BOOK THIS SPACE FOR AD
ARTICLE ADHackers impersonate ESET in phishing attacks targeting Israeli organizations. Malicious emails, claiming to be from ESET, deliver wiper malware. Security researcher Kevin Beaumont exposes the attack. ESET denies direct compromise and points to partner involvement.
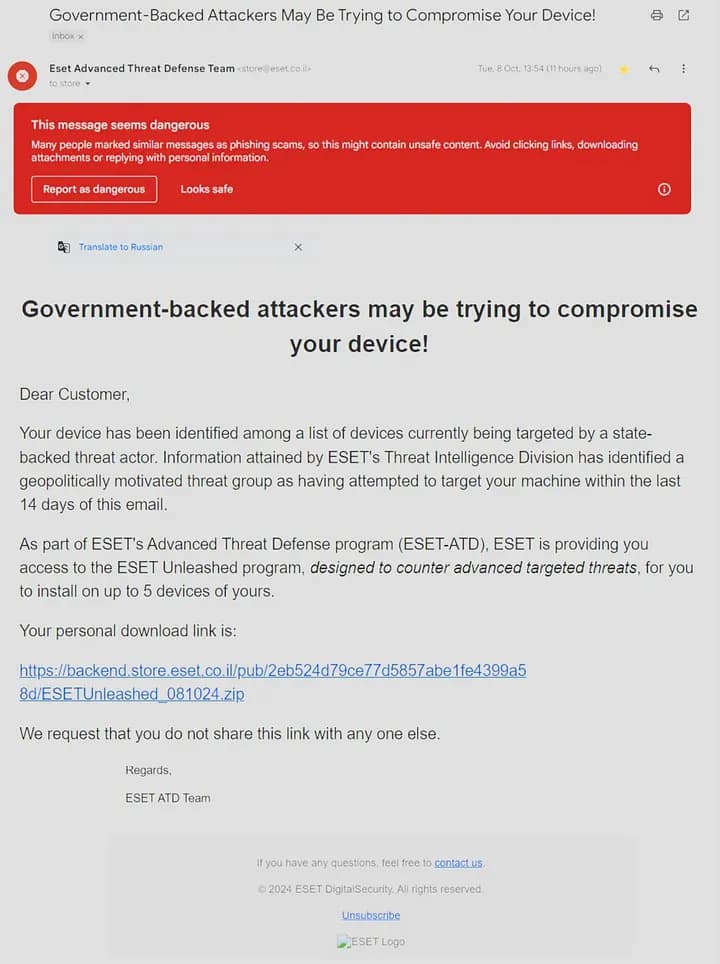
In a recent cyberattack, hackers targeted Israeli organizations by impersonating the cybersecurity firm ESET. The attackers sent phishing emails impersonating Slovak-based ESET, warning recipients of state-backed hackers targeting their devices.
The emails included a link to download a non-existent “ESET Unleashed program” that claimed to counter the attack. Clicking the link downloaded a ZIP file containing wiper malware, designed to wipe data from the infected device.
Security researcher Kevin Beaumont raised the alarm noting that the hackers had successfully breached ESET’s defences and were hosting malicious files on their servers. The emails were flagged as dangerous by Google, but many recipients may have fallen victim to the deception.
The email, styled as ESET Advanced Threat Defense Team, and the downloads, styled as ESET Unleashed, contain various ESET DLLs and a file called setup.exe and call out to a legitimate org in Israel-www.oref.org.il. If a victim opened the ZIP file and ran the malware, it would proceed to delete files and data from their device. However, the malware required a physical PC and time to activate its destructive capabilities.
“ESET Israel definitely got compromised, this thing is fake ransomware that talks to an Israeli news org server for whatever reason,” Beaumont wrote in his blog post.
ESET responded to the incident by acknowledging that a security incident had occurred at their partner company in Israel, Comsecure, denying that their own infrastructure had been compromised. The official statement from ESET on X (Twitter) read:
“We are aware of a security incident which affected our partner company in Israel last week. Based on our initial investigation, a limited malicious email campaign was blocked within ten minutes. ESET technology is blocking the threat and our customers are secure. ESET was not compromised and is working closely with its partner to further investigate and we continue to monitor the situation.”
The phishing campaign specifically targeted cybersecurity personnel within Israeli organizations, suggesting that the attackers were aiming to disrupt the country’s digital defences. The emails were sent on October 8th, the day after the anniversary of Hamas’ and other Palestinian militant groups’ armed incursions into Israel. A user on the ESET Security Forum quickly noticed the suspicious email and reported it.
The attackers gained access to Comsecure’s infrastructure likely through a security vulnerability or social engineering techniques. They then crafted carefully designed phishing emails that closely resembled ESET’s official style and branding.
The specific threat actor behind the campaign remains unclear. However, the tactics used are similar to those employed by the pro-Palestine group Handala, which recently targeted Israeli organizations with wiper malware and other cyberattacks. Cybersecurity firm Trellix has described Handala’s attacks as sophisticated and suggested possible links to Iran.
The ESET impersonation campaign is now blocked but it highlights the ongoing threat of phishing attacks and raises concerns about the security of ESET’s partner infrastructure and the potential for future attacks. To prevent similar attacks, organizations should prioritize verifying the authenticity of messages and implement advanced security measures.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·