BOOK THIS SPACE FOR AD
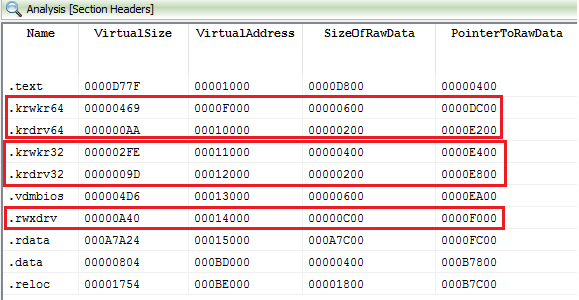
ARTICLE ADThe dropper also contains one more driver (and its x64 clone) that is also interesting for research. I should make one clarification about information I posted before. The dropper itself doesn't contain rootkit driver as whole file inside, instead it stores only its PE-sections. This means that rootkit PE-file is generated by dropper on-the-fly. So, aswfilt.dll and 32-bit code of another driver as well as its 64-bit clone are stored only as PE-sections. And this is answer on question, why aswfilt.dll has one unnamed section and zeroed timestamp in PE-header. On screenshot below, you can see how the dropper initializes PE-header of aswfilt.dll driver before it was written to FS as executable file.
Driver (Ring 0 code) has following properties:
It has compact size and its code is stored into two PE sections inside dropper.It has dynamic imports that are stored into special context structure.It has 64-bit clone inside the dropper.It has no DriverEntry function.It serves for one purpose: execute code from ptr that was passed from user mode to FastIoDeviceControl handler.It uses undocumented Windows kernel API.Code and data of aswfilt.dll driver are stored into a separate section with name ".rwxdrv", as you can see on screenshot below. Another two sections with names ".krwkr32", ".krdrv32" and ".krwkr64", ".krdrv64" are used for storing mentioned above 32-bit Ring 0 code and its x64 analog.
Like aswfilt.dll, kernel mode code from above mentioned sections uses special context structure where dynamically loaded imports are located. Format of this structure you can see below.
struct RootkitStruct {
PVOID pExAllocatePool;
PVOID pExFreePool;
PVOID pExQueueWorkItem;
PVOID pIofCompleteRequest;
PVOID pIoCreateDevice;
PVOID pIoDeleteDevice;
PVOID pIoDriverObjectType;
PVOID pIoGetCurrentProcess;
PVOID pKeInitializeEvent;
PVOID pKeSetEvent;
PVOID pKeStackAttachProcess;
