BOOK THIS SPACE FOR AD
ARTICLE ADMy previous blog post was dedicated to very interesting malware that is called Wingbird. This malware has been used by NEODYMIUM cyber espionage group and contains rootkit to execute sensitive and important operations for attackers in a system. The first sample used rootkit for injection malicious code into Winlogon with removing ESET driver hooks in kernel SSDT, while second deploys rootkit for bypassing FS sandbox of several security products. Both droppers analyzed in 32-bit environment, while their behaviour in 64-bit Windows versions are interesting too and different from what we have seen in the 32-bit versions.
In 64-bit system, the dropper doesn't resort to the use of kernel mode rootkit (obviously, due to DSE restrictions) for injection malicious code & data into trusted Winlogon process. Instead this, it uses special trick for masking its malicious activity and for performing injection. The dropper uses copy of trusted LSASS process (executable file) and forces it to load malicious dll with standart name that is imported by LSASS.
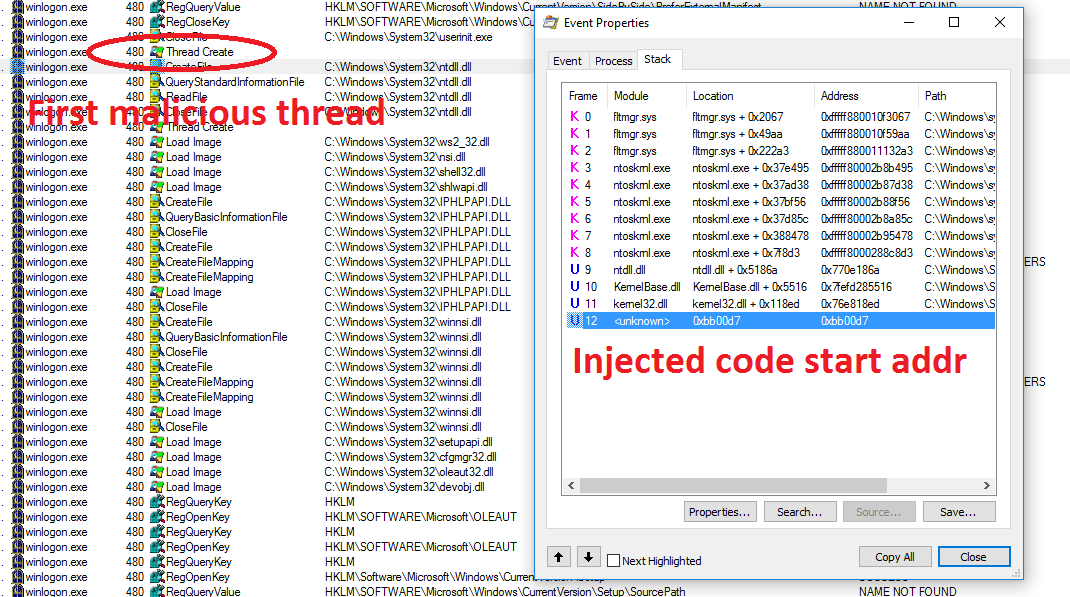
64-bit GMER anti-rootkit tool demonstrates injection anomalies into Winlogon and Svchost, where malicious code is located.
The presence of virtual memory regions into Winlogon with the protection attribute PAGE_EXECUTE_READWRITE is an indicator that the process was compromised.
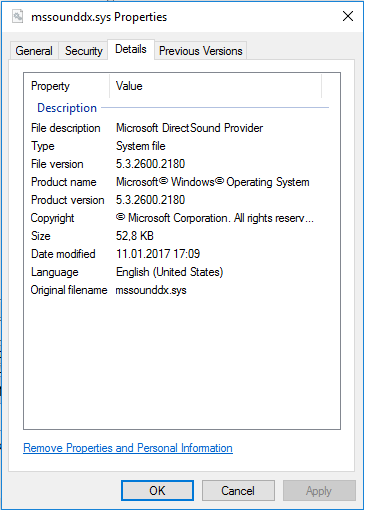
As I already noted in previous blog post, Wingbird malware shares similarities with another malware that is called Finfisher. For example, in malicious PE-file that was dumped from Winlogon memory region, we can see reference to name of Finfisher rootkit (mssounddx.sys).
After lsass service started, it injects code into winlogon and with help of ProcMon boot logging we can identify first actions that come from malicious code.
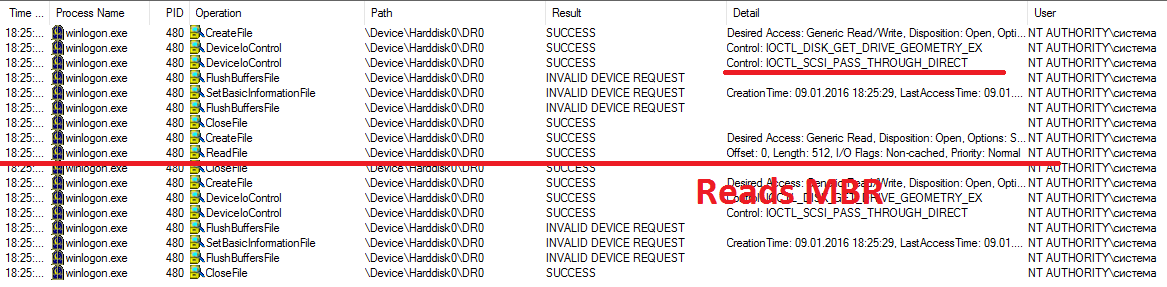
After some preliminary actions, malicious code into Winlogon tries to communicate with hard disk on low level, it requests disk geometry info and sends SCSI control code for reading data. In 32-bit version it uses rootkit to perform this operation.
It also checks presence of Finfisher files. See details in Symantec blog post here.
The following indicators show similarities between Wingbird and Finfisher.
I was able to get 32-bit version of mssounddx.sys rootkit. As you can see on screenshot below, authors masked its file as legitimate Microsoft driver.
Like Wingbird rootkit, Finfisher rootkit is protected from statical analysis. The code from DriverEntry and other functions in mssounddx.sys are representing a loader that decrypts content of BIN resource, where 2nd encrypted driver is located.
Rootkit code does following actions in DriverEntry.
1. It is looking for corresponding BIN resource into .rsrc section.
2. It allocates memory block from kernel pool and copies into it content of BIN resource with size 0xc180 (encrypted driver).
3. Decrypts data in allocated pool block.
4. Prepares PE-file of encrypted driver for work: applies fixups, fills some internal variables (ptrs to import functions).
5. Passes control to DriverEntry of decrypted driver.
Second driver uses following kernel functions.
Code injection.
Next picture demonstrates logic of 2nd driver execution.
Start of shellcode looks like.
Conclusion
As you can see from the analysis, we haven't seen something new in Finfisher rootkit. Like other drivers that are used by attackers, it is intended only for one purpose - for injection malicious code into Winlogon process. Nevertheless, authors use some anti-analysis tricks, including, driver encryption and obfuscation some data that driver keeps in kernel memory.
.png)




























 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·