BOOK THIS SPACE FOR AD
ARTICLE AD
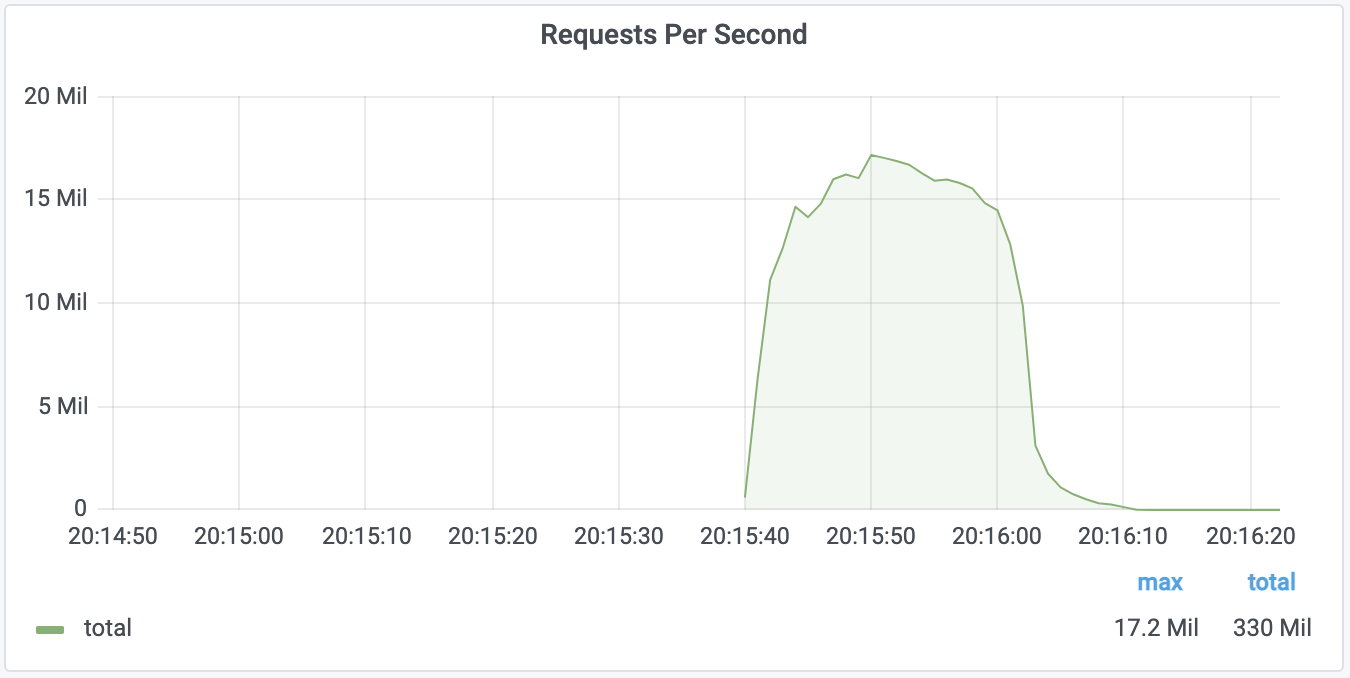
A distributed denial-of-service (DDoS) attack earlier this year takes the top spot for the largest such incident, peaking at 17.2 million requests per second (rps).
The attack was recorded by Cloudflare’s DDoS protection systems and accounted for almost 70% of all average rate for legitimate HTTP traffic for the second quarter of 2021.
Short-lived DDoS attack
The assault lasted less than a minute in July and sent more than 330 million requests targeting an organization in the financial industry.
It peaked at 17.2 million but maintained a steady push around 15 million for about 15 seconds.
While the duration of the attack is not impressive, its force does indicate that the threat actors in the DDoS business are increasing their capabilities.
