iblessing
iblessing is an iOS security exploiting toolkit, it mainly includes application information collection, static analysis and dynamic analysis. iblessing is based on unicorn engine and capstone engine. Cross-platform: Tested on macOS and Ubuntu.iOS App static info extract, including metadata, deeplinks, urls, etc.
Mach-O parser and dyld symbol bind simulator
Objective-C class realizing and parsing
Scanners making dynamic analysis for arm64 assembly code and find key information or attack surface
Scanners using unicorn to partially simulate Mach-O arm64 code execution and find some features
Generators that can provide secondary processing on scanner's report to start a query server, or generate script for IDA
Super objc_msgSend Xrefs Scanner
objc method and subs (such as block) emulation to generate xrefs like flare-emu objc function wrapper detect and ida usercall generate objc_msgSend sub functions analysis objc block to objc_msgSend xrefs in args and capture list report format including json, etc. Diagnostic logs
Tests
More flexible scanner infrastructure for new scanner plugins
Swift class and method parsing
More scanners and generators
Cross-platform
Support
unicorn may crash (segment fault or bus error) on some computers, I am trying to solve this problem. If you encounter any problems, you can contact me, thank you
In case you need support regarding iblessing or anything associated with it, you can:
Changelog
2020.08.11 - Now iblessing is a cross-platform tool, support both macOS and Linux 2020.08.08 - Improve objc_msgSend xref scanner, add sub xref supoort, including block arguments and capture list 2020.07.30 - Improve symbol-wrapper scanner, and add ida scripts for symbol wrapper rename and prototype modification 2020.07.21 - First releaseGet started
Sometimes unicorn will crash on start when doing huge memory mapping, you can try to run it again, if it still can't work, please contact me or create an issue, thanks.
How to Build
CMake
Platform: macOS, LinuxTo get started compiling iblessing, please follow the steps below:
git clone --recursive -j4 https://github.com/Soulghost/iblessing cd iblessing ./compile-cmake.shXcodeBuild
Platform: macOSTo get started compiling iblessing, please follow the steps below:
git clone --recursive -j4 https://github.com/Soulghost/iblessing cd iblessing ./compile.shShortcuts
Basic ConceptsScanners
Scan for AppInfos Scan for Class XREFs Scan for All objc_msgSend XREFs Scan for Simple Symbol Wrappers Generators
Generate objc_msgSend Xrefs Query Server Generate IDA Scripts for objc_msgSend xrefs Generate IDA Scripts for objc function wrapper rename and prototype modification
If there are any errors, you can manully compile capstone and unicorn, then drag libcapstone.a and libunicorn.a to the Xcode project's vendor/libs.
If all of this run successfully, you can find the binary in build directory:
Documentation & Help
Preview
$ iblessing -h ☠️ ██╗██████╗ ██╗ ███████╗███████╗███████╗██╗███╗ ██╗ ██████╗ ██║██╔══██╗██║ ██╔════╝██╔════╝██╔════╝██║████╗ ██║██╔════╝ ██║██████╔╝██║ █████╗ ███████╗███████╗██║██╔██╗ ██║██║ ███╗ ██║██╔══██╗██║ ██╔══╝ ╚════██║╚════██║██║██║╚██╗██║██║ ██║ ██║██████╔╝███████╗███████╗███████║███████║██║██║ ╚████║╚██████╔╝ ╚═╝╚═════╝ ╚══════╝╚══════╝╚══════╝╚══════╝╚═╝╚═╝ ╚═══╝ ╚═════╝ [***] iblessing iOS Security Exploiting Toolkit Beta 0.1.1 (http://blog.asm.im) [***] Author: Soulghost (高级页面仔) @ (https://github.com/Soulghost) Usage: iblessing [options...] Options: -m, --mode mode selection: * scan: use scanner * generator: use generator -i, --identifier choose module by identifier: * <scanner-id>: use specific scanner * <generator-id>: use specific generator -f, --file input file path -o, --output output file path -l, --list list available scanners -d, --data extra data -h, --help Shows this pageBasic Concepts
Scanner
A scanner is a component used to output analysis report through static and dynamic analysis of binary files, for example, the objc-msg-xref scanner can dynamiclly analyze most objc_msgSend cross references.
