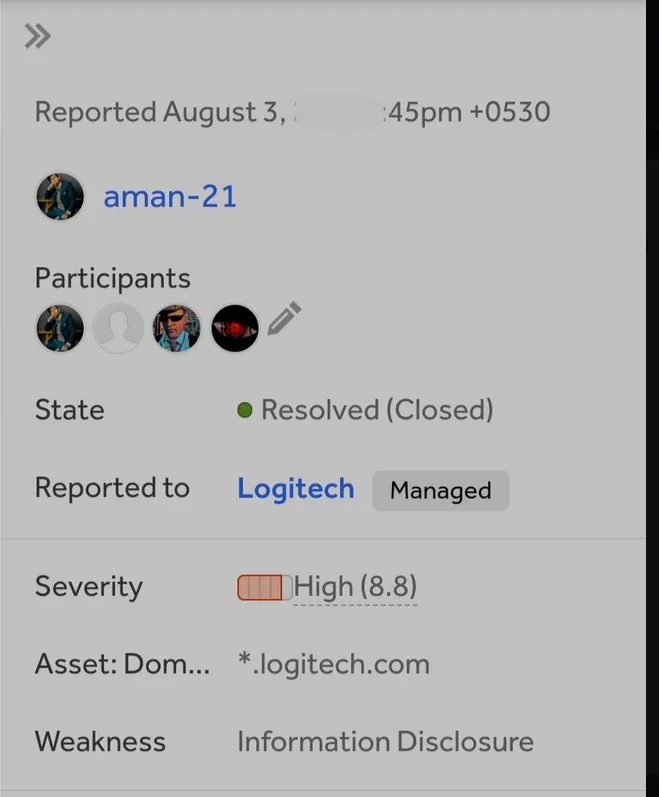
Hi, I’m Akash (myselfakash20), a bug bounty hunter and a cybersecurity researcher. Recently, I used GitHub dorking to find a critical vulnerability for a bug bounty program. By locating an exposed AWS access key in a public repository, I demonstrated the potential impact and earned $200 in just a few hours.
In this write-up, I’ll show you how I did it, share a collection of effective GitHub dorks, and guide you through both manual and automated processes to uncover sensitive information responsibly. Let’s dive in!
GitHub dorking involves crafting targeted search queries to uncover publicly exposed secrets in repositories. This is done by leveraging GitHub’s advanced search syntax to hunt for sensitive files, configurations, or keywords.
How I Earned $200 Using GitHub Dorking
.png)
 6 hours ago
8
6 hours ago
8 












 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·