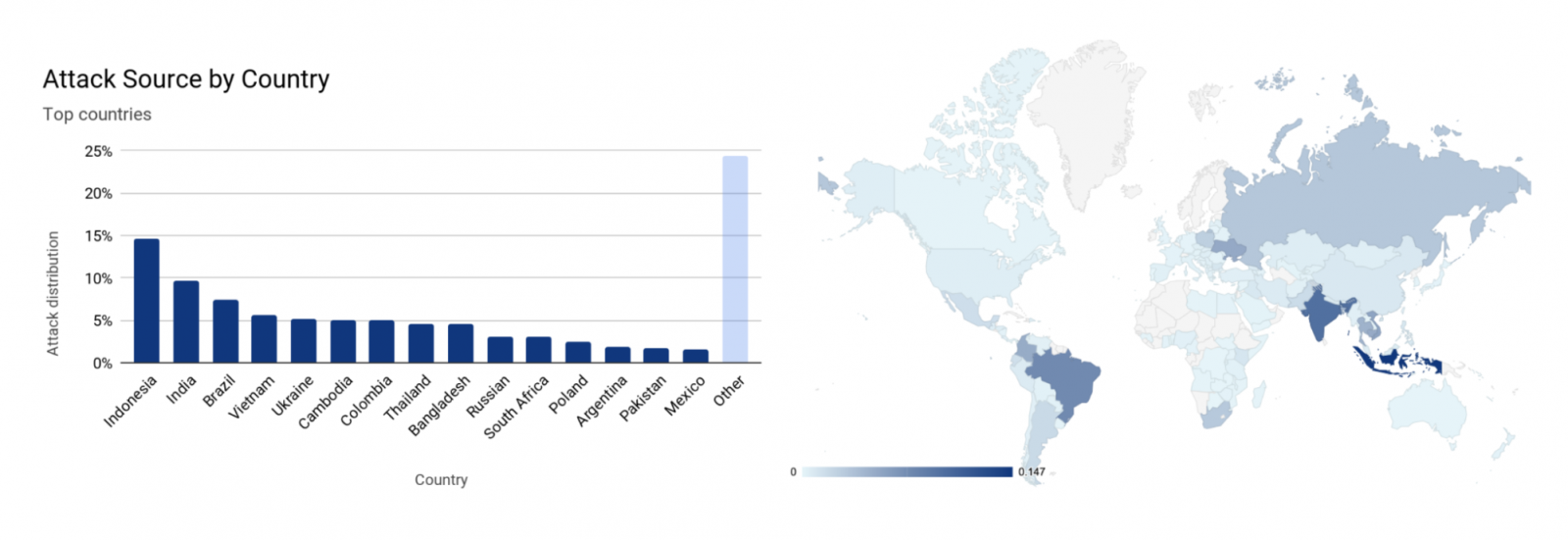
Cloudflare says that the attacker leveraged a botnet of at least 20,000 devices from all over the world. Most of the IP addresses generating the attack traffic were in Indonesia (15%), followed by India and Brazil (17% combined).
Omer Yoachimik, product manager for Cloudflare's DDoS Protection Service, says that this HTTP DDoS attack that Cloudflare mitigated is “almost three times larger than any previous one that we're aware of.”
To paint a better picture of the magnitude of the assault, Cloudflare’s typical serving load is above 25 million HTTP requests every second. At its strongest, the July DDoS attack reached 68% of that capacity.
Yoachimik says that the botnet behind the attack just last week has also targeted a hosting provider with the same type of attack but its peak was below eight million requests per second.
Other notable DDoS attacks that Cloudflare detected and thwarted came from a Mirai-based botnet that showed more than once it could send more than one terabyte of bad traffic every second.
At its strongest, the botnet delivered close to 1.2Tbps of junk traffic, some of the targets being a major internet, telecommunications, and hosting provider in the APAC region, and a gaming company.
“The Mirai botnet started with roughly 30K bots and slowly shrinked to approximately 28K. However, despite losing bots from its fleet, the botnet was still able to generate impressive volumes of attack traffic for short periods. In some cases, each burst lasted only a few seconds” - Cloudflare
Mirai was discovered in 2016 and its source code was released to the public after the devastating attacks on the website of investigative reporter Brian Krebs, the infrastructure of French host provider OVH, and of global DNS provider Dyn.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·