Generator
A generator is a component that performs secondary processing on the report generated by the scanner, for example, it can generate IDA scripts based on the the objc-msg-xref scanner's cross references report.
Basic Usage
Scan for AppInfos
> iblessing -m scan -i app-info -f <path-to-app-bundle>Let's take WeChat as an example:
> iblessing -m scan -i app-info -f WeChat.app [*] set output path to /opt/one-btn/tmp/apps/WeChat/Payload [*] input file is WeChat.app [*] start App Info Scanner [+] find default plist file Info.plist! [*] find version info: Name: 微信(WeChat) Version: 7.0.14(18E226) ExecutableName: WeChat [*] Bundle Identifier: com.tencent.xin [*] the app allows HTTP requests **without** exception domains! [+] find app deeplinks |-- wechat:// |-- weixin:// |-- fb290293790992170:// |-- weixinapp:// |-- prefs:// |-- wexinVideoAPI:// |-- QQ41C152CF:// |-- wx703:// |-- weixinULAPI:// [*] find app callout whitelist |-- qqnews:// |-- weixinbeta:// |-- qqnewshd:// |-- qqmail:// |-- whatsapp:// |-- wxwork:// |-- wxworklocal:// |-- wxcphonebook:// |-- mttbrowser:// |-- mqqapi:// |-- mqzonev2:// |-- qqmusic:// |-- tenvideo2:// ... [+] find 507403 string literals in binary [*] process with string literals, this maybe take some time [+] find self deeplinks URLs: |-- weixin://opennativeurl/devicerankview |-- weixin://dl/offlinepay/?appid=%@ |-- weixin://opennativeurl/rankmyhomepage ... [+] find other deeplinks URLs: |-- wxpay://f2f/f2fdetail |-- file://%@?lang=%@&fontRatio=%.2f&scene=%u&version=%u&type=%llu&%@=%d&qqFaceFolderPath=%@&platform=iOS&netType=%@&query=%@&searchId=%@&isHomePage=%d&isWeAppMore=%d&subType=%u&extParams=%@&%@=%@&%@=%@ ... [*] write report to path /opt/one-btn/tmp/apps/WeChat/Payload/WeChat.app_info.iblessing.txt > ls -alh [email protected] 1 soulghost wheel 29K Jul 23 14:01 WeChat.app_info.iblessing.txtScan for Class XREFs
Notice: ARM64 Binaries Only
Scan for All objc_msgSend XREFs
Notice: ARM64 Binaries Only
Simple Mode
iblessing -m scan -i objc-msg-xref -f <path-to-binary>Anti-Wrapper Mode
iblessing -m scan -i objc-msg-xref -f WeChat -d 'antiWrapper=1'The anti-wrapper mode will detect objc_msgSend wrappers and make transforms, such as:
; __int64 __usercall [email protected]<X0>(void *[email protected]<X0>, const char *[email protected]<X22>, id [email protected]<X20>, ...) objc_msgSend_X0_X22_X20: MOV X1, X22 MOV X2, X20 B objc_msgSendUsage Example:
; __int64 __usercall [email protected]<X0>(void *[email protected]<X0>, const char *[email protected]<X22>, id [email protected]<X20>, ...) objc_msgSend_X0_X22_X20: MOV X1, X22 MOV X2, X20 B objc_msgSendThe report can be used by the generators, now let's go.
Generate objc_msgSend Xrefs Query Server
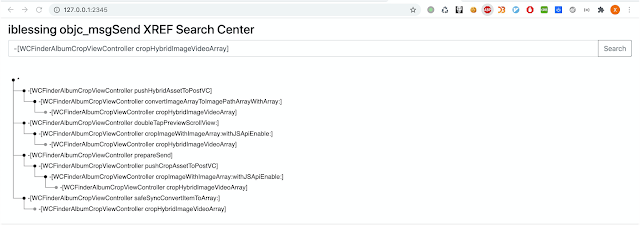
You can start a server through iblessing's objc-msg-xref-server generator to query all objc_msgSend xrefs.
