BOOK THIS SPACE FOR AD
ARTICLE AD
QNAP urges its users to update the Malware Remover app and bolster their NAS devices' security following a QSnatch malware joint alert published earlier this week by UK's NCSC and the US CISA government cybersecurity agencies.
While QNAP made it a point out of asking customers to reinforce their devices' security, the Taiwanese vendor also contradicted reports mentioning an increase in the number of NAS devices infected since October 2019.
"Certain media reports claiming that the affected device count has increased from 7,000 to 62,000 since October 2019 are inaccurate due to a misinterpretation of reports from different authorities," QNAP said.
However, as the CISA and NCSC joint alert says, around 62,000 QNAP NAS devices were found to be infected with QSnatch malware worldwide in mid-June 2020 — of which 7,600 were found in the US and 3,900 in the UK — after attacks targeting them from early 2014 to mid-2017 and from late 2018 to late 2019.
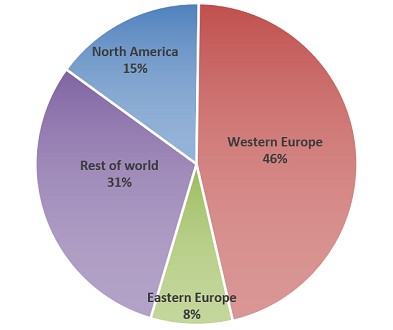 Infected QNAP NAS devices by region (CISA/NCSC)
Infected QNAP NAS devices by region (CISA/NCSC)The joint alert also says that all QNAP NAS devices are potentially vulnerable to attacks using QSnatch malware if their software is not up to date.
"Organizations that are still running a vulnerable version must run a full factory reset on the device prior to completing the firmware upgrade to ensure the device is not left vulnerable," the joint alert warned.
QSnatch malware capabilities
Once it infects a QNAP NAS device, QSnatch gains persistence by editing cronjob and init scripts to block any software updates, and it also prevents the Malware Remover app from running.
Even though the infection vector used by the malware is unknown, the joint alert issued on Monday says that some QSnatch samples will "intentionally patch the infected QNAP for Samba remote code execution vulnerability CVE-2017-7494."
QSnatch has a large assortment of features implemented as modules including but not limited to:
• a CGI password logger: installs a fake device admin login page for phishing credentials
• a credential scrapper
• an SSH backdoor: enables the attackers to run arbitrary code on infected devices
• a web shell: provides malware's operators with remote access to compromised NAS devices
• a data theft module: steals a pre-defined list of files (including logs and system configuration) and sends them in encrypted form to attacker-controlled servers
Users urged to secure QNAP devices
Right now, the attack infrastructure behind the previous QSnatch attacks is down, but users are urged by both QNAP and the two agencies to update their NAS devices as soon as possible to block future attacks.
"Users are urged to install the latest version of the Malware Remover app from the QTS App Center or by manual downloading from the QNAP website," QNAP said today. "QNAP also recommends a series of actions for enhancing QNAP NAS security."
These are some of the measures recommended by QNAP to secure NAS devices targeted by QSnatch:
Update QTS and Malware Remover to the latest version. Install and update Security Counselor to the latest version. Change and use a stronger admin password. Enable IP and account access protection to prevent brute force attacks. Disable SSH and Telnet connections if you are not using these services. Avoid using default port numbers 443 and 8080.Below you can find a timeline of all actions taken by QNAP since the first QSnatch malware report:
| Date | Event and reaction |
| October 25, 2019 | Notifications from authorities of Finland and Germany |
| November 1, 2019 | QNAP released the updated Malware Remover for detecting and removing QSnatch |
| November 2, 2019 | QNAP published the updated security advisory for QSnatch |
| November 7, 2019 | QNAP released a Press Release to inform the public |
| November 2019 to January 2020 | QNAP updated the security advisory multiple times to keep the public informed |
| February 2020 to June 2020 | QNAP emailed possibly affected users to recommend an immediate update |
| July 31, 2020 | QNAP released another Press Release to reassure the public |
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·