BOOK THIS SPACE FOR AD
ARTICLE ADEmail is still the most popular way for malware and other threats to be delivered, with more than 75% of threats being sent through email messages, according to the latest HP Wolf Security Threat Insights Report.
The report -- covering the first half of 2021 -- is compiled by HP security analysts based on customers who opt to share their threat alerts with the company.
HP's researchers found that there has been a 65% rise in the use of hacking tools downloaded from underground forums and filesharing websites from H2 2020 to H1 2021. Some of the tools are able to solve CAPTCHA challenges using computer vision techniques.
Some of the most targeted sectors include manufacturing, shipping, commodity trading, maritime, property and industrial supplies.
Ian Pratt, global head of security at HP, said the proliferation of pirated hacking tools and underground forums are allowing previously low-level actors to pose serious risks to enterprise security."
"Simultaneously, users continue to fall prey to simple phishing attacks time and time again. Security solutions that arm IT departments to stay ahead of future threats are key to maximizing business protection and resilience," Pratt said.
The report notes that affiliates of Dridex -- which is now the top malware family isolated by HP Wolf Security -- have been selling access to breached organizations to other threat actors, including ransomware groups.
Some criminal groups are now also using CryptBot malware to deliver banking trojan DanaBot, and cyberattackers are increasingly targeting business executives.
"In March 2021, HP Wolf Security isolated a multi-stage Visual Basic Script malware campaign targeting senior executives. The targets received a malicious ZIP attachment by email, named using their first and last names," the report said.
"It is likely the threat actor obtained employee names and email addresses from publicly available information online. The archives contained an obfuscated VBS downloader that downloads a second VBS script from a remote server to the user's %TEMP% folder. The first stage script was heavily obfuscated and had a low detection rate -- only 21% of anti-virus scanners on VirusTotal detected it as malicious."
The company also found a résumé-themed malicious spam campaign targeted shipping, maritime, logistics and related companies in Italy, Japan, Chile, UK, Pakistan, US, and the Philippines. These attacks exploit a Microsoft Office vulnerability to deploy the commercially-available Remcos RAT and gain backdoor access to infected computers, according to HP.
"Threat actors are continuing to exploit old vulnerabilities in Microsoft Office, underlining the need for enterprises to patch out-of-date Office versions in their environments," HP's researchers wrote.
"We saw a 24% increase in CVE-2017-11882 exploits in H1 2021 compared to H2 2020. Otherwise, there was no significant change in the vulnerabilities exploited by attackers over the reporting period compared to H2 2020."
Alex Holland, senior malware analyst at HP, said the cybercrime ecosystem continues to develop and transform, with more opportunities for petty cybercriminals to "connect with bigger players within organized crime, and download advanced tools that can bypass defenses and breach systems."
"We're seeing hackers adapt their techniques to drive greater monetization, selling access on to organized criminal groups so they can launch more sophisticated attacks against organizations," Holland said.
"Malware strains like CryptBot previously would have been a danger to users who use their PCs to store cryptocurrency wallets, but now they also pose a threat to businesses. We see infostealers distributing malware operated by organized criminal groups – who tend to favor ransomware to monetize their access."
The report adds that threats downloaded using web browsers rose by 24%, driven mostly by cryptocurrency mining software.
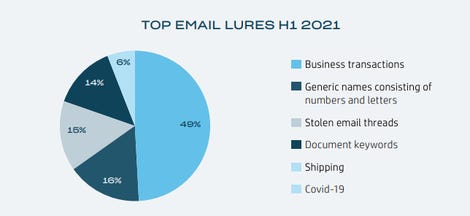
Nearly half of all email phishing lures used invoices and business transactions while another 15% were replies to intercepted email threads. The days of cybercriminals using COVID-19 as a lure seem to have ended, considering less than 1% of emails used the pandemic and there was a 77% drop from H2 2020 to H1 2021 in its usage.
 HP
HP
The report attributes the stolen email thread technique to Emotet, which was taken down by law enforcement agencies in January.
"We saw large Emotet campaigns targeting Japanese organizations using lures created from stolen email threads – a technique called email thread hijacking. Following the takedown, the proportion of malware being distributed via Word documents fell significantly because Emotet's operators preferred to use a Wordbased downloader," the report said.
Archive files, spreadsheets, documents and executable files were the most common types of malicious attachments. According to HP's team, almost 35% of malware captured had not been previously known.
"Cybercriminals are bypassing detection tools with ease by simply tweaking their techniques. We saw a surge in malware distributed via uncommon file types like JAR files – likely used to reduce the chances of being detected by anti-malware scanners," Holland added. "The same old phishing tricks are reeling in victims, with transaction-themed lures convincing users to click on malicious attachments, links and web pages."
Pratt explained that as cybercrime becomes more organized, and smaller players can easily obtain effective tools and monetize attacks by selling on access, there's no such thing as a minor breach. He noted that the endpoint continues to be a huge focus for cybercriminals.
"Their techniques are getting more sophisticated, so it's more important than ever to have comprehensive and resilient endpoint infrastructure and cyber defense," Pratt said. "This means utilizing features like threat containment to defend against modern attackers, minimizing the attack surface by eliminating threats from the most common attack vectors – email, browsers, and downloads."
.png)
 3 years ago
136
3 years ago
136 














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·