Specify the Listening Host and Port
The default listening address is 127.0.0.1:2345, you can specify it by -d option.
Usage Example
Notice: the objc-msg-xref is based on unicorn, to speed up the analyze, we do not follow any calls, so the result is partially missing.
Next you can open http://127.0.0.1:2345 with a browser to query any objc_msgSend xrefs you like:
Generate IDA Scripts for objc_msgSend xrefs
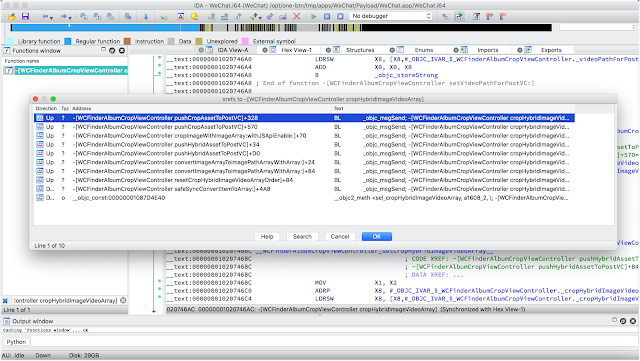
You can add objc_msgSend xrefs generated from objc-msg-xref scanner to make your reverse engineering journey more faster and comfortable.
Usage Example
Notice: the objc-msg-xref is based on unicorn, to speed up the analyze, we do not follow any calls, so the result is partially missing.
Next open your IDA -> File -> Script File and load the script, this step may take a long time. And when it is done, you can find many xrefs for objc method:
Scan for symbol wrappers
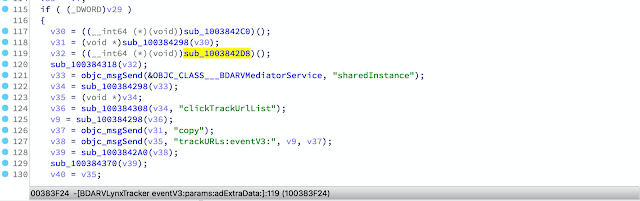
A Mach-O file may contain multiple wrappers of commonly used dynamic library imported symbols, such as:
We can convert the wrapper by usercall:
__text:00000001003842CC ; id __usercall [email protected]<X0>([email protected]<X23>, const char *@<X28>, ...) __text:00000001003842CC _objc_msgSend_61 ; CODE XREF: -[BDARVLynxTracker eventV3:params:adExtraData:]+2CC↑p __text:00000001003842CC ; -[BDARVLynxTracker eventV3:params:adExtraData:]+320↑p ... __text:00000001003842CC MOV X0, X23 __text:00000001003842D0 MOV X1, X28 __text:00000001003842D4 B objc_msgSendThe scanner can generate a report to record all wrappers, then you can use ida-symbol-wrapper-naming generator to generate ida scripts and implement this wrapper rename and prototype change.
