Credits
Author: M3n0sD0n4ld
Twitter: @David_Uton
GooFuzz is a script written in Bash Scripting that uses advanced Google search techniques to obtain sensitive information in files or directories without making requests to the web server.
$ git clone https://github.com/m3n0sd0n4ld/GooFuzz.git
$ cd GooFuzz
$ chmod +x GooFuzz
$ ./GooFuzz -h
$ cd GooFuzz
$ chmod +x GooFuzz
$ ./GooFuzz -h
Menu
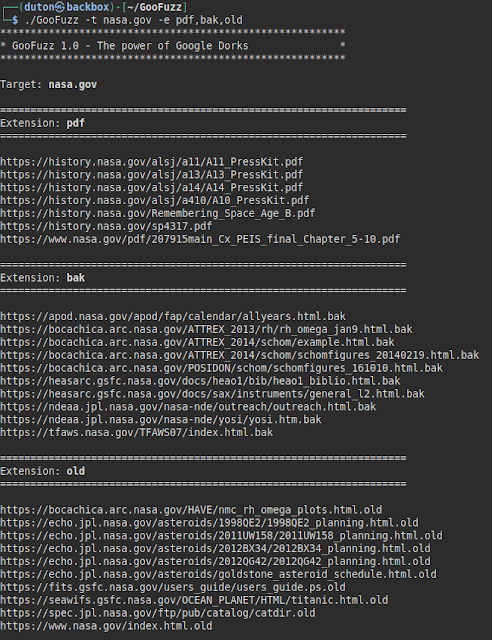
Lists files by extensions separated by commas.
Lists files by extensions contained in a txt file.
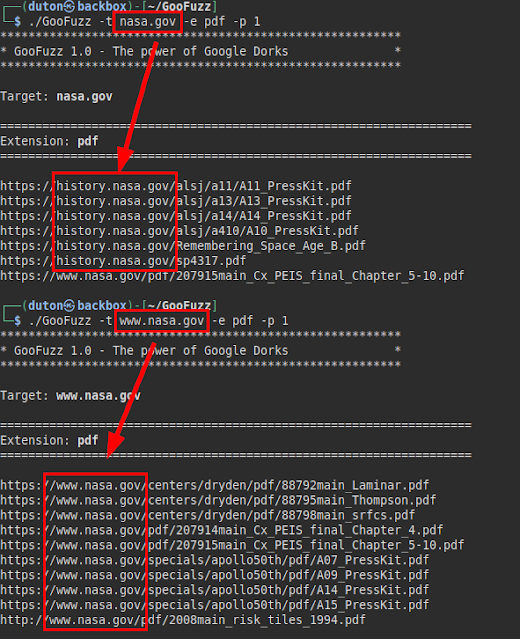
Lists files by extension, either subdomain or domain and showing the first Google result.
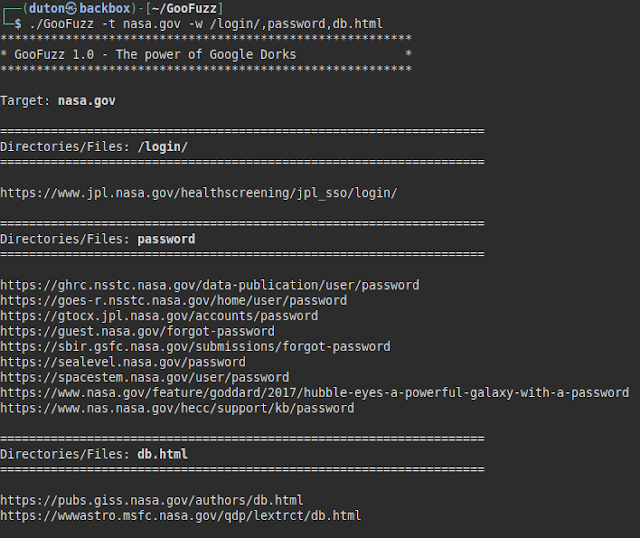
List files, directories and even parameters by means of a wordlist (it is recommended to use only very small files).
Lists directories and files by specifying paths, words or file names.
I am not responsible for the misuse of the tool. Google Search has mechanisms to prevent abusive use or detection of suspicious activity. If at any time the tool does not show results, Google has temporarily blocked you (e.g. Captcha). All the information obtained is public and through Google results. Logically, the searches are in Google, so it leaves no evidence in the logs of the target's server. And very important, if you see a file, directory, subdomain, etc... Indexed in Google, does not mean that it still exists on the server (or it does ;)).If you like the tool, find it useful in your work, Bug Bounty or as a hobby, you could help me like this:
Tell your friends and co-workers about it. Contribute new ideas or help me to improve it by correcting bugs from here. How? Do you want to buy me a coffee? Thank you very much!.png)
 2 years ago
160
2 years ago
160 



















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·