use ELF binary file
Download ELF zip file release , unzip and use by command ./ecapture --help.
Linux kernel version >= 4.18 Enable BTF BPF Type Format (BTF) (Optional, 2022-04-17)check your server BTF config:
grep CONFIG_DEBUG_INFO_BTF CONFIG_DEBUG_INFO_BTF=y">
[email protected]:~$# uname -r4.18.0-305.3.1.el8.x86_64
[email protected]:~$# cat /boot/config-`uname -r` | grep CONFIG_DEBUG_INFO_BTF
CONFIG_DEBUG_INFO_BTF=y
tls command
capture tls text context. Step 1:
Step 2:
bash command
capture bash command.
uprobe HOOK
openssl hook
eCapture hookSSL_write \ SSL_read function of shared library /lib/x86_64-linux-gnu/libssl.so.1.1. get text context, and send message to user space by eBPM map.
Probes: []*manager.Probe{
{
Section: "uprobe/SSL_write",
EbpfFuncName: "probe_entry_SSL_write",
AttachToFuncName: "SSL_write",
//UprobeOffset: 0x386B0,
BinaryPath: "/lib/x86_64-linux-gnu/libssl.so.1.1",
},
{
Section: "uretprobe/SSL_write",
EbpfFuncName: "probe_ret_SSL_write",
AttachToFuncName: "SSL_write",
//UprobeOffset: 0x386B0,
BinaryPath: "/lib/x86_64-linux-gnu/libssl.so.1.1",
},
{
Section: "uprobe/SSL_read",
EbpfFuncName: "probe_entry_SSL_read",
AttachToFuncName: "SSL_read",
//UprobeOffset: 0x38380,
BinaryPath: "/lib/x86_64-linux-gnu/libssl.so.1.1",
},
{
Section: "uretprobe/SSL_read",
EbpfFuncName: "probe_ret_SSL_read",
AttachToFuncNa me: "SSL_read",
//UprobeOffset: 0x38380,
BinaryPath: "/lib/x86_64-linux-gnu/libssl.so.1.1",
},
/**/
},
{
Section: "uprobe/SSL_write",
EbpfFuncName: "probe_entry_SSL_write",
AttachToFuncName: "SSL_write",
//UprobeOffset: 0x386B0,
BinaryPath: "/lib/x86_64-linux-gnu/libssl.so.1.1",
},
{
Section: "uretprobe/SSL_write",
EbpfFuncName: "probe_ret_SSL_write",
AttachToFuncName: "SSL_write",
//UprobeOffset: 0x386B0,
BinaryPath: "/lib/x86_64-linux-gnu/libssl.so.1.1",
},
{
Section: "uprobe/SSL_read",
EbpfFuncName: "probe_entry_SSL_read",
AttachToFuncName: "SSL_read",
//UprobeOffset: 0x38380,
BinaryPath: "/lib/x86_64-linux-gnu/libssl.so.1.1",
},
{
Section: "uretprobe/SSL_read",
EbpfFuncName: "probe_ret_SSL_read",
AttachToFuncNa me: "SSL_read",
//UprobeOffset: 0x38380,
BinaryPath: "/lib/x86_64-linux-gnu/libssl.so.1.1",
},
/**/
},
bash readline.so hook
hook /bin/bash readline symbol name.
Linux Kernel: >= 4.18.
Tools
golang 1.16 gcc 10.3.0 clang 9.0.0 cmake 3.18.4 clang backend: llvm 9.0.0 pahole >= v1.13 kernel config:CONFIG_DEBUG_INFO_BTF=y (Optional, 2022-04-17)command
compile without BTF
eCapture support NO BTF with command make nocore to compile on 2022/04/17.
make nocore
bin/ecapture --help
bin/ecapture --help
See CONTRIBUTING for details on submitting patches and the contribution workflow.
.png)
 2 years ago
156
2 years ago
156 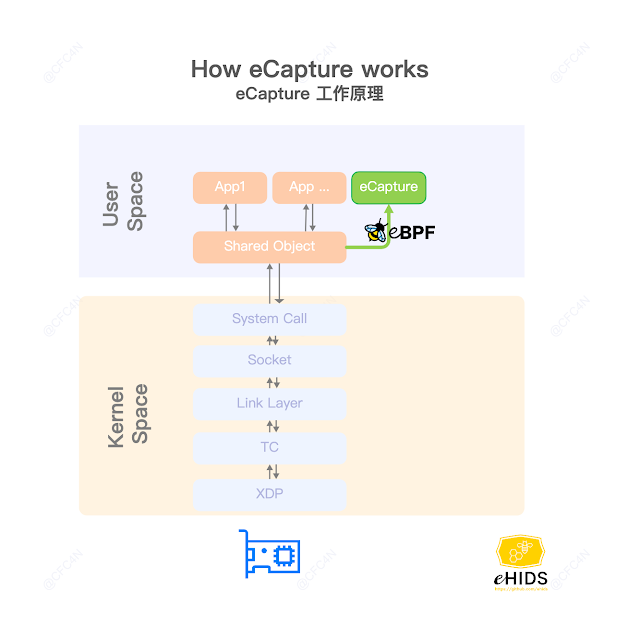


















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·