PVOID pKeUnstackDetachProcess;
PVOID pKeWaitForSingleObject;
PVOID pObCreateObject;
PVOID pObInsertObject;
PVOID pObQueryNameString;
PVOID pObfDereferenceObject;
PVOID pZwClose;
PVOID pZwCreateFile;
PVOID pBuffer;
ULONG cbBuffer;
ULONG field1;
PVOID pProcessForAttach;
};
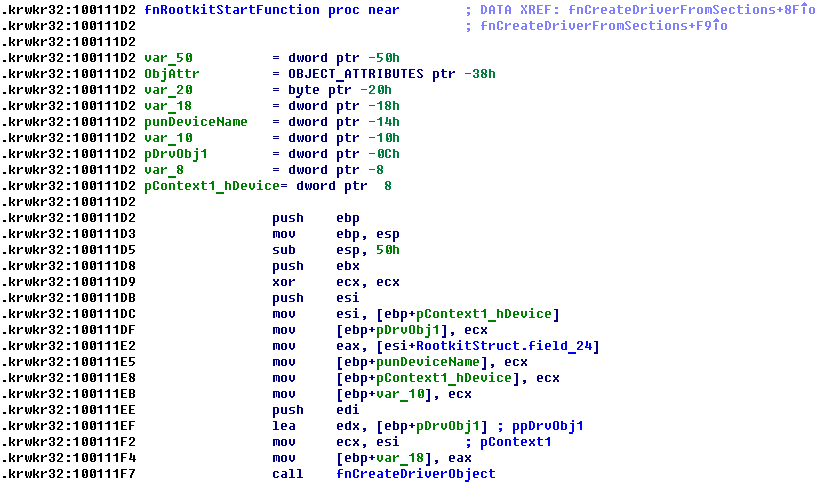
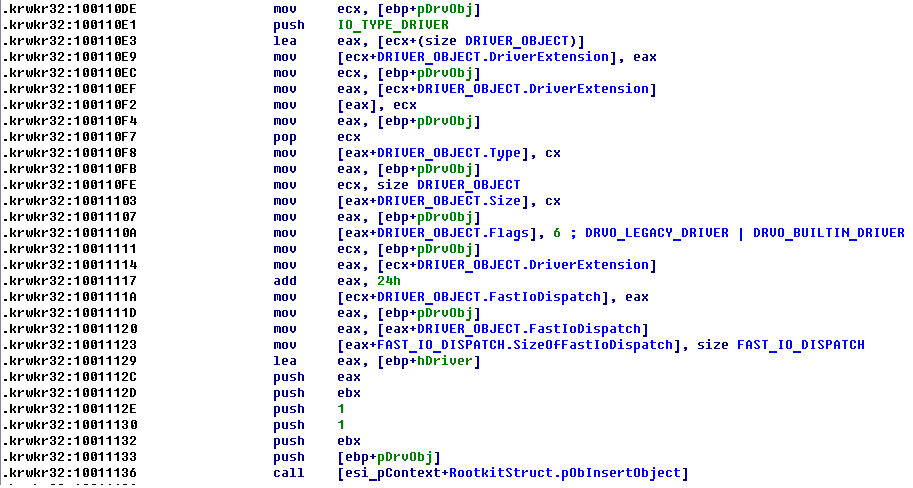
First action, which fnRootkitStartFunction does, it is creating driver object for loaded Ring 0 code (fnCreateDriverObject). This function (fnCreateDriverObject) allocates an object in memory with help of ObCreateObject, initializes it and does it visible for Windows kernel by inserting it into objects list with ObInsertObject.
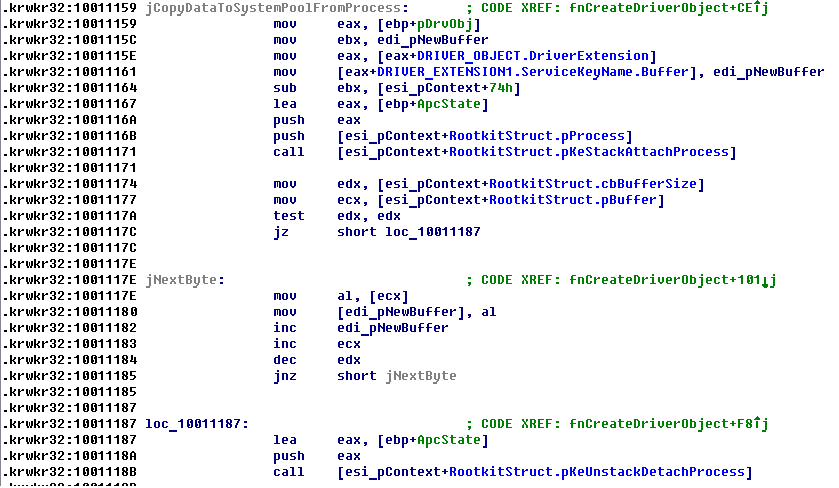
Next, it does copying of prepared data with already initialized ptr from user mode buffer to system buffer and saves ptr to it into DriverExtension->ServiceKeyName.Buffer.
The driver leverages interesting way for dispatching DeviceControl request. Unlike other drivers that are using IRP_MJ_DEVICE_CONTROL handler in such case, it registers FastIo function DriverObject->FastIoDispatch.FastIoDeviceControl.
As we already saw in case of aswfilt.dll, DeviceControl handler is responsible for performing only one task: execute function by ptr that has been passed to it from user mode client.
Unfortunately, I haven't a lot of free time for reconstructing logic of Ring 3 code (dropper part) and how it forms context for kernel mode code. I know that IOCTL with code 0x839200BF (Rootkits_IOCTLs_ExecuteFunction) is used by the dropper only one time in function fnSendIOCTL_839200BF. It passes to driver ptr to function that located at address 0x1000741A.
The dropper also contains some code for exploiting NT Virtual DOS Machine (NTVDM), it contains section with name .vdmbios and it imports function NtVdmControl. The code also uses context structre for calling dynamic imports.
.png)



















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·