BOOK THIS SPACE FOR AD
ARTICLE ADResearchers with D3Lab have discovered the data of almost one million credit card holders being sold on an underground forum, according to a blog post released this week.
In a sample of 980,930 files acquired by D3Lab analysts on Monday, the batch contained names, addresses, credit card numbers, expirations and CVVs.
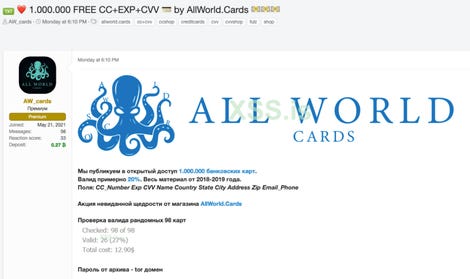
About 30,000 entries in the data set came from people living in Italy, based on identifications tied to the stolen cards. D3Lab analysts found the information on a carding database called All World Cards.
 D3Lab
D3Lab
All World Cards is a haven for online credit card thieves involved in things like magecart attacks, information stealing malware and point-of-sale attacks.
D3Lab noted in their report that carding sites generally get most of their stolen credit cards from point-of-sale attacks at gas stations, supermarkets and some e-commerce sites.
The report found that the people behind All World Cards have been marketing their site and services since June and may have purchased stolen credit card data and shared it for free "to entice other criminal actors to frequent their site."
The domain for allworld [.] Cards was created in May and the site now has 2,634,615 stolen credit cards, with more than 1 million coming from the US.
After examining the data, D3Lab researchers sent the information to the banks represented in the leak so that the cards could be cancelled and users could be notified.
Half of the cards in the batch are still operational, according to D3Lab.
With the help of a BIN database, the researchers managed to verify the stolen records and figure out the companies, issuers and other data on the victims.
Of the 980,930 stolen cards, 98% had a valid BIN associated with an emitter, according to D3Lab, while nearly every card came from either Visa or Mastercard.
More than 75% of the cards were debit cards and 24% were Gold, Business or Titanium cards.
India was the most represented country in the batch, with 20% of cards coming from the country followed by Mexico and the US with 9%. About 4% came from Italy as well.
Javvad Malik, security awareness advocate at KnowBe4, told ZDNet that the cards were stolen between 2018 and 2019, making it difficult to determine where the data came from or if it came from multiple sources.
Carding has become a lucrative avenue for cybercriminals, explained PerimeterX senior director Uriel Maimon. Attackers use bots to test lists of recently stolen credit card and debit card details on merchant sites.
The carders then use the proven credit card details to directly retrieve funds from associated accounts or to purchase gift cards which can easily be converted into high-value goods, such as cell phones, televisions and computers, Maimon explained.
"These goods are then resold -- often via ecommerce sites offering a degree of anonymity -- for a profit. As these cards were stolen between 2018-2019, it stands to reason that most are no longer valid, especially if they're publicly dumped and multiple actors will jump on them at the same time."
In December 2020, the FBI and Interpol seized four domains operated by Joker's Stash, the internet's largest marketplace for buying and selling stolen card data. The site announced it was officially shutting down in February.
BleepingComputer noted that cybersecurity company Cyble imported the stolen data into their AmIBreached service, so people can check if their credit card information was involved.
.png)
 3 years ago
193
3 years ago
193 














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·