BOOK THIS SPACE FOR AD
ARTICLE AD
A threat actor claims to have hacked T-Mobile's servers and stolen databases containing the personal data of approximately 100 million customers.
The alleged data breach first surfaced on a hacking forum yesterday after the threat actor claimed to be selling a database for six bitcoin (~$280K) containing birth dates, driver's license numbers, and social security numbers for 30 million people.
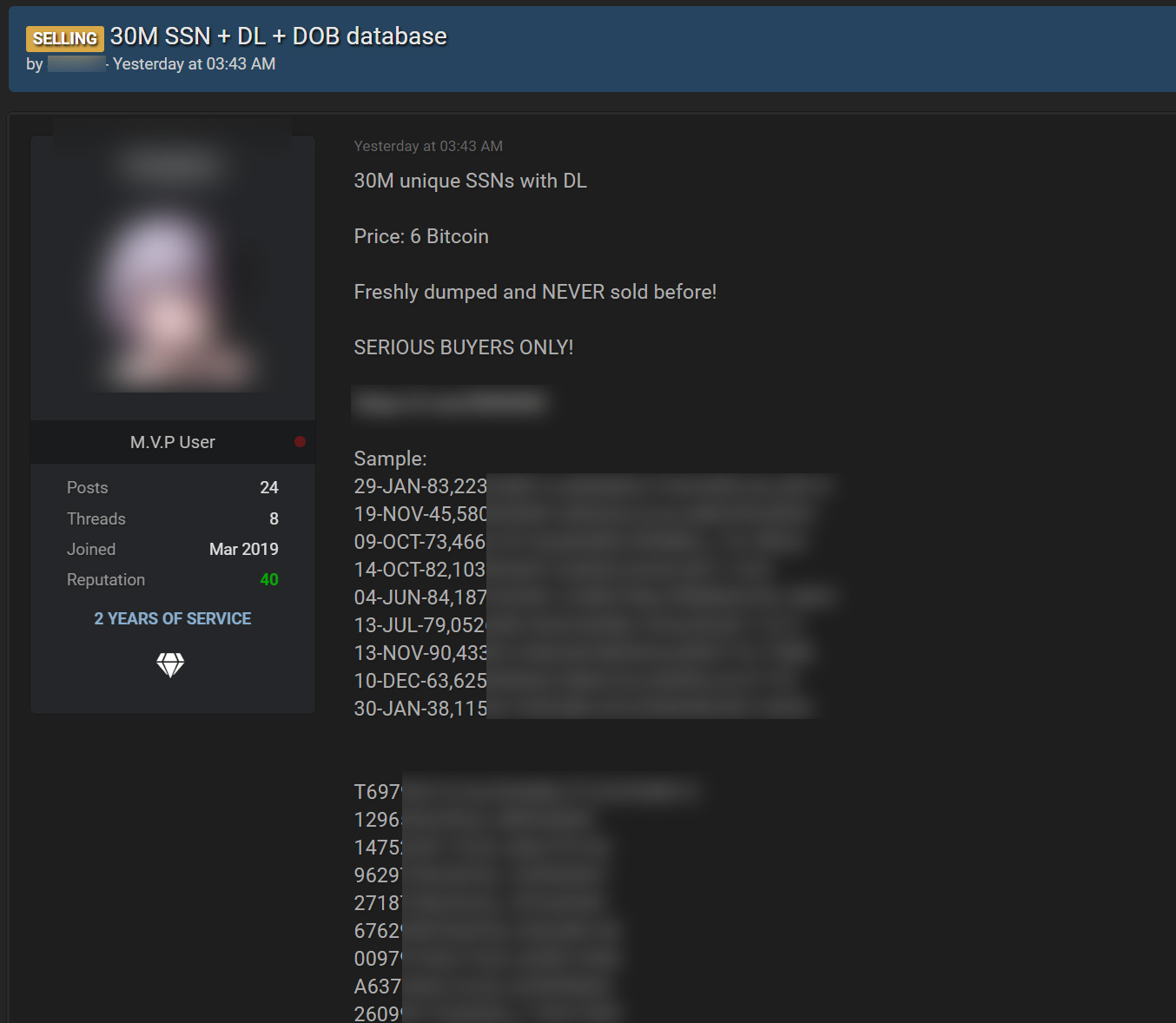 Forum post selling T-Mobile data
Forum post selling T-Mobile dataWhile the forum post does not state the origins of the data, the threat actor told BleepingComputer that they took it from T-Mobile in a massive server breach.
The threat actor claims to have hacked into T-Mobile's production, staging, and development servers two weeks ago, including an Oracle database server containing customer data.
This stolen data allegedly contains the data for approximately 100 million T-Mobile customers and can include customers' IMSI, IMEI, phone numbers, customer names, security PINs, Social Security numbers, driver's license numbers, and date of birth.
"Their entire IMEI history database going back to 2004 was stolen," the hacker told BleepingComputer.
An IMEI (International Mobile Equipment Identity) is a unique number used to identify mobile phones, while an IMSI (International mobile subscriber identity) is a unique number associated with a user on a cellular network.
Cybersecurity intelligence firm Cyble told BleepingComputer yesterday that the threat actor claims to have stolen multiple databases totaling approximately 106GB of data, including T-Mobile's customer relationship management (CRM) database.
Motherboard, who first reported on this breach, said they could verify that data samples provided by the threat actor belonged to T-Mobile customers.
When asked if they attempted to ransom the stolen data to T-Mobile, the threat actors said they never contacted the company and decided to sell it on forums where they already have interested buyers.
BleepingComputer has contacted T-Mobile but did not receive a response to our query at this time. However, Motherboard received a reply stating they are investigating the alleged data breach.
"We are aware of claims made in an underground forum and have been actively investigating their validity. We do not have any additional information to share at this time," T-Mobile told Motherboard.
T-Mobile hacked for revenge
The threat actors told Alon Gal, CTO of cybercrime intelligence firm Hudson Rock, that they performed this hack to damage US infrastructure.
"This breach was done to retaliate against the US for the kidnapping and torture of John Erin Binns (CIA Raven-1) in Germany by CIA and Turkish intelligence agents in 2019," the threat actors told Gal in a conversation.
"We did it to harm US infrastructure."
Binns is a resident of Turkey who sued the FBI, CIA, and Department of Justice in 2020.
The complaint alleges that Binn was tortured and harassed by the US and Turkish governments and is seeking to compel the USA to release documents regarding these activities under the Freedom of Information Act.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·