BOOK THIS SPACE FOR AD
ARTICLE AD
A new phishing campaign that uses the fake CAPTCHA websites we reported about recently is targeting hotel staff in a likely attempt to access customer data, according to research from ThreatDown.
Here’s how it works: Cybercriminals send a fake Booking.com email to a hotel’s email address, asking them to confirm a booking.
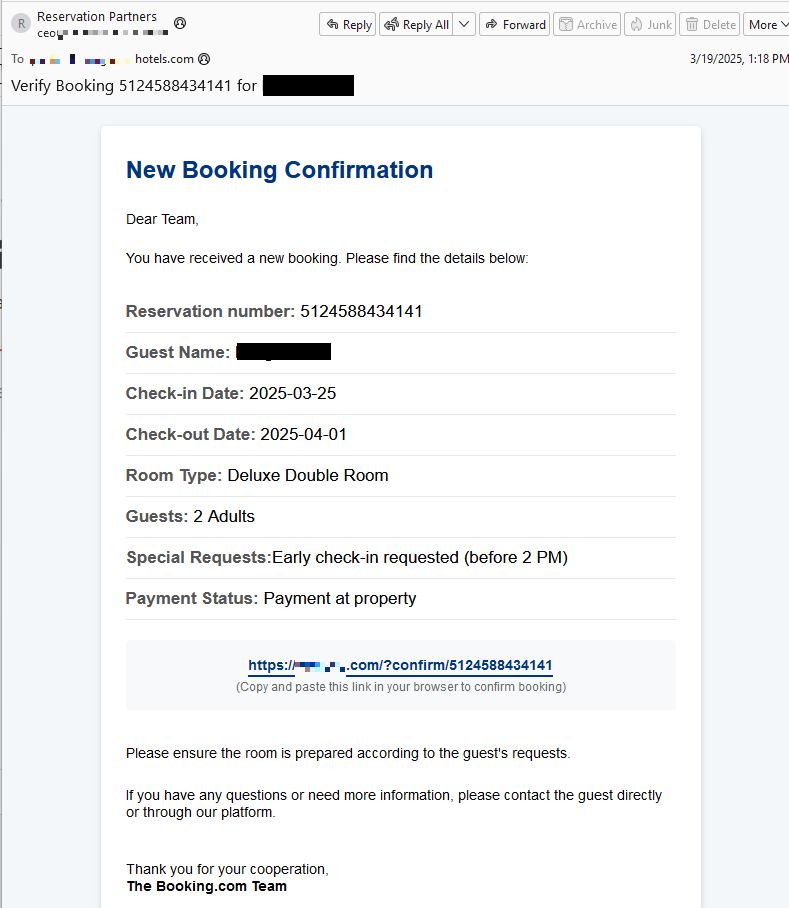
“Dear Team,
You have received a new booking. Please find the details below:
Reservation number: 5124588434141
Guest Name: Margit Kainz
Check-in Date: 2025-03-25
Check-out Date: 2025-04-01
Room Type: Deluxe Double Room
Guests: 2 Adults
Special Requests:Early check-in requested (before 2 PM)
Payment Status: Payment at property
{link to landing page}
(Copy and paste this link in your browser to confirm booking)
Please ensure the room is prepared according to the guest’s requests.
If you have any questions or need more information, please contact the guest directly or through our platform.
Thank you for your cooperation,
The Booking.com Team”
The email is sent only a few days before the check-in-date, which is very likely to create a sense of urgency—a common tactic of scammers.
But if the hotel staff were to copy and paste the URL into the browser address bar they will be greeted by this fake CAPTCHA website.

When they check the box, they’ll then see “verification” instructions that will effectively infect their system.
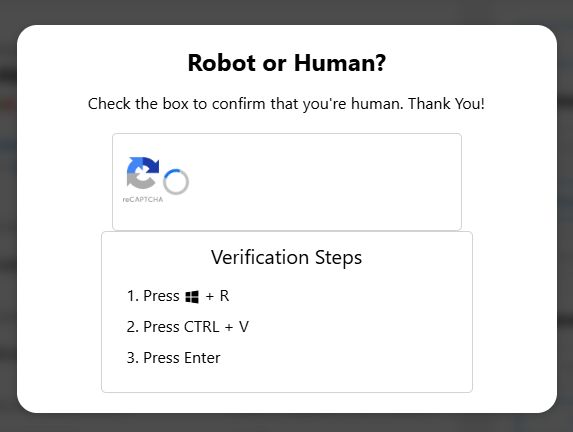
“Verification steps
Press Windows Key + R.
Press Ctrl + V.
Press Enter”
As we explained in more detail here, these instructions will infect their Windows system with an information stealer or Trojan.
What the hotel staff would actually be doing is copy and pasting a mshta command into the Run prompt and then executing the command, which then fetches a remote file and then runs it on their system.
We don’t know the exact plans of the criminals once they have gained control over the system, but it’s highly likely they’re after customer payment details and other personal data: Data that is very valuable to them and can be traded on the dark web.
There isn’t much you can do to protect your own data in situations like these, when cybercriminals are attacking the companies that hold your personal information. However, there are a few things you can do to lower your risk.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·