BOOK THIS SPACE FOR AD
ARTICLE ADA Russian-speaking group called RedCurl is running one of the most well-organized espionage campaigns for years to steal trade secrets and personal data of employees.
A cybersecurity firm Group-IB released a startling new report on a sophisticated hacker group called RedCurl. According to researchers who have been focusing on this group since 2019, the hackers specialize in corporate espionage.
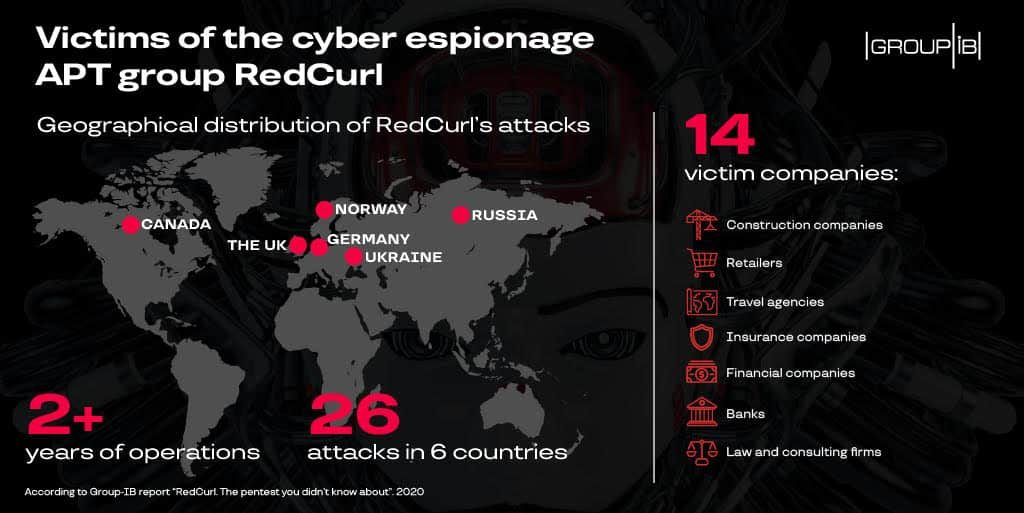
So far, RedCurl has targeted companies worldwide and has stolen commercial secrets as well as employees’ private data. Since 2018, as per Group-IB’s report, RedCurl has launched 26 different campaigns against 14 private sector organizations around the world and stole vast reserves of data.
The documents stolen by RedCurl include contracts, employee records, financial documents, and legal records. Moreover, the group targeted a wide range of industries, including finance, construction, law, and retail. Most of its targets have attacked companies in Russian, UK, Ukraine, Canada, Norway, and Germany.
Researchers have observed many similarities between hacking techniques of RedCurl and other groups, such as CloudAtlas and RedOctober. These groups are also known for attacking Russia-based government networks and organizations. It is quite possible that RedCurl is a continuation of the previous attacks, claims Group-IB researchers.
However, the researchers couldn’t identify where RedCurl is based, and just that the hackers speak in the Russian language doesn’t mean that they might be based in Russia.
Another point to note is that Russian hackers usually don’t target firms or institutions within Russia to avoid provoking the country’s intelligence agencies. RedCurl hackers, however, doesn’t hesitate to attack a Russian organization.
Researchers identified that RedCurl hackers impersonate the HR staff of their target organization, and send out emails promising employee bonuses to several workers in the same department. Through this tactic, the group manages to lower their defenses. Then it sends a phishing email to the HR department, which infects the systems.
Afterward, the group launches the attack formally to steal data. It exploits Microsoft PowerShell to infect the device with malicious software scripts and keep exploiting the breached network for at least 2 to 6 months. During this time, they steal confidential data such as usernames and passwords and employ different methods to evade detection.
In an email to Hackread.com, Group-IB’s head of malware dynamic analysis team, Rustam Mirkasymov, stated that:
“Such groups focus on corporate espionage and employ various techniques to cover their activity, including the use of legitimate tools that are difficult to detect.”
Moreover, the groups never use complex hacking techniques or tools to carry out corporate espionage, and mainly rely on spear-phishing to gain initial access to the system. They carefully craft the contents of the email, such as they use the target company’s genuine logo and address, and the sender’s address features the company’s domain name.
This is how they make their emails appear legit. The emails contain malware-infected files embedded with Power-Shell-based trojans, which, if downloaded by the victim, can infect the system.
If possible, RedCurl hackers also access network shared devices and replace original files with boobytrapped LNK files. If executed, these files can corrupt other systems as well.
Interestingly, RedCurl uses the WebDav protocol as its chief exfiltration channel, which RedOctober and CloudAtlas also use. However, researchers didn’t identify any major similarities between the three hacking groups and believe that these are separate groups. For in-depth technical details, you can download Group-IB’s report here.
Did you enjoy reading this article? Do like our page on Facebook and follow us on Twitter.
.png)













 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·