How to Use
> iblessing -m generator -i ida-objc-msg-xref -f WeChat_method-xrefs.iblessing.txt [*] set output path to /opt/one-btn/tmp/apps/WeChat/Payload [*] input file is WeChat_method-xrefs.iblessing.txt [*] start IDAObjMsgXREFGenerator [*] load method-chain db for version iblessing methodchains,ver:0.2; [*] table keys chainId,sel,prefix,className,methodName,prevMethods,nextMethods [-] bad line 104467,0x0,+[TPLock P, ],+,TPLock,P, ,[104426#0x1043b9904],[] [-] bad line 114905,0x0,?[0x108ce1578 (,],?,0x108ce1578,(,,[114900#0x1011e8c68],[] [-] bad line 104464,0x0,?[? P, ],?,?,P, ,[104426#0x1043b98a8],[] [-] bad line 139234,0x0,?[? X [-] bad line ],?,?,X [-] bad line ,[139205#0x1013c222c],[] [+] load storage from disk succeeded! [*] Generating XREF Scripts ... [*] saved to /opt/one-btn/tmp/apps/WeChat/Payload/WeChat_method-xrefs.iblessing.txt_ida_objc_msg_xrefs.iblessing.py > ls -alh WeChat_method- xrefs.iblessing.txt_ida_objc_msg_xrefs.iblessing.py -rw-r--r-- 1 soulghost wheel 23M Jul 23 16:16 WeChat_method-xrefs.iblessing.txt_ida_objc_msg_xrefs.iblessing.py > head WeChat_method-xrefs.iblessing.txt_ida_objc_msg_xrefs.iblessing.py def add_objc_xrefs(): ida_xref.add_cref(0x10036367c, 0x1008c2220, XREF_USER) ida_xref.add_cref(0x1003636e8, 0x1008c3df8, XREF_USER) ida_xref.add_cref(0x10036380c, 0x1008c27e8, XREF_USER) ida_xref.add_cref(0x103add16c, 0x700006e187a8, XREF_USER) ida_xref.add_cref(0x102cbee0c, 0x101143ee8, XREF_USER) ida_xref.add_cref(0x10085c92c, 0x1005e9360, XREF_USER) ida_xref.add_cref(0x10085c8bc, 0x1005e9274, XREF_USER) ida_xref.add_cref(0x10085c8dc, 0x1005e92bc, XREF_USER) ida_xref.add_cref(0x10085c8cc, 0x1005e9298, XREF_USER)Usage Example
We will take TikTok China as an example:
Next, we can generate ida scripts from this report.
Genereate IDA Script for Objc Runtime Function Rename and Prototype Modification
__text:00000001003842CC ; id __usercall [email protected]<X0>([email protected]<X23>, const char *@<X28>, ...) __text:00000001003842CC _objc_msgSend_61 ; CODE XREF: -[BDARVLynxTracker eventV3:params:adExtraData:]+2CC↑p __text:00000001003842CC ; -[BDARVLynxTracker eventV3:params:adExtraData:]+320↑p ... __text:00000001003842CC MOV X0, X23 __text:00000001003842D0 MOV X1, X28 __text:00000001003842D4 B objc_msgSendUsage Example
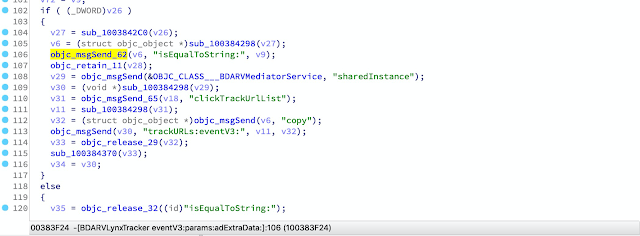
iblessing -m scan -i symbol-wrapper -f <path-to-binary> -d 'symbols=_objc_msgSend,_objc_retain,_objc_release' iblessing -m scan -i symbol-wrapper -f <path-to-binary> -d 'symbols=*'Next open your IDA -> File -> Script File and load the script, this step may take a long time. And when it is done, You can observe some decompiled code changes:
.png)
 4 years ago
191
4 years ago
191 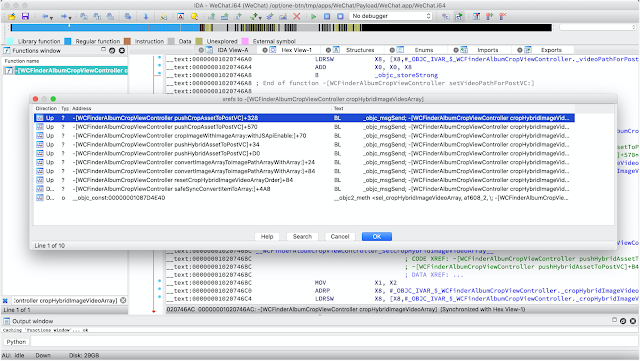
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·