A tool to test security of JSON Web Tokens. Test a JWT against all known CVEs;
Tamper with the token payload: changes claims and subclaims values. Exploit known vulnerable header claims (kid, jku, x5u) Verify a token Retrieve the public key of your target's ssl connection and try to use it in a key confusion attack with one option only All JWAs supported Generates a JWK and insert it in the token header And much, much more!Wiki
Read the wiki! wikiInstallation
N.B. Cloning the repository should be avoided except for development purposes! N.B. Deb package has to be considered beta
With rpm:
sudo rpm --install jwtxploiter-1.2.1-1.noarch.rpm
or, if previous version is installed on your machine
With pip:
With deb:
sudo dpkg -i jwtxploiter_1.2.1-1_all.deb
Cloing the repo:
./install.sh
N.B. python3-pip package is required to install dependencies, be sure to have it installed.
Who this tool is written for?
Web Application Penetration Tester / Bug Bounty Hunters
This tool has been written with the aim of become a key part of pentesters toolkit.Devs who need to test the secuirty of JWTs used in their applications
CTF Players
Not For Students
Since this tool automates lot of stuff, without force the user to know what's happening under the hood, it won't help you to understand the vulnerabilities it exploits.To Know
For attacks that generates a jwks file, you could find it in the current working directory. Remeber to deletes such files in order to avoid conflicts.
For jku/x5u injection that needs to merge two urls (the server vulnerable url and your one), the HERE keyword is required.
For redirect attacks the keyword should replace the redirect url, e.g.
http://app.com/foo?redirect=bar&some=thing --> http://app.com/foo?redirect=HERE&some=thingFor jku/x5u injections via HTTP header injection attacks, the HERE keyword sould be appended to the vulnerable parameter, without replacing its value, e.g.
http://app.com/foo?param=value --> http://app.com/foo?param=valueHEREAlso, in such cases, be sure to pass the server url and your one as comma separated values.
'/.well-known/jwks.json' is automatically appended to your url in jku/x5u attacks. So make sure to place the jwks file under this path on your server.
If you don't want that happen, use the --manual option, but this option is compatible only with --jku-basic and --x5u-basic so, you will need to manually craft the url and pass it to those options, even for attacks that exploit Open Redirect or HTTP header injection.
Look at the wiki for a detailed documentation.
.png)
 3 years ago
203
3 years ago
203 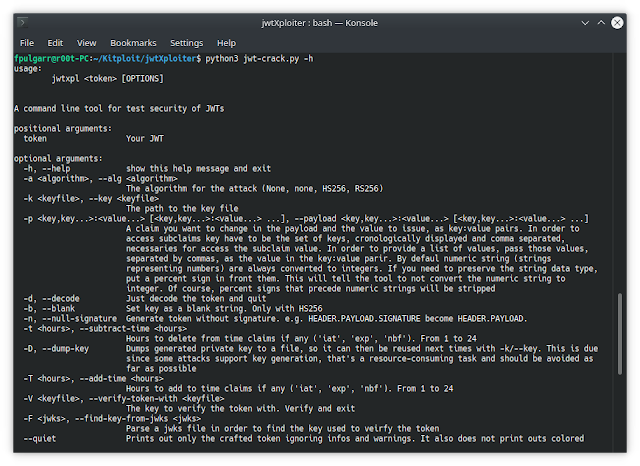















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·